Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
Dark clouds on the security horizon – Azure accounts compromised

Over the past few months, InfoGuard's CSIRT has been working on various cyber incidents in the Azure environment, primarily focusing on what is known as “Business E-Mail Compromise”. Read more in the current blog article by Stephan Berger, Senior Cyber Security Analyst at InfoGuard.
What is Business E-Mail Compromise?
When compromising a business e-mail account, the first thing an attacker does is to gain access to the company's e-mail account. In previous years, this path could be principally accessed via the OWA (Outlook Web Access) interface, which gave employees the option of accessing company e-mail while travelling. With many services including Exchange Online being outsourced to the Microsoft cloud, attackers have once again been given new opportunities to compromise corporate accounts and in, this way, to gain access to the compromised user's email accounts.
In a few cases, the attackers send phishing messages from the compromised mail account to various e-mail addresses as if they were coming from the compromised user. However, most of the time the attackers are patient and keep an eye on the conversations (i.e. incoming and outgoing e-mails) in the inbox for months, just waiting for an opportunity to join a legitimate e-mail conversation. The attackers' ultimate goal is financial gain by forging legitimate invoices or altering account numbers for a bank transfer. These frauds are often done using newly registered domains that are deceptively similar to the compromised e-mail address.
The Real Life Case from CSIRT
The following real-life case clearly shows how attackers proceed in a business e-mail compromise. In a mailbox compromise carried out this year, the attackers had already been intercepting the communication for weeks, as could be seen from the existing records of the logins. Figure 1 shows an original e-mail with an attached PDF invoice from the compromised user.
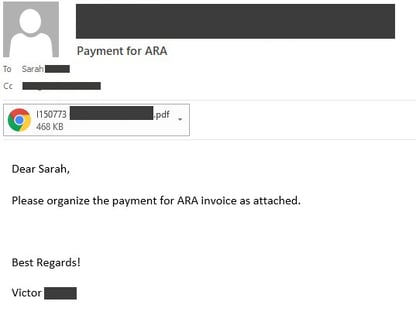
Figure 1: Original e-mail with the invoice attachment
Figure 2 shows the original invoice with the Australian bank's account details highlighted in red.
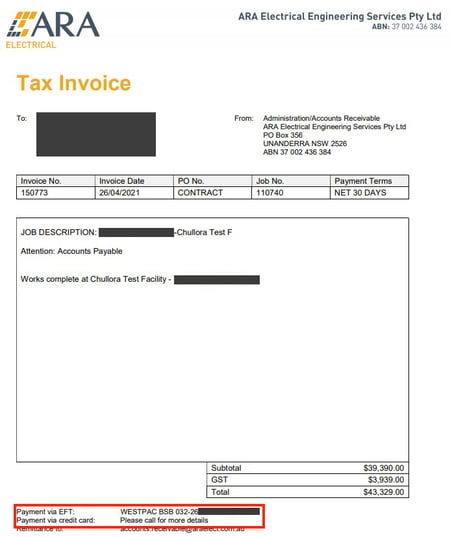
Figure 2: Original invoice
One day after the first e-mail, the attacker sent the e-mail in Figure 3, stating that the invoice sent yesterday should be ignored and the newly attached invoice should be used to make the payment.
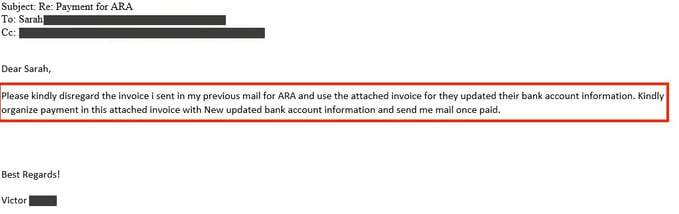
Figure 3: Hacker’s e-mail with a new invoice
Figure 4 shows the fake invoice, which looks exactly the same as the first one. Only the name of the bank and the account number have been changed.

Figure 4: Fake invoice with modified account details
Analysis of the forged PDF file showed that most likely, the attacker took a screenshot of the real invoice, modified it in an image editing programme and then created a PDF based on the image. This was shown by analysing the fake invoice's metadata. Only two tools are needed to do this:
- Creator: 3-Heights(TM) Image to PDF Converter 5.9.1.5
- Producer: 3-Heights(TM) Image to PDF Converter Shell 5.9.1.5
How do I spot a compromised Azure account?
A simple, fairly reliable way of identifying compromised Azure accounts is offered by Microsoft's “Risky Sign-Ins”. After being authenticated at the corresponding Azure tenant, the report can be viewed using the path: Azure Active Directory - Security - Risky Sign-Ins. You can see a sample of this potentially risky user login in Figure 5.
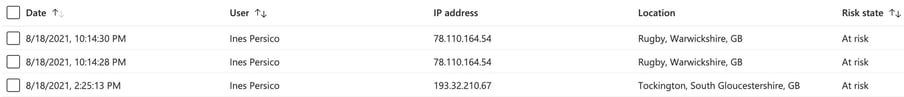
Figure 5: Risky sign-ins section with logins from England
As well as this, depending on the licence, Azure records the user's log-in data for a shorter or longer time period (the path is Azure Active Directory - Sign-In Logs). These “sign-in logs” can be easily searched using filters via the web GUI, and can also provide clues about a compromise. A useful starting point is to review logins from foreign countries where the company has no branches or subsidiaries.
Newly created e-mail rules
Once an account or mailbox has been compromised, attackers often install additional mailbox rules that search incoming e-mails according to certain criteria. For example, in several cases, InfoGuard has discovered a rule that searches incoming e-mails for various keywords like “Invoice”, “IBAN” and “Account”. These mailbox rules will automatically move the e-mails to the spam folder, giving the attackers enough time to get into the (legitimate) mail conversation.
But watch out! Even after a compromised account has been identified, simply changing the user account's password is not enough. All of the user's active sessions have to be terminated, on top of which further analysis has to be carried out, such as checking the inbox rules described above. However, there are many different ways that an attacker can infiltrate an Azure environment, from adding a new device to the Azure AD to installing an Azure app that would give the attacker full control over the mailbox or Azure account, even after the password has been reset.
Recommendations from our Incident Response Team
Our Incident Response Team recommends the following security measures to increase your security to prevent being compromised:
- Monitoring Risky Sign-Ins: Within the Azure portal, suspicious user sign-ins are logged. We recommend that you analyse the risky sign-ins regularly to detect compromised accounts at an early stage and respond accordingly.
- MFA (Multi-Factor Authentication): By using a second factor (SMS, authenticator app), the impact of a user losing a password (e.g. via phishing or a computer virus) can be alleviated. Even if an attacker were in possession of a valid password for a user account, they would still need to have the user's mobile phone to successfully log in (it is best to use the authenticator app so that the risk associated with SMS is also mitigated). Important: The second factor should be used wherever users can log in (VPN, webmail, etc.) to ensure across-the-board security.
- Typosquatting Monitoring: There are many cases where cyber criminals take over mailboxes to monitor them, especially for new incoming e-mails relating to invoices and account data. The attackers aim to get into the (legitimate) e-mail conversation, e.g. to change the account details of an existing invoice. This scheme is known as “Business E-mail Compromise (BEC)”, as referred to above. To do this, the attackers register a new domain that looks similar to the original mailbox domain.
InfoGuard provides targeted monitoring of customer domains to detect and prevent what is known as a typosquatting attack. If a typosquatting domain of this kind is registered, the customer is informed and can initiate defensive measures on their infrastructure (e.g. blocking the domain on the proxy, refusal of e-mails from this domain, etc.).
Do you suspect that your Azure tenant has been hacked? Our CSIRT incident response experts have specialist expertise in investigating Azure compromises. We would also be pleased to check your Azure tenant for hacked accounts with a Compromise Assessment.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


