InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Two-factor authentication – feel the authentication flow

During the Covid-19 pandemic, remote working is becoming a crucial factor in many companies’ survival. Have you been logging into your company VPN from your home office more and more often over the last few months? This allows employees to access their place of work from any location – from home, while traveling or on the customers' premises; but just how secure is this remote access to your company's network? Usernames and passwords have long since become outdated as the sole means of protecting access. Two-factor authentication (2FA) is standard practice today. Do you use two-factor authentication to protect access to your systems? How does “Airlock”, the Swiss 2FA solution, stand up to the test in everyday use? How is this implemented in the world of work? In this blog article, you will find out all about this topic.
Strong authentication – what does that even mean?
Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) require users to complete two or more separate steps to verify their identity. “Knowledge”, “possession” and “inheritance” are the three characteristics on which multi-factor authentication is based. Two of these three characteristics need to be fulfilled to ensure that authentication is strong:
1. Knowledge: PIN, password, username, answers to security questions
2. Possession: SecurID token, mTAN code, badge, smartphone, credit card
3. Biometrics: fingerprint, iris pattern, vein pattern and voice
When using secure authentication via a web browser, all factors are transmitted to the website from the same entry device (PC, mobile phone, etc.) over an encrypted channel. If attackers manage to gain access to this channel, they are able to get their hands on both factors. Dynamic factors are used to limit this risk. One example of this is popular e-banking. A very secure authentication is provided by the option of hardware keys (possession) in combination with the use of a PIN (knowledge). This works based on the One-Time Password (OTP) method, whereby a new six-digit code is generated for the key every minute, and the code is for single use only.
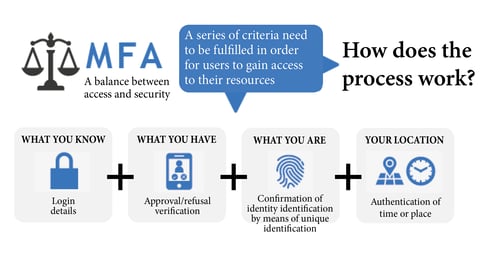 Illustration - Multi-factor authentication
Illustration - Multi-factor authentication
This makes multifactor and two-factor authentication indispensable. But when it comes to implementing a solution of this kind you are bound to ask yourself, which provider is offering the best solution?
Our partner, Ergon Informatik from Switzerland, has created a framework with the security solution called “Airlock Secure Access Hub”. It guarantees that a 2FA project can be implemented successfully and quickly. Airlock 2FA is an authentication solution that fulfills all the expectations of both providers and users. If one of the factors is compromised, the others remain unaffected. The FIDO-framework also offers the option of implementing 2FA and transaction signing. This ensures that there is comprehensive protection against password theft, phishing and social engineering attacks.
Is “better safe than sorry” a competitive advantage?
Let's take a look at three examples from different industries to see how this could work in practice.
2FA in industry
For industry, being networked, user-friendly and able to protect sensitive data creates a conflict between the need for accessibility and the desire to create greater involvement with external partners and customers. But just how secure can it be when industrial machinery is networked via IoT platforms, and customers and partners are able to access machinery and digital customer portals? In this case, identities need to be clearly defined and managed reliably.
Now imagine that a production manager can easily check the status of his CNC machines via an app using “one-touch”. He or she can also change the machine settings with user self-service. However, the manager wants to be certain that only he/she as an authorised employee can access the production processes, and that no untrained personnel is able to gain access to the machine settings. This is an example of why integrated security solutions are in demand in complex industrial environments.
2FA in the world of insurance
Many insurance companies offer a wide range of online services. The insurance industry is a complex one, and this is also true in terms of IT security. Security must be guaranteed when it comes to administering digital patient files, damage reports after an accident or when accessing sensitive pension and pension fund data. Dynamic 2-factor authentication facilitates this in a straightforward way, for example by selecting the “zero touch” or “one touch” option when logging in. By doing so, you get a continuous authentication flow.
2FA in the world of banking
The most common type of 2FA used by banks is still the mTAN method, where customers first enter their username and password (knowledge) before a transaction number (TAN) is sent by text message to their mobile phone (possession). Airlock's authentication methods provide great scope here and, above all, security.
There is no doubt that “zero touch” is the most convenient option. It uses a variety of channels like ambient noise, ultrasound, known Bluetooth devices and Wi-Fi to determine whether the user being identified is indeed in a familiar environment. “one touch”, which is also used in combination with biometric procedures like Touch ID or Face ID, provides a unique identification for users and allows them to carry out their banking transactions with a single touch of the screen. Registration for online banking or approval for a transaction can be carried out quickly and easily using this technology. Of course, customers can also log in and approve a transaction by scanning a QR code.
With Airlock 2FA, security without obstacles
With its two-factor authentication solution, Airlock not only provides you with IT security and compliance. The 2FA solution is integrated into Airlock IAM – a central access management component in the Secure Access Hub – thereby enabling administration and use of the personal key (on smartphones too).
The dynamic authentication concept reacts to different use cases based on risk. This ensures a smooth authentication process because both security requirements and user-friendliness are given equal weight. Airlock 2FA offers a range of authentication tools and methods:
- Zero touch: This variant uses ambient information for an automatic comparison between a smartphone and the browser. You are able to log in without the need for any interaction.
- One touch: You receive a push notification on your smartphone, which you confirm with a single touch – this can also be done in combination with biometric methods like touch ID or facial recognition.
- (Offline) QR code: Registration or authorisation by scanning a QR code can also be done offline. The Airlock 2FA app can be used to do this.
- Passcode: Airlock 2FA automatically generates a new access code every 30 seconds (this is a One-Time Password, OTP for short). You just enter this code to login.
Two-factor authentication means that identities can be authenticated based on specific characteristics. However, the person checking identities also has to manage them and their access authorisations. We recommend Customer Identity & Access Management (cIAM), which is integrated into Airlock's Secure Access Hub. You will be well armed using a 2FA in combination with cIAM, an upstream Web Application Firewall (WAF) and an API Security Gateway. Incidentally, we can also provide the Airlock WAF as a service to provide comprehensive protection for your web applications and portals.
In the whitepaper issued by our partner Airlock, you will find all the important basic information and detailed advice for achieving successful two-factor authentication.
Would you like to discover how Airlock's 2FA solution can be used in your company? Then contact us! Our experienced, certified Airlock specialists will be pleased to advise you. We look forward to hearing back from you!
List of figures:
- Illustration - Multi-factor authentication: https://www.tools4ever.de/was-ist-multi-faktor-authentifizierung
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first

