Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
IEC 62443 – or how to implement OT security in an efficient and reliable way

Digitalisation is affecting all areas of the economy and society. Unfortunately, cyber attacks are now one of the biggest threats posed to trouble-free business operation. Companies are under pressure to guarantee cyber security in OT environments and to create confidence in digital transformation. You can read how to achieve this based on the IEC 62443 standard in this blog article.
There are almost no limits to the potential of digitalisation. Modern information and communication technologies are used to connect industrial manufacturing. Plants, systems and components independently exchange critical data. What is known as “smart factories” boost the productivity of the entire value chain. This is how digital networking is making an important contribution to higher productivity, economic growth and the sustainable, environmentally friendly development of every company.
Digitalisation is changing the risk landscape
However, digitalisation is changing the threat and risk landscape too. Criminals are taking advantage of the fact that not only OT (e.g. production plants, control systems, water and energy supply, production facilities, building management, medical technology, etc.) but also simple everyday objects are increasingly controlled by software and are connected to the Internet. Once attackers have gained access to systems such as these, cyber attacks can be controlled via IoT botnets. According to a recent study, worldwide there were 105 million attempted attacks on IoT devices in the first half of 2019, so it's no surprise that cyber incidents are now one of the biggest threats to businesses.
Merging IT and OT
As a rule, production environments were designed to be an offline, stand-alone solution (Air-Gap). Many companies are now in the process of “modernising” these stand-alone solutions and streamlining them for digital integration. Unfortunately, however, many systems were not primarily designed with cyber security in mind. What’s more, the security principles of traditional IT do not always make it into the development and lifecycle phases of OT systems. We also find time and time again that IT security and OT security are viewed as two separate worlds. Safety is subject to clear guidelines and extensive assessments have to be performed, whereas IT security and OT security are still often severely neglected. However, with OT and IIoT integrations, production environments are developing into one networked “world” where it is difficult to achieve complete isolation. This is very evident in sensor technology, where sensors convert physical states into data and transmit them to computers. IT security is crucial here because sensors are the data source and so is the basis for any further action in industrial systems. The more sensors are used in industry, the more interfaces there are; this may simplify maintenance processes, but can also pose a serious risk to security.
OT security is the job of the integrator and the operator at the development stage
When companies digitise OT systems and business processes, they have to deal with the issue of security at the same time. The IEC 62443 standard has now become established as the internationally recognised standard for security in the process and automation industry. The standard's area of application also covers other industrial sectors and critical infrastructures. The standard is intended for operators, system integrators and manufacturers of industrial automation systems, and takes into account all parties involved in the production and automation environment, also referred to as “Industrial Automation and Control Systems” (IACS).
IEC 62443 – what you should know about this standard
The standard is divided into four interrelated sections. These then contain documents on individual key areas. We would like to present these briefly to you:
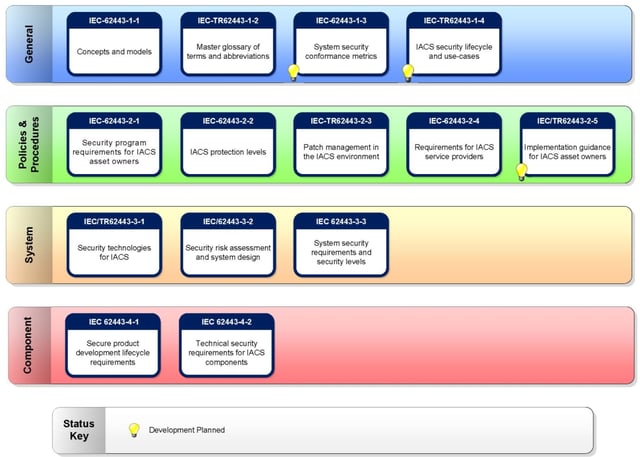
Figure: EC 62443 Series of Industrial Security Standard – Overview
- General
This section describes the basic terms, concepts and models. - Policies and procedures
In addition to technical specifications for control system security, this section describes a system for managing industrial IT security. Here there is a close connection to the well-known ISO 27000 family. The basic aim here is to continually improve OT security by evaluating the risks and specifications for processes and organisation. - System
Here, various specifications for safety functions of control and automation systems are outlined. The main focus is on manufacturing and process automation, including subjects like the control and monitoring of manufacturing processes. - Component
The fourth section describes the requirements for the product development processes of automation solution components.
Defence-in-Depth as a fundamental concept
IEC 62443 is based on the well-known “Defence-in-Depth” concept. This describes the protective measures that are implemented at various levels of a network or system. This widespread principle prevents an attacker, or an incident triggered by another means, from spreading unimpeded and causing damage by overriding a single measure.
To implement a well-designed security concept, improvements need to be made to all the security functions of all the systems, products and solutions involved. However, guidelines, processes and ultimately the operating staff must also be taken into consideration so that different protective layers can be put in place, much like the layers of an onion, so that if one layer is circumvented, the next layer will continue to provide protection. This principle is very useful for a variety of infrastructures and networks. Often the systems and components involved are not kept up to date with the latest security level due to a lack of updates and being permanently available.
Segmenting, identifying and authenticating
In technological terms, one of the keys is appropriate authentication, architecture and network zoning – all the way down to the “zero trust” level if need be. After all, secure identities are the first link in the chain of trust in automated communication. Good architecture involves the creation of appropriate security zones, i.e. physical or logical groupings of installations that share common security requirements and can isolate critical components of the control systems.
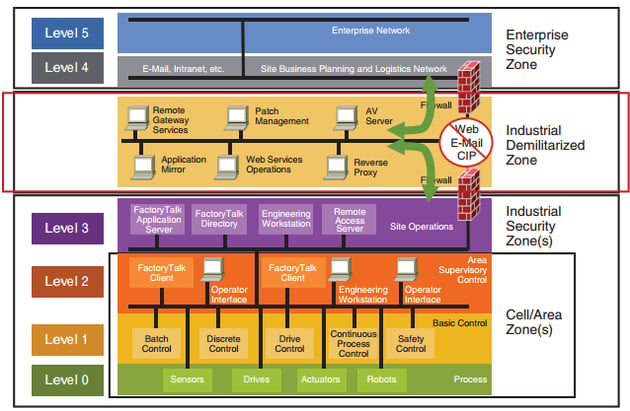 Figure: Purdue Enterprise Reference Architecture (PERA) model according to the ISA-99
Figure: Purdue Enterprise Reference Architecture (PERA) model according to the ISA-99
The figure illustrates an example of a possible network architecture of an IACS network. Please note: the VSE has also published a comprehensive manual for the power supply.
The segmentation describes a logical vertical separation. However, plant subnets can also be logically separated horizontally. Zones with similar needs for protection need to be identified and separated from each other with the help of technical methods. In doing so, different lines of defence (Defence-in-Depth) need to be established. The segmentation of environments, data streams and operating processes allows data and assets to be protected reliably. With segmentation and identity management, you do not need to reinvent the wheel. We recommend that you follow tried and tested, best-practice approaches.
Security versus maturity level
In addition, IEC 62443 is based on the approach that IT security is more than just a purely technical discipline because technical precautions can be bypassed by staff or operational processes and thus rendered ineffective. A distinction is therefore made between the functional technical “security levels” and the maturity level of the organisational processes and employees. Security levels can be used to assess systems, networks and components based on their level of IT security. Conversely, maturity levels focus on procedural compliance with organisational guidelines. By combining these two approaches, the result is a comprehensive safety concept that offers far more potential protection than a purely technical approach.
A company-wide understanding of security
So, you can see that IEC 62443 provides all the parties involved with an efficient means of ensuring a secure IACS environment and incorporating all the important aspects such as employee and production security, ensuring availability, increasing production efficiency and quality and protecting the environment. This enables companies to detect potential vulnerabilities in their control and instrumentation technology at an early stage and take the appropriate protective measures.
Of course, a comprehensive and future-oriented approach goes even further and encompasses the traditional IT landscape, development and production IT. This is the only way to achieve the aims of cyber security, minimise business risk and meet the regulatory requirements.
Where do you rank in digitising and automating your business processes?
Your OT infrastructures are also business critical. As a security officer, you need to be responsible for all of your production environment's security issues. InfoGuard can assist you in verifying the key components, setting up the architecture in line with the Defence in Depth methodology, building up security according to IEC 62443, setting up an appropriate supplier risk management, so making a significant contribution to reducing security risks, and to the company's success!
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


