Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
The seven mortal sins: how hackers can easily compromise networks

Lack of patch management, ignoring antivirus messages, direct Internet access: these are just three of the seven “mortal sins” of IT security, which cybercriminals often use and exploit by to penetrate networks and move unnoticed once they are in. First, the good news: such mistakes are easy to avoid. This blog post points out the seven mortal sins and tells you how to avoid the mistakes.
We all know that nowadays one hundred percent protection against cyber-attacks is an illusion. And that is why it is all the more important to build one’s own protective walls as high as possible – alongside comprehensive cyber defence. However, these walls must not only be high, but also solidly built. And this is where easily avoidable mistakes often occur on a technical level, which I and my colleagues like to call mortal sins.
Mortal sin 1: lack of patch management
You may remember the news coverage: last May, the NCSC (National Cyber Security Centre) was forced to notify more than 200 companies about a vulnerable Exchange Server on their network. And this is not an isolated case! At InfoGuard CSIRT (Computer Security Incident Response Team) we regularly see vulnerable Exchange Servers in our work. The tragedy is that exploit codes are often publicly available a few weeks after the vulnerabilities become known, e.g., in the popular Metasploit framework. Yet even so, many administrators fail to install these important security updates.
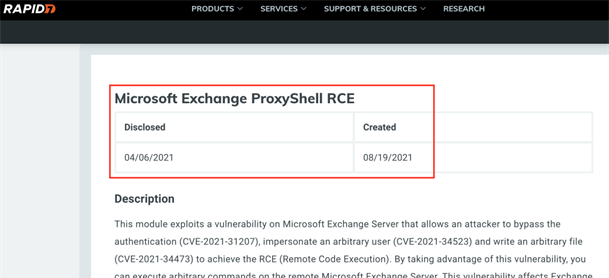
Figure 1: ProxyShell module by Metasploit
Confluence and VMWare Horizon are two other products that were extensively targeted by attackers in mid-2022 because security patches were not installed or were installed too late. In today’s attack landscape, administrators are encouraged to keep abreast of the security news to give them early warning of critical vulnerabilities and important patches.
Mortal sin 2: no multi-factor authentication
In addition to exploiting critical vulnerabilities, a lack of multi-factor authentication (MFA) is one of the most common gateways into networks. As a reminder: MFA means that additional verification via SMS, authenticator app or token is necessary in addition to the password. This means that there is no chance of attackers logging in legitimately even if passwords are leaked – or indeed there are good chances of them doing so if no MFA is in place. Despite awareness-raising or phishing campaigns, many people still fall for the (admittedly very professionally prepared) phishing emails and reveal their login credentials on fake portals.
Cybercriminals can use the revealed password for example to log into an employee’s mailbox and gate-crash email conversations. A common goal is to forge invoices or exchange account details so that money is transferred to an account controlled by the attacker. According to the FBI’s Internet Crime Report, the damage caused by this so-called “business email compromise” (BCE) in 2021 amounted to over USD 2 billion, which is several times the amount of damage caused by ransomware.
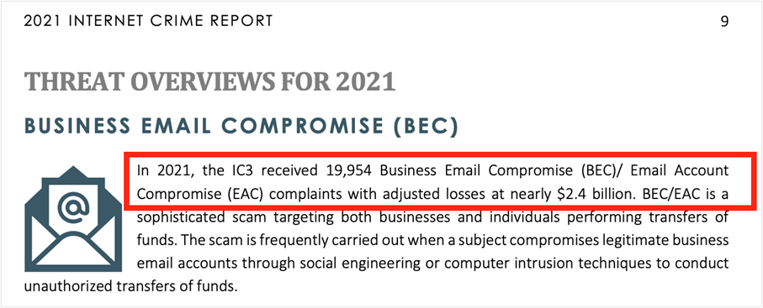
Figure 2: Excerpt from the FBI Internet Crime Report
It is important that any access to the company network or company information accessible from outside is protected by a second factor, be it access to the email account or VPN access to the internal network.
Mortal sin 3: ignore or misinterpret antivirus messages
For the third mortal sin, we start with a look at the “Antivirus Event Analysis Cheat Sheet”, created by the well-known German security researcher Florian Roth, which, by the way, is updated periodically. The “Highly Relevant” column is especially valuable for administrators and SOC analysts. This lists the most important keywords that demand a response if they are contained in a virus alert.
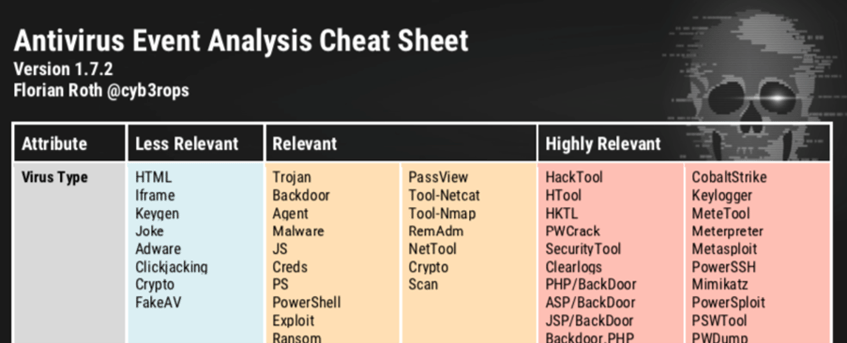
Figure 3: Florian Roth’s Antivirus Cheat Sheet
Analysis of many incident response cases shows that local antivirus services detect one or more of the attacker’s steps – including scripts and programs. However, we know from experience that antivirus alerts are often ignored or not analysed thoroughly enough. The cheat sheet is helpful in this context because it provides guidance on which keywords should be investigated – or that at least a specialist cyber security company should be commissioned to analyse the incident.
Mortal sin 4: lack of Active Directory hardening
Hackers also like to go for the heart – in this case, Active Directory, the heart of Windows networks. The end goal of many attackers is to compromise domain admin accounts. There are many well-documented attack paths via which attackers can acquire the highest privileges in a network. However, these attacks often depend on misconfigurations that can be found and corrected relatively easily. Here are a few classics that InfoGuard CSIRT regularly encounters in Active Directory assessments:
- Passwords of highly privileged accounts are not changed regularly (sometimes not for years!).
- Service accounts are part of highly privileged groups, which increases the risk of kerberoasting attacks.
- Passwords, some for highly privileged accounts, are stored in the GPO (Group Policy Object).
- Highly privileged accounts log on to regular clients (missing tiering model)
Such misconfigurations can be found through Active Directory assessments, raising the bar for cybercriminals.
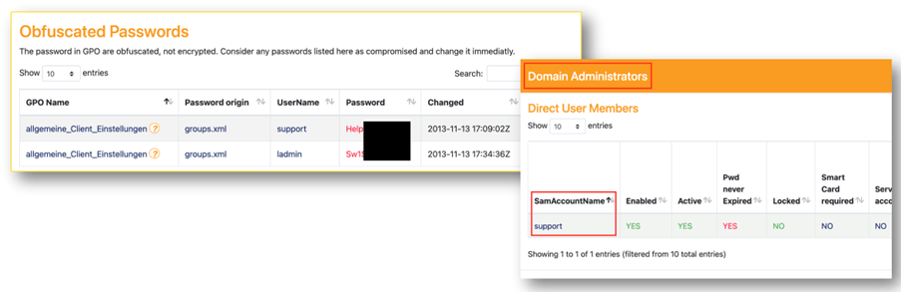 Figure4: Saved passwords in the GPO
Figure4: Saved passwords in the GPO
Mortal sin 5: no in-depth analysis after an incident
Unfortunately, no in-depth analysis is performed after an incident such as the infection of a server or client or after the outflow of login credentials. Consider the following scenario: a user falls for a phishing email and enters their login credentials on a fake platform. In many cases, only the password is reset in this case, but this is far from adequate. For example, checks would have to be made as to whether someone from an unknown IP address has successfully logged in, whether the attackers have had access to the mailbox and new inbox rules have been created etc. However, not only the mailbox should be checked, but also the VPN accesses. Another tip before resetting the password is to close all active sessions.
The same procedure applies to infected devices or servers. Check how long the host was infected for before the incident was noticed? Have the attackers already spread further in the network through the infected host? Were other credentials that could only be read from memory stolen? And so on.
Mortal sin 6: direct internet access
Our CSIRT often sees that servers can communicate directly to the Internet without being routed through a proxy. Attackers in the internal network exploit this circumstance to simply exfiltrate data from the network or to address the command & control server. The solution: route traffic through a proxy so that blocking rules can be set up that make attacks more difficult. As a result, attackers can no longer easily reload programs and issue commands on the compromised machines.
Mortal sin 7: missing EDR agent
In today’s attack landscape, a simple antivirus scanner is not enough to prevent attackers from compromising the network. To protect larger networks, what is known as an “Endpoint Detection & Response Agent” (EDR for short) is required. The benefits of such EDR agents on the one hand are the deep insights into the processes and network connections of the hosts, and on the other, malicious behaviour can be detected thanks to these insights.
IT security is complex, but not a dead end
If you now feel you have been caught committing one or the other “mortal sin” – you are certainly not alone. However, insight into and understanding of the relevance of such basic rules and practices is itself the first step in the “safe” direction. Nevertheless, cyber defence has become a must in the event that an attack is successful no matter how exemplary your behaviour. Since many companies lack both the know-how and the resources, it is advisable to obtain cyber-defence services from an external partner such as InfoGuard.
The services of our Cyber Defence Center (CDC) range from Managed Security Services, which monitor systems 24/7, detect and remedy weak points, to SOC-as-a-Services for holistic cyber defence, to Incident Response Services, where I and my team colleagues are immediately on hand should an emergency occur.
More information about our Cyber Defence Services and a contact form can be found on our website:
Blog

SWIFT CSCF v2025 Increases the Pressure: Only Cyberresilient is Compliant

Zero Trust Maturity Model 2.0: Security in a Dynamic Future


