Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
SWIFT CSCF v2023 – New Changes for Enhanced Cyber Security

The financial sector remains one of the most attractive targets for cyber criminals, which is why compliance requirements are (thankfully!) constantly being adapted. Accordingly, version 2023 of the SWIFT Customer Security Control Framework (CSCF) again involves some changes.
In summary: first, there is a new mandatory control 1.5 (only for architecture type A4 “Middleware/File Transfer Server as Connector”); second, the differences between the various architecture types have been better documented. New controls have been introduced for the other architectures (except A4), but some have been adapted slightly in terms of content. An excerpt:
- The requirement to control systems’ connections (e.g. USB connections) has been moved from control 3.1 (Physical Security) to control 2.3 (System Hardening).
- Control 2.2 (Security Updates) aligns the vulnerability remediation timeframes to common standard for security patching, also taking regular update deliveries into account.
- Control 6.1 (Malware Protection) specifically mentions, as optional enhancement, to consider all the general operator PCs, not only the Windows OS based ones.
There have also been some changes to the Independent Assessment Framework, which are discussed in more detail below.
CSCF v2023: What needs to be borne in mind?
The following changes to SWIFT CSCF v2023 need to be taken into account:
Architecture typ A4
- New mandatory conrol 1.5: Customer Environment Protection (equivalent to control 1.1, which is mandatory for the other A* architecture types).
- Further specification of A4 architecture type compared to type B: emphasis that the distinction lies in the type of endpoint (server or client).
Back-office systems (e.g. core banking system, ERP system):
- It is pointed out that adequate protection of back-office systems (e.g. core banking system, ERP system), responsible for generating transactions, is strongly recommended. This is becoming increasingly important with the increase in APIs.
New mandatory control 1.5 (Customer Environment Protection) – for architecture type A4
Following the introduction of customer connectors and architecture type A4 (by splitting architecture A3) in SWIFT CSCF v2021, control 1.5 (Customer Environment Protection) is now mandatory to bring architecture A4 in line with A3 and protect all connectors equally.
Distinction between architecture types A3, A4 and B
The architectural drawings have been revised and expanded to clarify the division between the different A3, A4 and B architectures.
Architecture type A3- SWIFT connectors, e.g.: Lite 2 AutoClient, SIL – Alliance Cloud, SIL – CFS, SIL – gpi connector, SWIFT API connector, SWIFT Microgateway
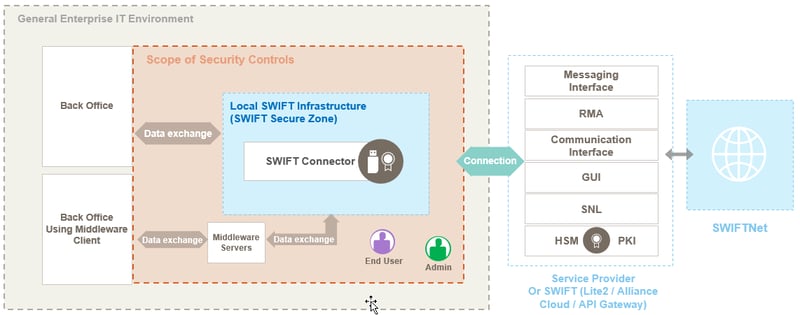
Source: SWIFT Customer Security Controls Framework v2023, Customer Security Programme (Version 01.07.2022)
Architecture type A4- Customer connectors, e.g. middleware server (e.g. MQ Server, Kafka)
- File Transfer Server (SFTP Server)
- Customer API connectors (internally developed application that uses the API specifications or integrates the Swift SDK)
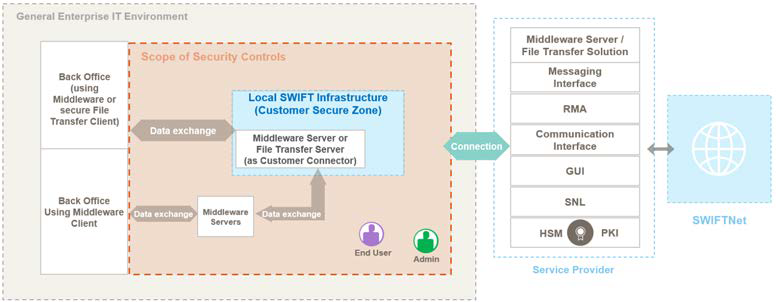
Source: SWIFT Customer Security Controls Framework v2023, Customer Security Programme (Version 01.07.2022)
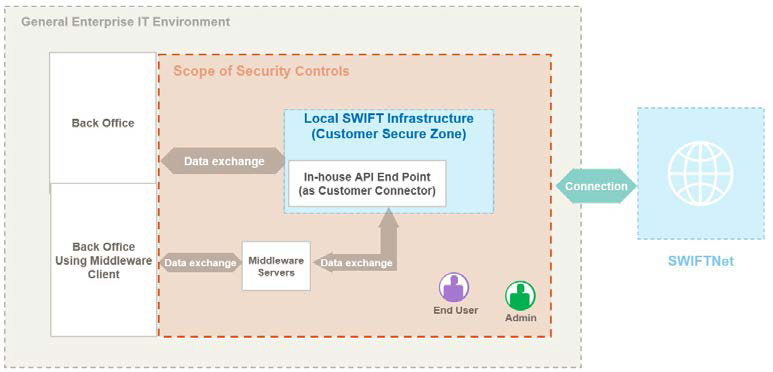
Source: SWIFT Customer Security Controls Framework v2023, Customer Security Programme (Version 01.07.2022)
Architecture type B
- Users only access SWIFT messaging services via a GUI application at the service provider (user-to-application).
- A user’s back-office applications (core banking system, ERP system) communicate directly with the service provider (application-to-application) using APIs from the service provider, a middleware client (e.g. an MQ, Kafka or Solace client/broker) or a secure file transfer client without connecting directly to SWIFT or independently transmitting business transactions.
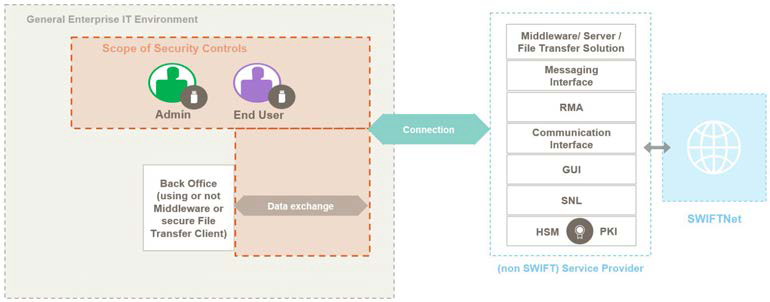
Source: SWIFT Customer Security Controls Framework v2023, Customer Security Programme (Version 01.07.2022)
Update of Independent Assessment Framework – removal of Delta Assessment
The Delta Assessment, as it was known last year, has been completely cancelled by SWIFT. All controls must be (re)assessed at each assessment. However, it is still possible to rely on the assessment of the control(s) from the previous year’s independent assessment (whether internal, external, mixed or SWIFT-mandated). Either way, an annual certification must be supported by an independent assessment, whether or not that certification is based on a previous audit in part or in full.
SWIFT has developed a new mandatory assessment report template to be completed by the assessor in addition to the familiar assessor templates for easier documentation of the chosen testing approach.
SWIFT Assessment – are you ready for compliance v2023?
Be prepared to address any non-compliance issues in good time before the end of 2023 with our SWIFT Compliance Assessment. We offer comprehensive cyber security services and support in assessing SWIFT customer security programmes. Our comprehensive SWIFT Assessment provides you with an evaluation of your ACTUAL state and clear recommendations for v2023 compliance. Secure your SWIFT transactions and stay compliant in the ever-changing financial world!
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


