InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
SWIFT CSCF v2021 – are you ready for the independent assessment?

The financial sector remains one of the main targets for cyber attacks. According to one analysis, of the 200 banks polled, 4 out of 5 have sustained at least one SWIFT fraud attempt since 2016. The total damage due to SWIFT payment fraud was at least US$ 380 million. In addition, two-thirds of banks reported that SWIFT cybercrime has been on the rise since 2016. There is now pressure on financial institutions and specialists to plan and implement the steps needed for compliance. In this blog, you will learn about the key changes to the SWIFT Customer Security Controls Framework (CSCF) in the 2021 version.
CSP v2021: What should you watch out for?
The following changes to the SWIFT CSCF v2021 must be taken on board:
-
New mandatory control 1.4 – restricting Internet access (this item was previously part of the control 1.1)
-
Newly-introduced architecture type A4 to distinguish SWIFT connectors from customer-owned connectors (B or A3 architectures could become A4)
-
Introduction of the independent assessment
New mandatory control 1.4 – restricted Internet access
The SWIFT v2021 assessment includes a maximum of 22 mandatory and nine advisory controls, with extensive implementation guidelines. The total number of controls is dictated by the type of architecture, which depends on how SWIFT members connect to the SWIFT network. SWIFT differentiates between five possible architecture types (types A1-A4 and type B), with all 31 controls (22 mandatory) falling within scope for architecture types A1 and A2, and only a subset of 22 controls (14 mandatory) falling within scope for architecture type B.
The CSCF v2021 is simply promoting the previous year's advisory control to the new mandatory control. In practice, however, this control 1.4 was already part of mandatory control 1.1, which has been in place from the very first version of the CSCF. As a result, for clients who have already followed the CSCF v2020, there should not be any additional burden with the controls within the CSCF v2021. This is because the CSCF v2021 mainly consists of clarifications to the scope of existing controls. Here is an overview:
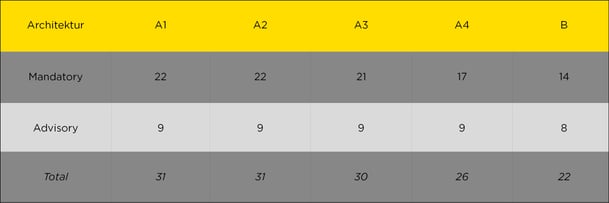
Table 1: Number of controls per type of architecture
New architecture type A4
The CSCF version 2021 introduced a new architecture type A4 to distinguish SWIFT members that use SWIFT connectors (A3) versus members that use customer-owned connectors (new A4). Expanding the scope to include middleware/MQ servers and file server solutions as customer-owned connectors could result in some existing B or A3 architectures becoming A4.
- Architecture type A3:
SWIFT connectors, e.g.: lite 2 autoclient, SIL - alliance cloud, SIL – CFS, SIL - gpi connector, SWIFT API connector, SWIFT microgateway. - Architecture type A4:
Customer connectors, e.g.- Customer API connectors: Proprietary applications deployed in the user environment that implement SWIFT APIs (either using the specifications or by integrating the SWIFT SDK) to connect directly to SWIFT services (e.g. alliance cloud, lite2).
- FTP solutions (FTP servers): Locally installed file transfer solutions used to facilitate communication with SWIFT components supplied by a service provider.
- Middleware/MQ servers: Local middleware system implementations, such as IBM® MQ servers, used to exchange data between the SWIFT components (in the local SWIFT infrastructure or at a service provider) and the user's back office.
The following example illustrates in a schematic way the architecture type A4 with the integration of commercially available customer connectors such as file transfer solutions or middleware/MQ servers:
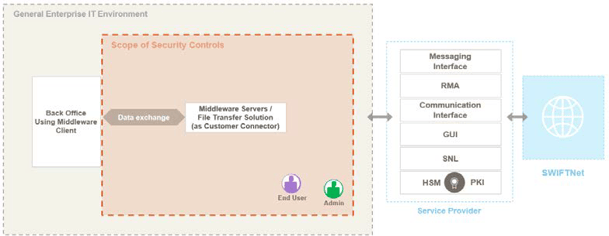
Diagram 1: Architecture A4 – middleware/file transfer as a connector (source: SWIFT)
The following example illustrates in a schematic way the architecture type A4 with the integration of customer API connectors developed in-house:
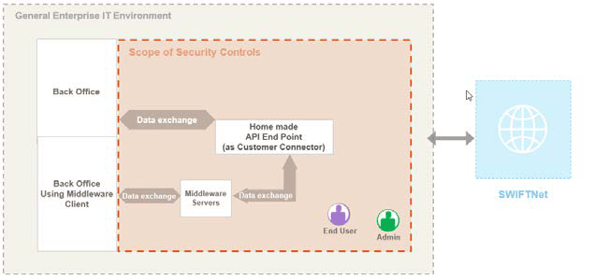
Diagram 2: Architecture A4 – customer (home-made API) connector (source: SWIFT)
Independent assessment
Due to COVID-19, in mid-2020 SWIFT had decided to revert from CSCF v2020 to the previous year's 2019 version, as well as suspending independent assessment. Independent assessment is now being introduced in 2021.
Therefore, self-assessment is no longer permitted for this year's certification, which must be carried out between July and December 2021. What is known as an independent community standard assessment must be carried out; this is illustrated in the following diagram.
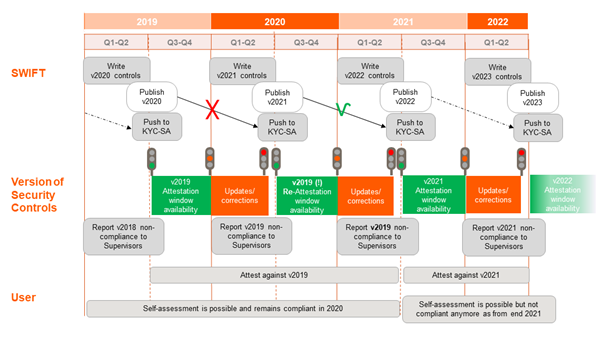
Diagram 3: https://www.swift.com/ja/node/300801
To carry out an independent assessment, you have the two following options:
- Independent internal assessment:
- Performed by the second or third line of defence (such as compliance, risk management or internal audit) that operates independently of the first line-of-defence that submitted the self-assessment (e.g. CISO).
- The persons performing the assessment are to have recent, relevant experience in assessing cyber-related security controls.
- Independent external assessment:
- Conducted by an independent external organisation with experience in cyber security assessment.
- Assessors who hold industry standard security certifications.
Qualified assessors must have experience that is recent (within the last twelve months) and relevant in order to be able to perform a cyber security-focused assessment in accordance with an industry standard such as PCI DSS, ISO/IEC 27001 or the NIST Cyber Security Framework. In addition, assessors must be independent, as defined by the Institute of Internal Auditors (IIA), and at least the lead assessor must have industry-related professional certification (e.g. CISSP, CISA, CISM, ISO/IEC 27001 Lead Auditor or QSA). When assessing users’ security compliance, assessors must use a risk-based approach. Implementation can be done either in accordance with the documented implementation guidelines proposed by SWIFT, or in accordance with an alternative implementation that addresses the risk drivers, covers the relevant in-scope components and meets the specified control objective.
If the independent assessment is not carried out by a SWIFT member, or if the results are unsatisfactory, SWIFT reserves the right to report this to the local supervisory authorities or other SWIFT members (counter-parties). Ultimately, the “weakest link” puts the entire network at risk. It should also be mentioned, for the sake of completeness, that the SWIFT-mandated assessment (audit initiated by SWIFT) still exists. This must be carried out by an external party.
Ensure SWIFT compliance – act now!
Get the assessment done early, so that you have time to deal with any non-compliance issues before the end of the year. Are you aware of the current status of your compliance? Do you need support in interpreting and implementing the measures required? Are you looking for a qualified external service provider to carry out the assessment in your company?
InfoGuard is a provider of SWIFT CSP assessment and cyber security services, and can carry out a compliance assessment for the required confirmation. We are available to assist you with implementing the SWIFT CSCF controls or to conduct a compliance assessment of your implementation of the SWIFT CSP. Our SWIFT assessment provides you with a comprehensive overview of your current status, as well as recommendations for measures to meet compliance v2021. You can find more information and a contact form here:
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first


