Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
The clock is ticking: stricter NIS2 guidelines from October 2024

The EU adopted the NIS2 Directive on cyber security in December 2022. The EU member states have until 17 October 2024 to enact a corresponding national NIS2 law. Affected companies are obliged to comply with the new regulations from 18 October 2024 (no transition period provided). This article explains what you need to bear in mind.
In view of the growing threat of cyber attacks, including on critical infrastructures (KRITIS), it is essential for companies to optimise their cyber resilience – the ability to prevent, withstand and recover from cyber incidents. The aim of NIS2 is to achieve a better collective level of cyber security.
From October 2024, many companies will be subject to significantly stricter, mandatory security measures and reporting obligations – including many businesses that were not previously affected. Swiss companies would also be well advised to align themselves with the security measures, although NIS2 is essentially aimed at European organisations.
NIS2 – and what needs to be considered by when
This EU Directive is a minimum standard which must be enshrined in national law by the EU member states. The EU Directive is relevant for Swiss companies because it explicitly includes supply chains and partner companies. Swiss companies also need to observe NIS2 more generally as part of their operations in the European Union.
At present, the implementation status in the individual EU member states varies greatly. Legislation in some countries is already well advanced and is currently the subject of public debate (e.g. Austria, Belgium, Croatia, Czech Republic, Finland, France, Germany, Italy, Netherlands, Sweden). In other countries, the status is unclear as little or no information is available.
There are considerable differences in national implementation levels: the definitions of sectors and companies are not standardised; obligations are interpreted differently; verification checks are sometimes carried out by authorities, sometimes by operators and sometimes not at all. There is also variation in terms of the level of detail for specifications and requirements for implementation.
SMEs are also affected by NIS2
In future, providers of digital services will also be obliged to implement suitable state-of-the-art technical, operational and organisational security measures in addition to critical infrastructures (KRITIS) such as electricity and water supply companies, the financial sector and the healthcare sector.
At the same time, sectors such as postal and courier services, waste management and food producers must also take appropriate measures to protect themselves effectively against cyber attacks. The Directive generally applies to organisations with 50 or more employees and an annual turnover of more than €10 million, and thus also covers SMEs.
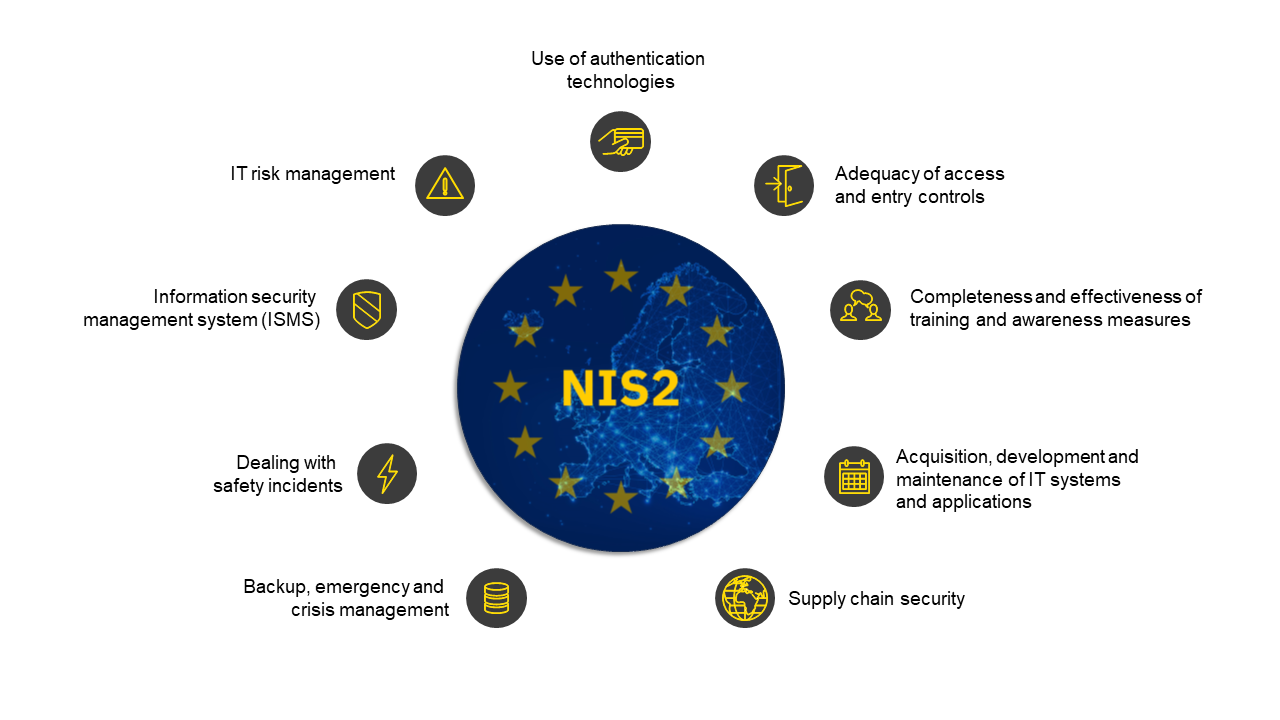
Substantive focus of NIS2
Alongside backup, emergency and crisis management, the sensitisation of employees as well as regular audits and procedures for evaluating the effectiveness of the company’s own risk management measures, NIS2 also requires risk-analysis and security concepts for IT systems to be implemented and vulnerabilities and security incidents to be managed.
Key practices include zero-trust principles, regular software updates and appropriate network segmentation. Sufficient identity and access management and multi-factor authentication are a must.
The challenge for companies is not only to implement such measures, but also to perform regular effectiveness checks, whether in the form of vulnerability scans, security assessments, penetration tests or simulated cyber attacks.
These four points must be observed when implementing NIS2
Irrespective of the specific manner of national implementation, affected companies must observe the following changes, which will come into force on 18 October 2024:
- Registration with the competent national authority.
- Incidents must be reported to the local competent authorities.
- Conformity with the requirements must be guaranteed.
- Proof of conformity through appropriate certification or a security review/security audit should be provided on a regular basis.
Companies affected by NIS2 should check that they fulfil the requirements of the EU Directive and rectify any identified divergences in good time to ensure that at least the minimum EU-wide requirements are met.
Any existing country-specific requirements should be taken into account in order to minimise potential non-conformities. It must be ensured that conformity is permanently guaranteed.
Gap assessment to determine the NIS2 maturity level
Find out how your company is positioned in terms of NIS2 and what still needs to be done. A NIS2 gap assessment provides an overview of possible divergences from the minimum requirements in your IT security strategy.
But there's more: our specialists will also provide you with technical, organisational and personnel-related recommendations and suggestions for implementing immediate measures.
Let us support you and get your NIS2 optimisation underway now.
Implementation of concrete safety measures
At InfoGuard, over 230 experts are available to help you meet the NIS2 requirements, be it with our Risk Management & Compliance Services or 24/7 Cyber Defence & Incident Response Services from our ISO 27001-certified Cyber Defence Center in Switzerland.
Get in touch: our cyber security experts will be happy to support you.
NIS2 will soon be followed by the Cyber Resilience Act (CRA)
While the NIS2 Directive aims to strengthen companies’ basic resilience against cyber threats by creating a uniformly high level of security, the Cyber Resilience Act (CRA) seeks to increase the security of digital products in the long term.
We have already reported on the announcement of the introduction of the CRA. In the coming weeks, we’ll be taking another detailed look at the latest developments in a separate blog post.
Stay tuned and subscribe to our blog updates.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant





