InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
ISO 27001:2022 – what has changed and what you need to get done

In October 2022, the International Accreditation Forum (IAF) published the new ISO/IEC 27001:2022 standard which replaced the previous ISO/IEC 27001:2013 version. This means that the established international standard has been revised and now comes with a number of important changes. The major impact is primarily the revising of the security measures and the way they are structured in Appendix A. This was published already in mid-February 2022 as part of the revised ISO/IEC 27002:2022 standard. This article explains what the new version of the ISO 27001 standard will mean for you.
We have had to wait a long time for the third version of the ISO 27001 standard. After nine long years, the new version was published in late October 2022. At present, it is only available in English, with the German translation expected to be available by autumn at the earliest. The first obvious change is the standard's name. Previously, ISO 27001 was entitled “Information technology – Security procedures – Information Security Management systems - Requirements”; now it is called “Information Security, Cyber Security and Protection Protection - Information Security Management Systems – Requirements”. Including the topic of data protection is a novelty, but it is not particularly surprising as very similar goals are pursued by both information security and data protection - even though they have different outlooks there is overlapping content.
ISO/IEC 27001:2022 – “Editorial” changes
In essence, the standard itself has undergone only marginal changes. If you take a look at the table of contents, for example, you will notice that sub-chapters have been added to Chapters 9.2 (Internal Audit) and 9.3 (Management Review), chapters 10.1 (New: Continual improvement) and 10.2 (New: Nonconformity and corrective action) have switched positions. Furthermore, Chapter 6.3 (Planning of Changes) has been added.
Otherwise, the content and structure of the standard itself has not changed that much from the previous version. The core idea of the management system, which is also found in its basic features in other ISO standards, remains unchanged.
All the same, following we would like to briefly discuss the changes to some parts of the content.
-
-
In Chapter 4.2 (Understanding the needs and expectations of interested parties) a further point (c) has been added: The organisation shall determine which of these requirements will be addressed through the information security management system (ISMS).
-
In Chapter 4.4 (ISMS) the existing requirements have been expanded in one significant area:
The organisation shall establish, implement, maintain and continuously improve an information security management system, including the processes needed and its interactions, in accordance with the requirements of this document.
-
In Chapter 6.1.3 (Information security risk treatment) a footnote referring to Appendix A has been added. “Appendix A contains a list of potential information security controls...” In practice, it is always debatable whether all the controls need to be implemented or not. This has not completely taken off the table with the word “potential”, but it is clear that there is some leeway here.
-
In Chapter 6.2 (Information security objectives and planning to achieve them) the following has been added concerning information security objectives to “be monitored" (point d) and “be available as documented information" (point g).
-
Within the new Chapter 6.3: “Planning of changes” the following is required: “When the organization determines the need for changes to the information security management system, the changes shall be carried out in a planned manner.” This goes without saying, but now it is stated as a mandatory requirement under the standard.
-
In Chapter 7.4 (Communication) points d) and e) have been combined
-
Several amendments have been made to Chapter 8.1 (Operational planning and control). Under the standard, criteria for the processes are required to be defined for control purposes, and the controls must be carried out in accordance with these criteria. Furthermore, documentation must be made available so that evidence can be provided that the processes are functioning correctly. Reference is also made to external processes: “The organization shall ensure that externally provided processes, products or services that are relevant to the information security management system are controlled.”
-
In Chapter 9.1 (Monitoring, measurement, analysis and evaluation) the order of the sentences have been changed.
-
Chapter 9.2 (Internal audit) has been subdivided. It now consists of chapters 9.2.1 (General) and 9.2.2 (Internal audit programme). However, there have been no changes in terms of content.
-
The same also applies to Chapter 9.3. (Management review). It is divided into 9.3.1 (General), 9.3.2 (Management review inputs) and 9.3.3 (Management review results). In addition, in 9.3.2 it has also been added that “changes in needs and expectations of interested parties that are relevant to the information security management system” (Point c).
-
As already mentioned, Chapters 10.1 and 10.2 have switched position. However, nothing has changed in terms of content either.
-
So far, so good – up to this point, the changes to the standard seem to be mostly “cosmetic”.
ISO/IEC 27001:2022 – updated security controls
The most relevant amendments can be found in the above-mentioned Appendix A. The controls have been updated and restructured. There are now only 93 measures instead of 114. This is despite the fact that 11 new controls have been added, i.e. some of the controls have been combined.
As previously mentioned, the associated standard ISO 27002 with recommendations for action and guidance for implementing the individual controls was published back in mid-February 2022, and we have already presented it in an earlier blog article.
The Controls in Appendix A to ISO 27001:2022 are now divided into four control types:
-
Organisational Controls with 37 measures (3 new measures – A.5.7/23/30)
-
People Controls with – like before – 8 measures
-
Physical Controls with 14 measures (1 new measure – A.7.4)
-
Technological Controls with now 34 measures (7 new measures – A.8.9/10/11/12/16/23/28)
The new 11 controls, which deal with current topics such as cloud security, threat intelligence and data protection-related issues, are entitled as follows:
-
-
A.5.7 Threat intelligence
-
A.5.23 Information security for use of cloud services
-
A.5.30 ICT readiness for business continuity
-
A.7.4 Physical security monitoring
-
A.8.9 Configuration management
-
A.8.10 Information deletion
-
A.8.11 Data masking
-
A.8.12 Data leakage prevention
-
A.8.16 Monitoring activities
-
A.8.23 Web filtering
-
A.8.28 Secure coding
-
In addition to the new measures and the completely revised structure, each measure is now assigned five additional attributes:
-
Control Type (preventive, detective, corrective)
-
Information security properties (confidentiality, integrity, availability)
-
Cybersecurity concepts (identify, protect, detect, respond, recover)
-
Operational capabilities (e.g. governance, physical security, IAM, etc.)
-
Security domains (governance_and_ecosystem protection, defence, resilience)
The attributes compensate the new, flat hierarchy of ISO 27001:2022 Appendix A compared to the previous version (4 control types in the new version versus 14 areas in the 2013 version). This attribution also means that strength/weakness profiles can be displayed and potential improvements can be identified.
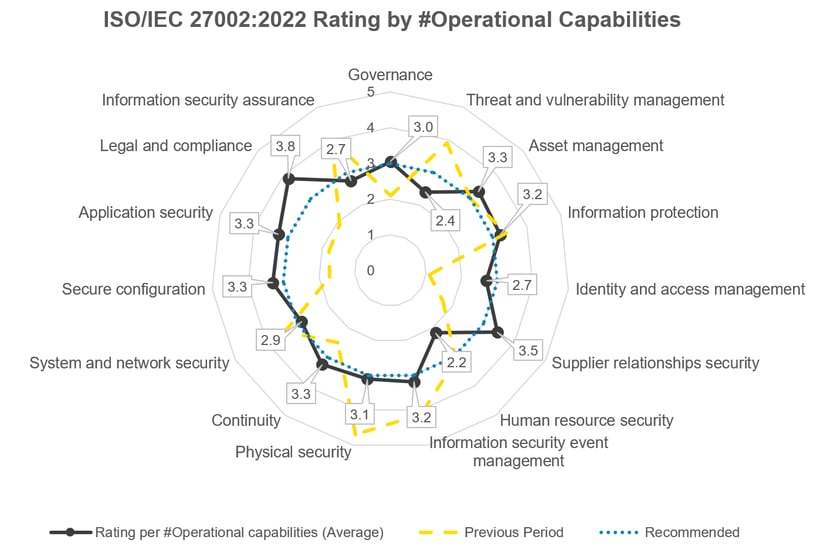
Fig: Example of a strengths/weaknesses profile in accordance with ISO/IEC 27001:2022 Appendix A. Operational Capabilities
What does the publication of the new version of the ISO 27001 mean for companies?
Although the changes are significant, they do not demand a completely new approach to information security or drastic changes to a pre-existing information security management system. What they represent are adaptations that were desperately required to assist the growing understanding and importance of information security. This means that the basic statements and requirements of the new ISO 27001:2022 are comparable to those in its precursor.
Nevertheless, by fundamentally restructuring the security controls, known and established topics have been separated, for example “Access Management” and the controls associated with it (formerly Chapter 9, Appendix A). This discipline is now spread across three of the four control types: organisational, physical and technical controls.
Conversely, some existing measures have been combined, such as the following: 9.2.2 (User access provisioning), 9.2.5 (Review of user access rights) and 9.2.6 (Removal or adjustment of access rights), which are now combined under 5.18 (Access Rights). At the same time, it is inevitable that the growing importance of data protection will result in a call for an integrated management system for both areas, and this makes it advisable to add the ISO 27701 standard to supplement ISO 27001 and ISO 27002 .
Even if there are still three years left before the changeover, every company with an existing certification is advised to address the required changes immediately and draw up a project plan for migration to avoid (unnecessary) time pressures later on.
ISO/IEC 27001:2022 – An overview of all the transition periods
ISO 27001:2022 was published on 25 October 2022, with a three-year (36-month) transition period. This translates into the following transition periods and deadlines for those who use the standard:
-
-
Readiness for certification in accordance with ISO/IEC 27001:2022
→ Probably from the 2nd half of 2023 (depending on the accreditation body), not guaranteed information
-
Last date for initial/re-certification audits under the former ISO 27001:2013
→ 18 months after the new ISO/IEC 27001:2022 is published, i.e. April 2024
-
Conversion of all existing certificates to the new ISO/IEC 27001:2022
→ 3 years, based on the last day of the month on which ISO/IEC 27001:2022 is issued (October 2025). By then, all ISMS must be aligned with the new standard.
-
These transition deadlines are commonplace for ISO standards. They correspond to the re-certification cycle that is used under ISO 27001 in any case. Certified companies have to go through a completely new audit process every three years in order for their ISMS to be re-certified.
What does this mean for you?
-
-
For companies that are already certified
Documentation for the new controls should be amended and updated as soon as possible. The company can then be certified in accordance with ISO 27001:2022 at the upcoming re-certification audit. -
For companies that are not yet certified
If companies want to be certified for the first time, they can still do it under the old version. However, if the audit is planned to be done after the time the accreditation body is ready to provide certification, it is recommended to directly implement the new version. This would mean that there is no need to conduct a new audit once the transitional period has expired.
-
Are you seeking ISO 27001:2022 certification, but need help with implementing it?
At InfoGuard, we accompany you on your path to compliance. Our information security experts have the sector-specific expertise to implement an ISMS in accordance with ISO 27001:2022 (also, with ISO 27001:2013 or taking into account other standards like NIST CSF, DSG/GDPR, SWIFT, etc.) and we can accompany you through both internal and external audits.
The entire process can be supported by our information security management platform, which automates manual processes and guides you step by step through the entire project. Just make an appointment, no-obligation consultation and start the ISO 27001:2022 migration process as soon as possible.
Blog
Zero Trust ab 2026: 3 Praxisansätze für Cyberabwehr zwischen KI und Compliance

Cyber Security Radar 2026: Die zentralen Traktanden für CISOs und CIOs

