Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
IaaS and SaaS: connection without any obstructions

Is it true that “Infrastructure as a Service” (IaaS) or “Software as a Service” (SaaS) cannot work together with on-premises IT? Not at all! In this blog post, you will discover how an IaaS or an SaaS cloud environment can be combined with a company’'s on-premises IT in a classic hybrid situation. The focus here is on network-related aspects while keeping other aspects in mind. To give you a better illustration of this issue, let’s take a look at the scenario via a fictitious company. So once again, Hedgehog Winter Sleep AG has a challenge to overcome and we are invited to watch it unfold.
Hedgehog Winter Sleep AG needs to grow, so a new ERP and PPS are called for
Business is booming at Hedgehog Winter Sleep AG. Each autumn, demand for hedgehog shelters literally goes through the roof, fuelled by seasonal demand. This year, the business is also developing in a very positive direction with mobile, prefabricated piles of foliage.
Against this background, Mrs Tiggywinkle (the CEO of Hedgehog Winter Sleep AG) has decided to take strategic steps. She wants to procure new solutions for Enterprise Resource Planning (ERP) and the Production Planning System (PPS), with the aim of getting rid of the performance and quality issues that have arisen.
She chose an integrated system that combines both functions: “Carefree ERP&PPS” from Carefree AG. Its range of operating models makes the product a winner:
- On-premises in a client container environment
- Operation within a cloud infrastructure (IaaS)
- Bought from the cloud from Carefree AG as Software-as-a-Service (SaaS)
The Hedgehog Winter Sleep AG IT team needs external support for architecture integration and to ensure the security of the solution. Mrs Tiggywinkle asked InfoGuard if the architecture team could deal with the following issues:
- How should Hedgehog Winter Sleep AG connect Carefree ERP&PPS to the internal IT?
- What specific aspects need to be taken into account?
It was clear to my colleagues at InfoGuard what was needed, and they immediately began to support the architecture team in their usual organised way.
The first thing to be done is identify interrelationships
The first thing for the architecture team to do was to get an overview. Hedgehog Winter Sleep AG had undergone significant growth over the last few years, leaving little time for designing the architecture.
The Hedgehog Winter Sleep AG network is distributed between the following areas:
- Office: A desktop working environment for customer care and administration
- Manufacturing: Production of hedgehog homes and prefabricated leaf piles
- Server: Multi-purpose for all client/server-based applications, including the online store
- Management: Management network for administration of the IT components
- Entry DMZ Zone:Central internet entry/exit point. Access for customers to the online store, remote access for employees as well as Hedgehog Winter Sleep AG’s access to the web and to external services
These areas are connected to each other via a firewall. The areas protected in this way are also called zones. Sensibly, the firewall rules restrict the traffic between the areas or zones, for example, there is no office zone access to the production area.
On the wrong track: check requirements for the future cloud setup!
As a first step, it quickly became clear, however, that this was not the right approach for tackling the specific problem. It is not a matter of whether the current network design is adequate; it’s more about what requirements will be needed in the future cloud setup. Among other things, this requires that the future operating model of the Carefree ERP&PPS be defined.
(Non-)Decision No. 1 – IaaS versus SaaS
A range of discussions were held with the contacts at Hedgehog Winter Sleep AG. It became clear that it was not a sensible option to run Carefree ERP&PPS on-premises. Hedgehog Winter Sleep AG is seeking to reduce local IT, not to expand it. There were equal votes both for operating Carefree ERP&PPS in a cloud infrastructure (IaaS) and for obtaining services from Carefree AG as an SaaS. In the end, the architecture team was commissioned to design a solution for both variants, so that a well-informed decision could be reached.
The architecture team set to work producing the following assessment:
|
Characteristic |
Carefree ERP&PPS as IaaS with a Cloud Service Provider |
Carefree ERP&PPS as an SaaS |
|
Authentication
|
Federation, design freedom as long as they cover Carefree ERP & PPS'’ needs |
Federation as specified by Carefree Ltd. |
|
Operation
|
Shared Responsability1: Cloud service provider is responsible for the infrastructure, while Hedgehog Winter Sleep AG is responsible for the applications running on it. |
Shared Responsability: Operational responsibility lies with Carefree AG. |
|
Monitoring |
Extending the existing monitoring solution to the cloud service provider. Any events that occur at the cloud provider are correlated with the Hedgehog Winter Sleep AG monitoring solution2. |
Carefree AG’s monitoring tool |
|
Stretched Network
|
The network areas that will probably be needed: entry, server and management will be connected with the corresponding counterpart at Hedgehog Winter Sleep AG. (known as a "Stretched Network") |
Not avilable |
|
Affiliation/Belonging
|
The IaaS environment is considered to be a Hedgehog Winter Sleep AG "Stretched Network", or demarcated area. |
The SaaS environment is a demarcated area. |
Table 1: Comparison between Carefree ERP&PPS IaaS versus SaaS
Stretched network or demarcated environment
In a stretched network, the on-premises network areas are stretched to the IaaS provider as far as required. The advantage of this is that similar systems (either on-premises and/or IaaS) can be located within the same network area.
The scenario is illustrated in Figures 1 and 2. Only the office zone with the workstations for customer care and administration and the entry zones are needed at Hedgehog Winter Sleep AG, and are therefore not "stretched".
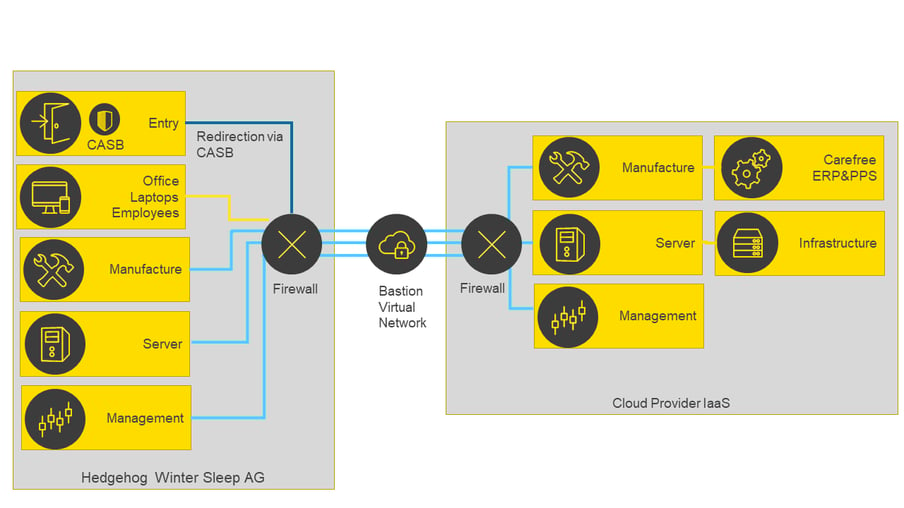 Fig. 1: Stretched Network with IaaS
Fig. 1: Stretched Network with IaaS
In a stretched network, the impact of attacks is increased. An attack, for example on the manufacturing network, would also compromise the directly connected "counterpart". In Figure 2, this is shown by the red dotted line.
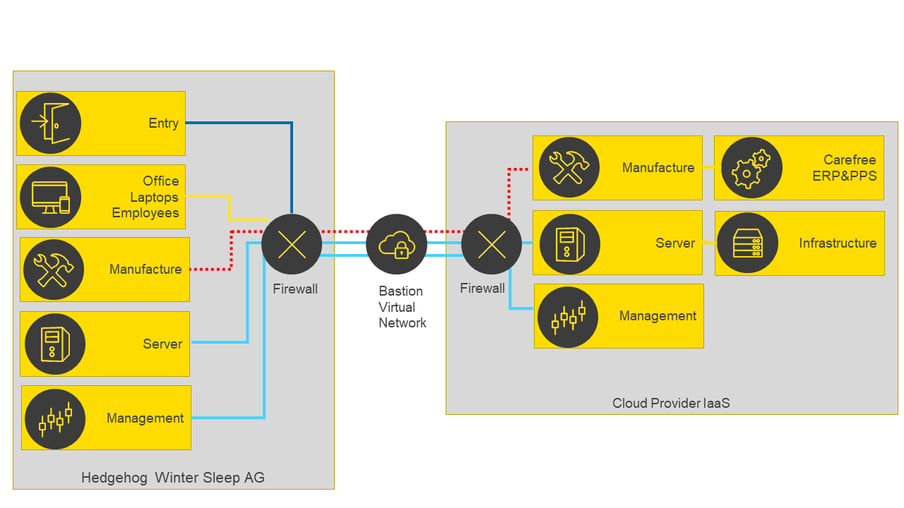 Fig. 2: Effect of compromise
Fig. 2: Effect of compromise
A demarcated environment is the counterpart to a stretched network. Here, the demarcated environment is integrated into the corporate network as a whole. This provides maximum separation between Hedgehog Winter Sleep AG and Carefree AG. Figure 3 illustrates this scenario for connecting Carefree AG as a Software as a Service (SaaS) provider: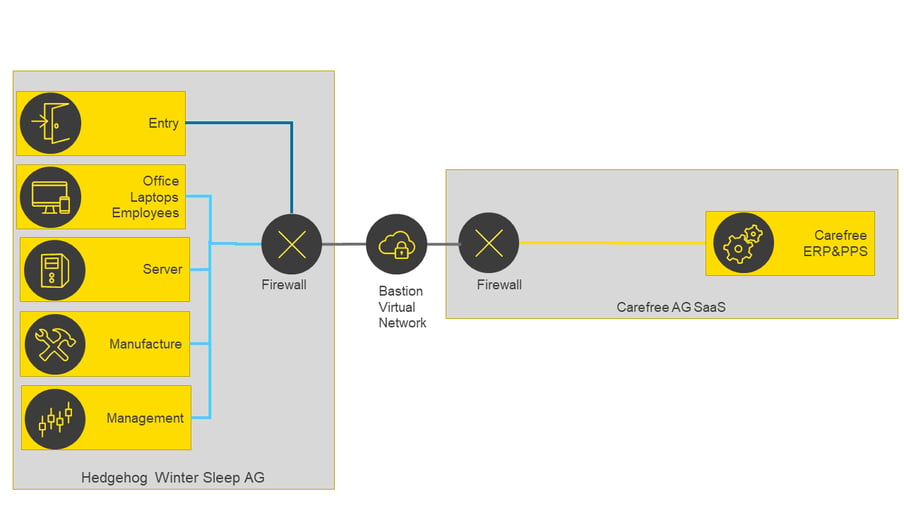 Fig. 3: Demarcated environment for SaaS
Fig. 3: Demarcated environment for SaaS
Similarly, it is possible to create a ring-fenced setup for an Infrastructure as a Service (IaaS) provider. This is illustrated in Figure 4:
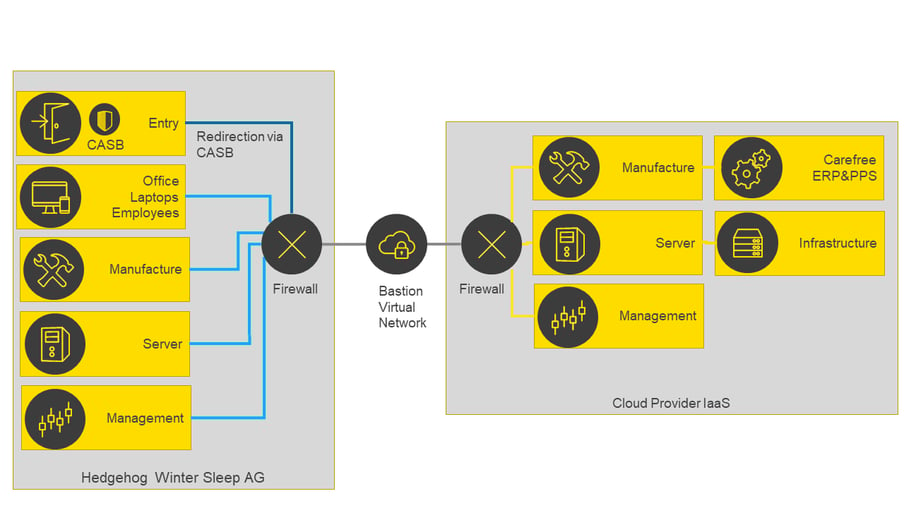 Fig. 4: Demarcated environment for IaaS
Fig. 4: Demarcated environment for IaaS
Yet another task for InfoGuard: provider analysis
Mrs Tiggywinkle wants to ensure that the IaaS provider, as well as the SaaS provider Carefree AG, has the right level of security. To ensure this, she has commissioned InfoGuard to carry out a provider analysis. In this analysis, the architecture team carries out an assessment of the security awareness of the providers, based on interviews and studying documents. The provider analysis contains the following points, among others:
|
What |
Description of possible points to consider |
|
Architecture
|
|
|
Business Continuity |
|
|
Experience |
|
|
Costs |
|
|
Legal and Compliance |
|
|
Sicherheit |
|
|
Support-Leistungen |
|
Table 2: Potential questions for the provider analysis
InfoGuard’s analysis revealed that both providers have the certifications and security measures required.
IaaS AND SaaS for a future-oriented architectures
Mrs Tiggywinkle discussed the set-up in Table 1 with InfoGuard. At the heart of the discussion was Hedgehog Winter Sleep AG requirement for certain applications and that these could only be available on the market as SaaS or IaaS. As a result, in the future Hedgehog Winter Sleep AG will buy in services that have to be provided based on the IaaS or SaaS operating model.
Mrs Tiggywinkle concluded: “For Hedgehog Winter Sleep AG, committing to just one of the two variants, IaaS or SaaS, as the future operating model due to the current issue for Carefree ERP & PPS is not future-proof." The architecture team took this fact into account when making their subsequent deliberations.
Safety first
InfoGuard AG's core skills – clearly – include security issues. Together with Mrs Tiggywinkle, the architecture team carried out a risk analysis, which resulted in the Carefree ERP & PPS needing a high level of protection. Hedgehog Winter Sleep AG’s chief value turned out to be its in-depth knowledge of how to produce high-quality hedgehog homes using lean manufacturing processes. This means that they can undercut competitors on price. Mrs Tiggywinkle would like to protect this process knowledge mapped in the Carefree ERP & PPS in a particularly effective way. The architecture team looked for ways to fulfil this request.
A security device for the cloud: CASB
Cloud Security Access Broker (CASB) monitors incoming and outgoing traffic to and from the web. There is an InfoGuard blog article specifically on the topic of CASB. CASB increases Hedgehog Winter Sleep AG’s security level:
|
CASB Uses |
Description |
|
Compliance
|
The use of cloud services creates data protection issues such as a provider's geographical location. CASB assists Hedgehog Winter Sleep AG in defining and enforcing data protection policies. |
|
Data Security |
The CASB enables Hedgehog Winter Sleep AG to prevent the transmission of sensitive content. As a result, CASB has functionalities that overlap with Data-Loss-Prevention-Systemen (DLP). However, DLP systems have a broader scope, for example in scanning data files or automatically classifying documents. |
|
Threat protection |
DerCASB enables Hedgehog Winter Sleep AG to protect itself from threats associated with cloud connection via behavioural analysis and malware detection. |
|
Visibility |
CASB monitors Hedgehog Winter Sleep AG's use of cloud applications and produces risk-based reports on the basis of which a decision can be taken as to whether access to a cloud application should be blocked. An additional benefit of this functionality is that any shadow IT present at Hedgehog Winter Sleep AG is also detected. |
Table 3: Use of a Cloud Access Security Brokers (CASB)
In addition to CASB as a specific cloud security device, there are other protective measures that need to be implemented when connecting to the cloud. Clarifications from the provider analysis have proven helpful for the architecture team:
|
Protective measure |
|
IaaS |
SaaS |
|
Administrative access
|
How administrators securely access the cloud environment |
To be implemented by Hedgehog Winter Sleep AG |
Dependent on the offer |
|
Connection to the Hedgehog Winter Sleep AG’s monitoring solution |
Integrate log data from the cloud environment into the Hedgehog Winter Sleep AG’s monitoring solution |
To be implemented by Hedgehog Winter Sleep AG |
To be implemented by Hedgehog Winter Sleep AG |
|
Cloud Access Security |
See CASB description |
To be implemented by Hedgehog Winter Sleep AG |
To be implemented by Hedgehog Winter Sleep AG |
|
Hedgehog Winter Sleep AG established VPN connection to the cloud service provider |
Establish a secure, reliable connection to the cloud provider |
To be implemented by Hedgehog Winter Sleep AG |
Dependent on the offer |
|
Firewalling by Cloud Provider |
Safeguard access to and from the cloud environment |
To be implemented by Hedgehog Winter Sleep AG |
Dependent on the offer |
|
GDPR Compliance |
Take into account the data protection aspects |
Dependent on Carefree ERP & PPS software and IaaS offering |
Dependent on Carefree ERP & PPS software and SaaS offering |
|
Hardware Security Module |
Secure storage of keys, e.g. for encryption at rest or data encryption in Carefree ERP & PPS |
Dependent on Carefree ERP & PPS software and IaaS offering |
Dependent on Carefree ERP & PPS software and SaaS offering |
|
Patching |
Responsibility for patching and deciding who triggers the patching cycle |
Infrastructure via the IaaS provider |
Done by Carefree AG |
|
Redundancy |
Measures for interruption-free operation |
To be implemented by Hedgehog Winter Sleep AG |
Dependent on the offer |
|
Connection protection provided by a firewall by Hedgehog Winter Sleep AG |
Set the firewall rules required |
To be implemented by Hedgehog Winter Sleep AG |
To be implemented by Hedgehog Winter Sleep AG |
|
Data-at-Rest Encryption |
Prevent sensitive data from being viewed by the cloud provider |
To be implemented by Hedgehog Winter Sleep AG |
Dependent on the offer |
|
Certification |
Ensure that information about the cloud environment can be provided during audits, without the need for a separate cloud audit. |
Possible for the infrastructure and how it is operated |
Possible for the service provided |
Table 4: Clarification of IaaS and SaaS protective measures
The breakdown in Table 4 shows that Hedgehog Winter Sleep AG has a wider range of options for action with an IaaS provider than with an SaaS service. On the other hand, the installation, configuration and operation of Carefree ERP & PPS with IaaS requires substantially more effort from Hedgehog Winter Sleep AG than purchasing an IaaS service.
A sound decision
The provider analysis showed that, from a security point of view, Carefree ERP & PPS can be operated by the IaaS provider in a “stretched network” scenario. Hedgehog Winter Sleep AG lacks the resources and skills required to operate Carefree ERP&PPS in an IaaS environment, so Mrs Tiggywinkle selects Carefree AG’s SaaS offering.
Mrs Tiggywinkle would like to see a visualisation by the architecture team so that she can avoid “reinventing the wheel” when more SaaS or IaaS-based services are introduced. It is advisable to publish these architecture blueprints on the intranet so that current and future projects and employees can use them for guidance. In practice, this saves time and stress.
Blueprint connection of the SaaS provider
Figure 5 shows the setup in the SaaS model. Hedgehog Winter Sleep AG and Carefree AG are connected to each other via two firewalls and the Bastion Virtual Network by means of a VPN connection. A decisive factor is that the traffic between Hedgehog Winter Sleep AG and Carefree AG is routed via the entry zone and the CASB located in it. Carefree AG’'s SaaS environment is a black box to the outside world.
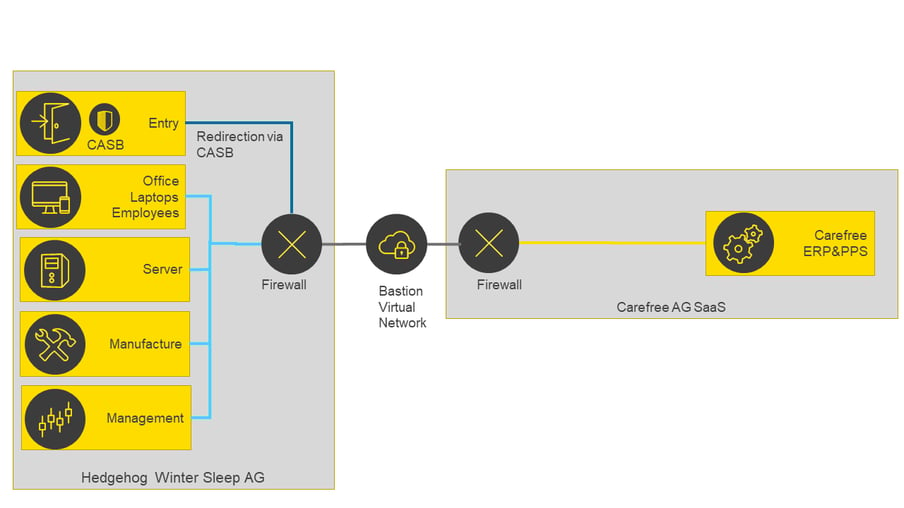 Fig. 5: SaaS connection
Fig. 5: SaaS connection
Mrs Tiggywinkle also wanted to see architecture blueprints for any future Hedgehog Winter Sleep AG connections to an IaaS provider, so the architecture team provided some additional (next-step) graphics.
Blueprint connection of the “stretched” IaaS provider
The setup shown in Figure 6 is more complex due to the fact that Hedgehog Winter Sleep AG is running the Carefree ERP & PPS software itself in the IaaS setup. The stretched networks for manufacturing, server and management, which extend across Hedgehog Winter Sleep AG and the IaaS provider, can be clearly identified here. Once again, traffic between Hedgehog Winter Sleep AG and the IaaS provider is redirected via the entry zone and the CASB.
 Fig. 6: IaaS connection Stretched Network
Fig. 6: IaaS connection Stretched Network
Blueprint connection of the IaaS provider “black box”
An IaaS provider can also be connected as a black box. This method, as shown in Figure 7, could be used if only a single application is operated on the IaaS platform or if there are concerns about stretching the on-premises network to the IaaS provider. Traffic between Hedgehog Winter Sleep AG and the IaaS provider is redirected via the entry zone and the CASB.
 Fig. 7: IaaS connection as a black box
Fig. 7: IaaS connection as a black box
IaaS or SaaS as a service model: to summarise
The following points have to be borne in mind when connecting infrastructure as a service (IaaS) or software as a service (SaaS) to a company:
- The IaaS setup gives a company more freedom, but it is more complex.
- With SaaS, the service provider stipulates a lot, but there is less complexity. It is crucial for the architecture design to clarify in advance which model is the right one for a company.
- With good architecture, it is possible to integrate different operating models (IaaS Blackbox, IaaS “stretched”, SaaS) at a later date.
- Do not lose focus: The important thing is what the network is supposed to achieve in the future and what protective measures are to be put in place to do this based on the risk analysis.
- Deciding to implement either a demarcated environment or a stretched network is dependent on a range of factors including:
- Whether just one service will be operated in the IaaS environment
- Whether there is enough confidence in a cloud provider’s security measures to stretch the on-premises-network to the cloud provider
- Whether the available resources and skills within the company
-
- Whether the company is already using an IaaS platform.
Should we be providing you with support?
The answer to the question whether to choose IaaS or SaaS is a more or less obvious one, depending on the customer. When in doubt, our customers appreciate a well-founded (second) opinion, because the decision taken has a long-term impact for the customer. InfoGuard has the following offers ready for you:
- Architecture reviews focusing on security: Assessment of existing or planned architectures (cloud, on-premises, hybrid) focusing on security.
- Facilitation of workshops to clarify outstanding issues
Our experience from past customer projects means we can assess what the best target-oriented solution for your needs would be. Our architecture team is looking forward to working with you!
1) In the cloud environment, shared responsibility is understood as being the joint responsibility of the cloud service provider and the cloud service recipient. Individual areas such as operation and patching can be the responsibility of the cloud service provider, the cloud service subscriber or both of them.
2) For example, irrespective of the different login IDs on the systems used, all of User A's transactions are normalised so that the transactions can be queried as a whole.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


