Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
Continuously assessing the risks that affect your OT and IoT systems

Operational systems that are central to value creation and revenue have become more important than ever. It remains a challenge to protect these systems from the ever-evolving threat landscape, as cyber criminals often target these highly critical infrastructures and industrial systems. In its current OT/IoT Security Report, our partner Nozomi Networks provides an overview of the most important threats and vulnerability trends of recent months. We have summarised the most important findings in the following blog article.
Supply Chain Threats and Vulnerabilities
In 2020, one of the most significant cyberattacks was the attack on SolarWinds. The result of the supply chain attack was that thousands of businesses, mainly based in the US, were infected. It was a sophisticated cyberattack that compromised a SolarWinds network monitoring product used to manage IT infrastructure. Government agencies, critical infrastructure operators and manufacturing companies were all among the victims of the attack.
Although cyber criminals had just selected a few targets at SolarWinds, all those organisations infected were faced with the major challenge of cleaning up their networks as quickly as possible. The example shows that the cyber criminals very specifically chose widely used software to attack the supply chain. This also demonstrates how important cyber security is throughout the entire supply chain and the risks associated with it.
Another type of supply chain threat is embedded component risk, as has been shown by the example of Ripple20 vulnerabilities. Ripple20 consists of 19 vulnerabilities identified in Treck's TCP/IP stack. At the time these vulnerabilities were disclosed, there was great concern about the risks they posed to IoT devices. Later it became evident that the probability was low, as many targets did not meet the requirements that motivated cyber criminals would require to exploit them.
Ransomware attacks are reaching a whole new dimension
Persistent ransomware attackers are dominating the threat landscape and they target companies they believe can pay lucrative ransoms. When they do so, not only do they demand financial payment, they also extort those companies targeted by threatening to release data and information about the compromised networks, to be used for future activities.
Ransomware criminals are also becoming more and more sophisticated, and there are more of them using different combinations of strategies and threat vectors. One example is the Ryuk ransomware group, which it is estimated is responsible for a significant proportion of all the ransomware attacks carried out in 2020. The following figure shows the Ryuk attack kill chain: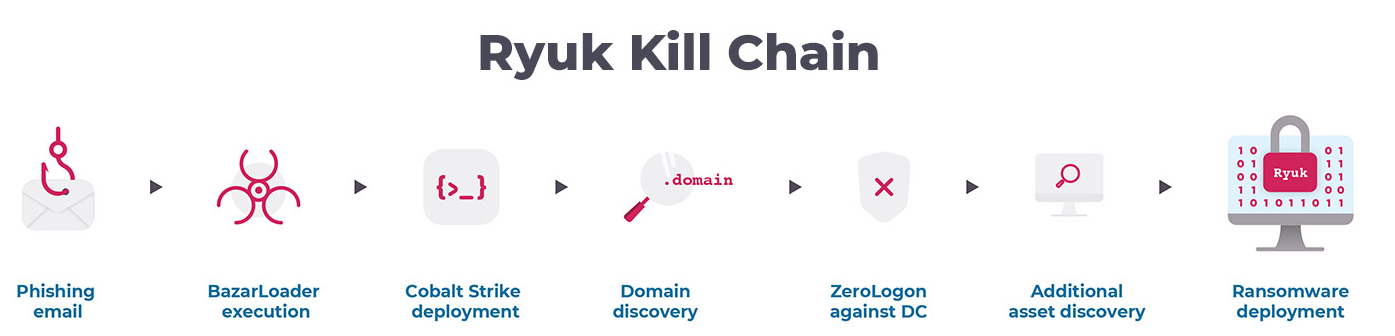 Figure 1: Ryuk kill chain (Source: Nozomi Networks, OT/IoT Security Report 2021)
Figure 1: Ryuk kill chain (Source: Nozomi Networks, OT/IoT Security Report 2021)
How can you safeguard your OT/IoT environment?
In a threat landscape where ransomware organisations are attacking targeted businesses, it is crucial to understand which vulnerabilities are being actively exploited. It is worthwhile continually improving your own cyber resilience and assessing how the measures you have put in place are performing against key emerging threats. Organisations should be focusing on identifying unpatched software and implementing update or mitigation policies. Attack surface reduction and network segmentation are two proven methods for reducing risks in the supply chain. Furthermore, the monitoring of OT and IoT networks using key technology is essential to help define the attack surface and detect anomalous activity that indicates an advanced threat. Our partner Nozomi Networks is one of the leading companies in OT and IoT security and transparency. Nozomi Networks' innovative use of artificial intelligence (AI) provides OT visibility, threat detection and insight into thousands of the largest critical infrastructures and industrial sites around the world, all in a single solution.
The OT/IoT Security Report recently published by Nozomi Networks summarises the most significant threats and risks for OT and IoT environments, to enable you to understand the current threat landscape better and faster. Also included are ten recommendations of ways to improve protection against this threat landscape. Download the full report now:

Now is the time to re-evaluate your OT/IoT systems attack surfaces and reassess the risks within your supply chain. Our cyber security specialists will be delighted to advise you on Nozomi Networks products. Contact us now! .
.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant
