Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
Cyber Risk Monitoring – keeping an eye on your cyber risks!

Managing cyber-risks is becoming more and more important. We told you about it in a previous blog. Cyber risks are ever-present, and they affect not just your business, but also your customers, partners and suppliers. Furthermore, cyber risks are highly dynamic. In this blog post, you will learn how you can maintain an up-to-date picture of your cyber risks.
Cyber risk management helps you identify threats and risks in advance, deal with them and proactively define the actions and measures that need to be taken if an incident occurs. All the same, many companies still underestimate the general level of cyber risk.
Cyber risk management is a challenging task
We realise that there are multiple challenges in tackling cyber security risks. In our daily consultancy work, we repeatedly come across four fundamental difficulties related to this:
- The lack of resources and/or tools
- The challenges involved in systematically assessing and monitoring risks
- The large number of people and third parties who are impacted
- The organisational challenges in implementing and checking security targets
So it is no surprise that companies resign themselves to what they assume is all the effort involved, and ineviatbly cyber risk management degenerates into a one-off – which can be very dangerous!
Cyber risk monitoring as an important component of cyber risk management
Everyone who is running a business knows that the economy is constantly changing and companies have to react to the changing circumstances. On top of this, a company's risk tolerance may also change over time. Therefore, your risk analysis must also be permanently checked for its relevance and coherence, so you need to be permanently (or at least regularly) monitoring your cyber risks and, where necessary, adapting your risk strategy (reducing, accepting, outsourcing, etc.).
Cyber risks are dynamic
Unfortunately, cyber risks are not static situations, they are highly dynamic events. That is why it is crucial to keep an eye on cyber risks at all times, because:
- General conditions change
Initial cyber risk analysis is carried out under specific framework conditions. If these change, the risks also need to be reassessed, and today’s business world is extremely fast-moving, so this needs to be done on a regular basis. - The likelihood of events changes
The initial risk analysis is based on the current situation and the information available at the time, and probably it is already outdated by now. A cyber risk that was originally considered to be very unlikely can suddenly become a higher priority. But the opposite situation can also occur. If the probability of an event occurring changes, this will almost certainly have an influence on the prioritisation of the measures planned. - Measures have to be implemented
If you have developed measures from the initial risk analysis to minimise your cyber risks, that's great! Unfortunately, these do not just take care of themselves. Cyber risk monitoring also includes checking whether the measures have been implemented effectively. Particularly when the responsibility for implementing them has been delegated to others, it does not hurt to check on how things are progressing. - Impacts need to be analysed
Even where all measures have been implemented as intended, this does not mean that cyber risks have actually been minimised, so as part of cyber risk monitoring you also need to check whether the measures’ impact matches expectations.
Cyber risks do not recognise corporate boundaries
Cyber risk management and the monitoring associated with it are therefore important aspects of a company's overall security system. However, you cannot treat cyber risks separately from your business environment, which is why we strongly recommend that you also include your third parties, such as partners/suppliers, in the cyber risk assessment to the extent that this is relevant and appropriate. Third party management is an important stage and focuses on identifying and managing cyber risks to external third parties (i.e. partners, service providers, hardware and software suppliers, outsourcing providers, cloud service providers, etc.). By implementing cyber security requirements in formal contracts, risks should be managed in a targeted manner. For example, supply chain management has grown in importance in recent years - especially in terms of addressing aspects of information security. The only way to obtain the transparency needed on cyber risks and cyber security maturity within the supply chain is to consciously extend your own risk management and cyber security to your suppliers.
Whitepaper: Cyber Risk Management
We are well aware that cyber risk management and monitoring current cyber risks is a real challenge. In this white paper, you will learn how to set up a good, efficient cyber risk management system. We have also put together some important points and tips for implementing a realistic cyber risk management system. Good luck with implementing it!
Do you know your digital footprint and the cyber risks associated with it?
A clear, up-to-date overview of your essential cyber risks is a major challenge, but it is also the prerequisite for effective cyber risk management. Increasing dynamics and changing assessments have a significant impact on your company's risk exposure. We can help you with this – have an up-to-date view of your cyber risks at all times with our Digital Footprint Risk Monitoring Service. With comprehensive analysis functions, you and your company get a detailed insight into the vulnerabilities in your infrastructure and do so from the perspective of a potential attacker. Moreover, our cyber security experts are available to you with advice and support to analyse your risk landscape, show you the relevant cyber risks for your company and suggest the appropriate security measures. The best thing is that with our platform, not only do you have your own company covered, but this cover can also be extended to your partners and suppliers, which means that you have solved three of the four challenges described above at the same time.
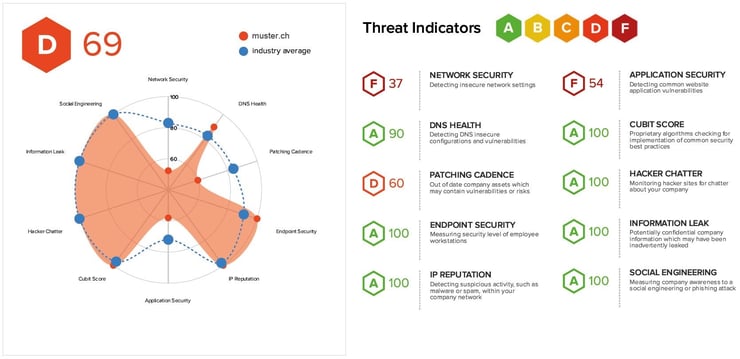
Our Digital Footprint Risk Monitoring Service helps you identify your security risks and enables you to manage them and report them transparently (at any time). We would be happy to show you the options available in a personal consultation – contact us with no obligation, or find out more about our service on our website:
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant



