InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
[Alert] InfoGuard CSIRT issues a “malvertising” warning

Malvertising & SEO poisoning – is this a new trend?
In itself, this scam is nothing new. It was already known back in the day when LimeWire and Co. were around. It is almost definite that anyone who downloads stolen software online will be infected with a virus. Even before there was an Internet as we know it today, it was not just Doom and Day of the Tentacle that were traded when games were traded on floppy disks, as the first computer viruses also found their way into distribution channels this way. But what is relatively new is that attackers are running Google ads that offer legitimate software, which is then downloaded from the internet by thousands of users every day from fake websites, and it includes Trojans.
However, malvertising and SEO poisoning are really nothing new. In summer 2022, our CSIRT had already issued warnings about cases of fraud where login pages for popular e-banking portals had been forged and phishing pages were being promoted via Google advertising. In malvertising, the rogue pages are disseminated on platforms by means of paid advertising. On the other hand, SEO poisoning involves the attackers trying to position popular search terms like “iPhone X instructions” or “summer holiday packing list” nearer the top of the Google ranking, by cleverly planting contaminated PDFs that are linked to each other over and over again – something which Google likes. The aim here is to make it easier for users to land on phishing pages. The advantage for SEO poisoning is that this tactic also works even when the ad blocker is active. However, it costs a lot more than paying a Google a couple of hundred dollars to be listed above the real search results.
Quickly download WinRAR
In the past few weeks, InfoGuard CSIRT has detected several campaigns that “poison” search queries for popular software products by providing links to their malicious websites:
- WinRAR / 7-Zip / WinZip
- AnyDesk / TeamViewer / Splashtop
- Blender / GIMP
- OpenOffice /LibreOffice
- Audacity / VLC Player / KMPlayer
Over the next few weeks, the list will probably get longer.
Here, users want to unpack an archive and download WinRAR. After a Google search, they can see the following results:
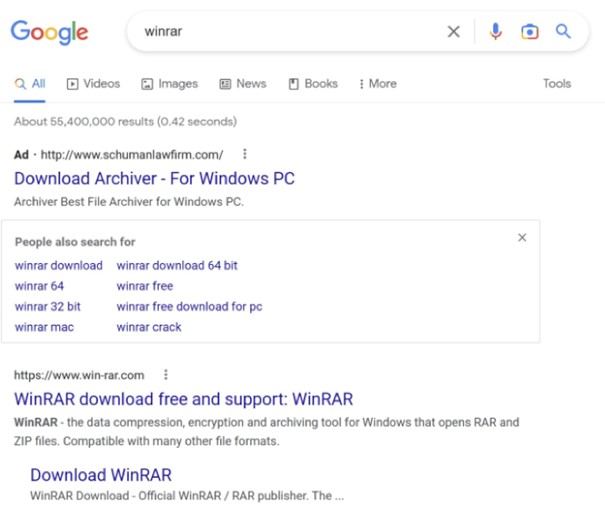
The first link is a paid advert that leads to what is known as a collection or sinkhole page, which has very probably been hacked. Here, the hackers have created an automatic redirection to their perfect copy of the WinRAR page:

The download then takes place via another website. The advantage of this is that the link to the download can easily be switched if the target site is taken offline due to malware being distributed. (After all, costly advertising shouldn’t be done for no reward. 😉)
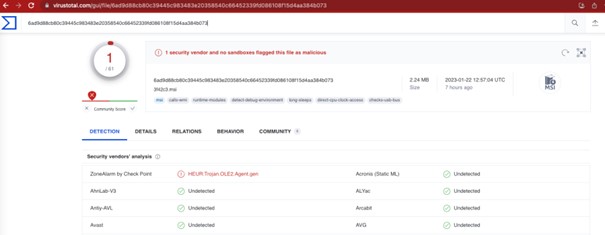
As expected, the downloaded file is a Windows Installer (MSI), and has not yet been actually detected by VirusTotal.
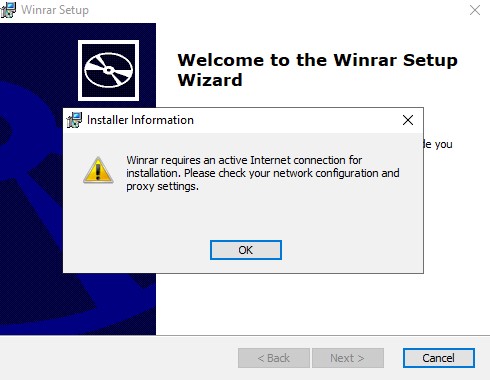
However, what is interesting is that the installer needs an active internet connection. This is not true of the original WinRAR – and it is not required unless you are looking to infect the computer. Alongside the installation of WinRAR, a PowerShell script is secretly started in the background, and this installs a malicious DLL file and creates a scheduled task that regularly executes the malware at set intervals.
How do I go about protecting my business?
We are right at the start of malvertising and SEO poisoning, so we will probably be having to deal with frequent cases like these in the months (and years) to come. This means that it is really worth thinking about how to protect yourself against attacks like these, both at work and at home. As is usually true with related security issues, the best way to start is to increase awareness:
- Share this post with other people to grow the security awareness of your employees, colleagues and family members by highlighting the issues of malvertising and SEO poisoning.
- Make the issue part of your awareness programme.
- Restrict what your employees can download and run on their workstations.
- Check that ad blockers are in use (but please, still take great care about what you download).
- Only download software from known sources. When you download software, we recommend that you always go to the manufacturer's website.
- Use EDR/XDR (Endpoint Detection & Response).
- Use sandboxing technology on a proxy server or endpoint.
- Use Applocker / Windows Defender Application Control to block unknown software.
- Block proxy categories such as adware, greyware and topical threat feeds, as well as things falling into the “uncategorised” category.
- Implement a Managed Detect & Response service in order to detect and eliminate this kind of threat in a timely manner.
Blog

Agentic AI on the Attack: How Human-AI Teaming is realigning Cyber Defense

Zero Trust 2026: These 4 steps work in IT, OT & cloud-first

