Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard CSIRT is warning of e-banking fraud

In recent weeks, InfoGuard's Computer Security Incident Response Team (CSIRT) has uncovered multiple recent fraud sites for Swiss banks' e-banking systems. By working together with the Swiss National Cyber Security Centre (NCSC), on one hand we have succeeded in issuing a proactive, coordinated warning to the banks concerned. On the other hand, we immediately informed the companies about what measures to take to successfully remove the copied, fake websites. In this article, our principal cyber security analyst Stefan Rothenbühler shows you in detail how these malicious attacks, which seem to be targeting Swiss banks' private customer accounts, work and how to protect yourself effectively.
Google Ads as an entry portal
There are still many fake websites on the internet. These sites are aimed at getting customers to enter their personal data. The various attacks on prominent Swiss banks in recent weeks have all followed the same pattern – the bank's e-banking service website or landing page has been almost completely copied like for like, and it is then set up under a new, fake domain that at first glance (and unfortunately also at second glance) looks very similar to the bank in question.
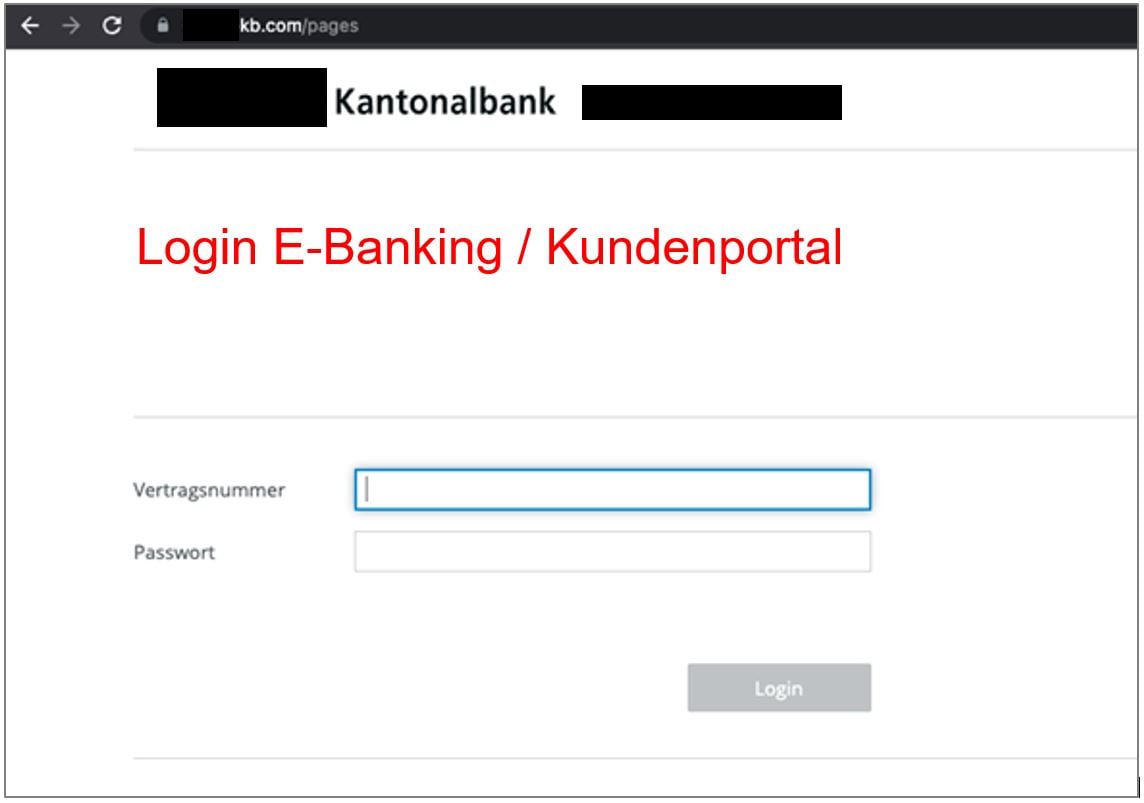
Fake landing page for e-banking login (anonymized example)
But the climax of the attacks – at least from the attackers' point of view – was still to come. The attackers used a very clever method of luring unsuspecting victims to the fake e-banking login page. They used Google Ads, by far the most popular SEA (Search Engine Advertising) system in the world. Or to put it another way, they placed advertisements in such a way that the fake pages were displayed even before the actual search results were shown. The chance that unwitting victims would click on the search results that appear right at the top has now been established. Nowadays, the URL fields in the browser are constructed in such a way that the character strings entered are automatically searched for via the stored search engine – and in the vast majority of cases, this is Google. It is quite usual for a lot of people to be so comfortable that they use this. To make matters worse – and unfortunately I am still hearing this all too often from the people around me – they do not enter the actual URL, they simply type the words “e-banking” and the name of the bank into the address field, then rely on the Google results that pop up. This should never be done under any circumstances, particularly given the sensitive nature of data and services such as e-banking.
We recommend that you always check the URL very carefully and only open your trusted bank’s e-banking service via its official website.
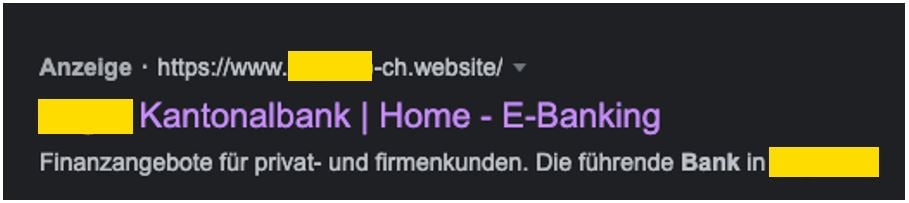
Fake ad made to look like a Google ad
To illustrate this more clearly, we have shown you an (anonymized) example of this kind of fake Google Ad. The cantonal bank, which incidentally reacted very quickly to the warning from our CSIRT experts and immediately posted a warning for its customers on the e-banking login page, is only one example. In Switzerland, several banks have been affected by these treacherous, highly professional attacks in the course of the last few weeks.
Effective protection against online banking fraud
Now, the burning question – how do you go about protecting yourself from attacks like these? In this article, we would like to take the opportunity to show you the most effective measures for protecting against fraud in online banking, both from the point of view of end customers and e-banking service providers.
Protection for end customers
Users of e-banking can protect themselves in the following ways:
- Always enter the full URL of the website you want in the address field, and do so independently. Do not search using Google.
- Alternatively, only open your e-banking provider's login page from the relevant bank's official website, or save the URL in your favorites.
- Use a separate user profile in your Windows for e-banking, or at least a separate browser – or use the incognito mode.
- If the second factor query takes longer to load (PhotoTAN, etc.), we recommend that you close the session and restart it in a new browser window.
- Never click on links that you are sent via e-mail. There is a very high risk that they are phishing e-mails, particularly in this sector.
Protection for e-banking services providers
As a bank or a provider of e-banking services, you can also take measures to protect your customers. These include:
- Making sure that adding new devices for PhotoTAN can only be done via letters sent in the post.
- Having your e-banking domains checked and monitored for the registration of fake domains with Typosquatting Monitoring.
- Examining your web server logs for unusual referrals. The attackers often include images directly in their fake websites or forget to replace the links.
- Checking your e-banking web application logs for sessions that have a longer duration between password entry and PhotoTAN confirmation.
- Checking e-banking accounts for newly added PhotoTAN devices.
You can find more interesting information about cyber security and cyber defence specifically intended for banks and financial service providers in this free brochure.
Cyber Threat Intelligence Services
For e-banking service providers, it is crucial to identify threats to your company, networks, systems, applications and services early on. Our InfoGuard Cyber Defence Center security analysts will be pleased to provide you with support and deliver concrete recommendations for effective countermeasures on one hand, and important insights for targeted prevention, defence and response on the other.
Are you interested? Or specialists are looking forward to hearing from you. Simply enter the keyword “Cyber Threat Intelligence Service” in the form. We will contact you immediately to assess your individual needs and provide you with the best possible support.
Blog

Incident Response Planning (IRP): Gut vorbereitet, stark im Ernstfall

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen



