Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
Advent, Advent, the school is “burning”! [Part 2]

In the first part of our three-part Advent story, we found out that Winterstadt school had fallen victim to a cyber-attack – it was the LockBit 3.0 ransomware. Last time, I asked you why a state school could be of interest to cyber criminals at all, because as everyone knows, there are far more lucrative targets around than that. Well, have you got any ideas? In this part of the cyber Advent story, I'll tell you what happened.
At the same time as I was making contact with the attackers, my colleagues were checking the systems in the background, and they were quickly able to establish that it was very likely due to remote access being misused to access the systems. Yet again, this had not been safeguarded by means of MFA (multi-factor authentication ), making it child’s play for the attackers. It also transpired that most of the data was able to be retrieved from backups. Only the staff members’ personal drives had been irrevocably destroyed. Now you are probably asking yourself whether to pay or not to pay? The amount demanded was a six-figure sum, so paying was not really an option, especially for a school...
The majority of the data could be recovered, so the more pressing question was what consequences of the threatened publishing of data would mean for the students and teachers. Working together with communication experts and the local police, as a precaution letters were prepared for people who might be affected, because if data is actually going to be published on the Darknet, this has to be done quickly!
Even cyber-criminals have to do their homework
Let’s go back to the attackers and the issue of why encrypting a state school seemed to be profitable for them. As it quickly became clear, the attackers had not done their homework very well, by which I mean that they calculated the ransom demand and maybe even the attack itself working on the assumption that the victim (the school) was a company with an annual turnover of 10 to 25 million Swiss francs.
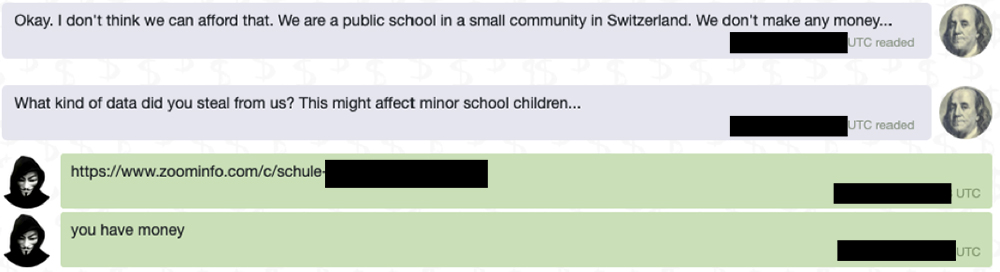
Of course, we did not try to withhold this fact from the attackers, and we pointed out to them that these were probably “not the droids they had been searching for”.

When they gave the answer “make your offer to us”, I realised that it was dawning on the blackmailers that they had probably made a mistake with this attempted blackmail.
Do cyber criminals have a conscience?
We were just as curious as you probably are about what the blackmailers’ reaction would be. In the third and final part of our three-part cyber Advent story, you will find out how we were able to use this situation to our advantage, and whether school could continue as normal after the half-term holidays. If you don’t want to miss out on this and our Advent competition with great prizes, just subscribe to our blog updates!
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


