Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
2-Factor-Phishing – the “Man-in-the-Middle” Attack
2FA (2-Factor-Authentication) is standard practice today – whether it's for online banking, e-mail accounts, virtual desktop infrastructures (VDI) or social media accounts. However, 2FA is no panacea, and there are now applications that can act as a man-in-the-middle to crack 2FA and facilitate 2FA-phishing. Read more about this in my current blog article. My name is Lukas Reiter and I am a Senior Cyber Security Consultant / Penetration Tester at InfoGuard.
“Old” Phishing Tactics
Phishing is one of the most popular, successful methods of attack. It involves sending fake e-mails or imitating them from legitimate senders, or creating HTML templates that are dressed up as lookalikes of login pages from popular websites. Users are then tricked into revealing their usernames and passwords. When the user enters their username and password, the login details are logged and the attack is considered to be a successful one.
To present the attacker with an additional obstacle, 2FA has established itself as a secondary protection factor on login pages. If the victim has 2FA enabled on their account, the attacker needs an additional form of authentication on top of the username and password they have intercepted via phishing. This additional form of authentication can be a text message code sent to the mobile device or a PIN that remains valid only for a limited time. An attacker without access to one of these options will not be able to successfully authenticate and log into the victim's account. Phishing methods that focus solely on acquiring usernames and passwords are completely defeated by 2FA.
2FA-Phishing using Man-in-the-Middle Attacks
The logical consequence of this is for attackers to adapt their phishing tactics so that they can successfully bypass 2FA and, consequently access the web application again in the victim's name.
To understand these new tactics, it is necessary to take a brief digression into the authentication process for web applications, as illustrated in the figure below:
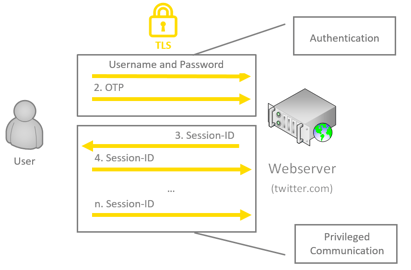
Figure 1: Web authentication with 2FA
First of all, the user is authenticated: in the web application, the username and password are entered, as well as the one-time password (OTP), e.g. a text message code or the PIN from the security app. As soon as the authentication is successful, the webserver issues a unique, confidential session ID for the user. Based on this session ID, the web application is then able to identify on the server-side which incoming HTTP request originates from which user. If an attacker can successfully steal a session ID, they can perform any action in the affected username in the web application. This is also referred to as a session hijacking attack.
For the attacker, this session ID or token is pure gold, as they can use it to control everything. So how is it possible to intercept the session ID remotely without having any physical access to the victim's computer?
Provided the user communicates directly with the actual web application via an encrypted channel (HTTPS), the attacker has no way of reading the communication. As before, however, the attacker can send the user a phishing email and ask the user to call up a special web application controlled by the attacker. The following illustration shows how this works:
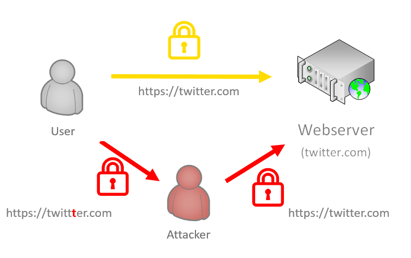
Figure 2: 2FA-Phishing using Man-in-the-Middle/Session-Hijacking Attack
When the communication reaches the attacker, they can capture the data that the user enters as a man-in-the-middle, and forward it simultaneously to the real website in real-time. This is how attackers not only get the login data, but with 2FA, much more importantly, they also get the session tokens.
Today, there are even applications such as Evilginx2 that take on the role of the attacker. Evilginx2 is an attack framework for setting up phishing pages. Common phishing attacks rely on creating HTML templates, which take a lot of time to create. Most of the work involves making them look good, responsive on mobile devices, and properly disguised to circumvent phishing scanners. Instead of creating templates of login page lookalikes, Evilginx2 acts as a relay between the real website and the user. The user interacts with the real website while Evilginx2 captures all the data that is transferred between the two parties. Every packet coming from the user's web browser is intercepted, modified and relayed to the real website. The same happens with response packets originating from the website. They are intercepted, modified and sent back to the user. With Evilginx2, there is no need for the attacker to create their HTML templates. On the user's side, everything looks as if they are communicating with the legitimate website. The user has no idea that Evilginx2, as man-in-the-middle, is analysing every packet and logging usernames, passwords, OTPs and, of course, session tokens.
It is possible to fake any web-based login page that asks the user to enter their password and that has some form of 2FA implemented, using this technique! I showed the practical illustration of this in my presentation at the InfoGuard Innovation Day 2021 on the subject of 2FA-phishing (only in German available).
How can you protect yourself?
To implement appropriate countermeasures, first of all, it is essential to understand what kinds of threats 2FA can protect against. Primarily, 2FA ensures that if valid credentials become known (e.g. via what are known as password leaks or the “old” phishing tactic), they cannot immediately be misused by attackers to gain unauthorised access to web applications. However, as we discussed in this blog article, 2FA does not protect against 2FA-phishing via a man-in-the-middle/session hijacking attack.
Web applications should employ active preventive measures to increase the complexity of successful session hijacking attacks. In the simplest case, this can be achieved by binding the session IDs on the server-side to the user agent string of the web browser used by the user and the user's public IP-address. However, this measure does not offer any protection against attackers with greater maturity, since the attacker can read the user's entire web communication anyway due to the man-in-the-middle attack, and consequently has all the information at their disposal to successfully bypass this protection mechanism.
To effectively mitigate the risk of a successful phishing attack on 2FA, it is essential for there to be user awareness. This means that employees should recognise phishing attacks and know which methods can be used to trick them. We have created a useful poster for you – download it free of charge now. You should also carefully check whether the website you are accessing is an authentic one. InfoGuard can assess your employees' security awareness using a targeted check, as a one-off audit or as a continuous service. Then a simulation of phishing and malware attacks can be tested and analysed in detail.
Contact me now. I will be happy to give you an individual quotation.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


