InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Zero Trust – take care in whom you trust

This probably sounds very familiar to you – dashing from your home office to meet the client, then on to a meeting in the office, and rapidly answering a few e-mails on your way home. Your notebook and smartphone are connected to the Internet everywhere you go, and being available at all times is virtually an obligation. However, behind the scenes, working like this can have unexpected side effects.. We will show you what they are, and how to counteract them.
All devices, especially ones that are used outside the limits of the company to connect to the Internet, could be infected by malware. This also applies to your clients or, for instance, a co-working space, because you cannot be sure how conscientiously IT security is implemented there.
Why you are not secure within your own four walls
Do you connect your notebook to your home Wi-Fi? Almost certainly. Even if you are using a VPN (Virtual Private Network) to connect to your employer's network, your device will still be visible within the home network, e.g. by the convenient media server NAS (Network Array Storage) which you use to view your photos and share them with friends via a link or web browser. The same goes for the TV box and your TV. None of this is a problem as long as the various components are secure and protected against external access.
But, can you say for certain that all the individual components are secure and that you have them all under control? If not, you need to configure your device (or have it configured) so that it can protect itself to the maximum extent possible and that it complies with your company's security guidelines, for example:
- Disable the option of exporting shared folders.
- Disable display as a network device.
- Use security software (anti malware) that detects suspicious behaviour and malware and blocks any unauthorised access.
- Activate the firewall on the notebook and allow only mandatory access.
- Regularly patch all components.
- Protect your Wi-Fi with a strong password.
These examples show that when you are working on a networked computer, you should be prepared for all eventualities and never blindly trust anyone – not even your home network. This is where Zero Trust comes in to play!
Zero Trust – the thing about trust
Trust is the basis for a successful collaboration, right? But hold on – trust can be exploited. Have you already heard about cyber attacks that exploit the willingness of employees to help out, for example, phishing? One response to this is the “Zero Trust Model”. In this model, the assumption is that trust is a risk, so according to Zero Trust, nothing can be trusted, both outside and even inside the company. Instead, every single access to the company system needs to be checked for its trustworthiness. Blind trust in “resources” such as hardware, data sources and services is a vulnerability. The following points demonstrate why Zero Trust is so important:
- Infrastructures, systems and networks are inherently not trustworthy. If these resources are used, the system needs to protect itself as if it were under continuous attack. There is no such thing as a trust advantage for resources that are operated on the premises or in cloud services from known providers.
- Not all devices on the network are owned or configured by the company. Employees, visitors and service providers bring their own device (Bring Your Own Device – BYOD) using the guest Wi-Fi or connect from their home office via their own router.
- But even employees who can access the company remotely cannot unconditionally trust the local network they are on, so all access should be authenticated and encrypted.
Consequently, no users, devices, services or configurations can be intrinsically trusted. Every device must be authenticated before it can be allowed to access a resource.
So what does Zero Trust look like in practice?
The principles described above may sound reasonable. But you are probably asking yourself how to implement Zero Trust in practice. Based on NIST (National Institute of Standards and Technology) according to the draft “Zero Trust Architecture” these are the important points:
- All data sources and services are resources. A network is made up of different kinds of devices such as mobile devices that are used to access corporate resources.
- Being present in the “trusted”network does not imply “trust”. Access from the internal and external network and the Internet must be checked the same way. All communication must be authenticated and encrypted.
- Policies are in place to control access to resources. These includes, for example, user identity, the account used and the status of the device used to access resources. As well as this, the latest behaviour pattern of users requesting access is compared with their normal behaviour.
- Access to resources is granted via a connection. Checks are carried out before access, but gaining access to one resource does not automatically grant access to others.
- “Least privilege” ensures that only the minimum rights required to access the resource are granted. The check carried out depends on the needs of the company and the risk-level it is willing to accept.
- It must be ensured that systems that monitor the company or its suppliers are also secure and are checked regularly. As well as this, all systems where vulnerabilities are identified must be prevented from accessing resources.
- Authentication is a dynamic, strictly enforced process. Zero Trust implies a continuous cycle of accesses and authentications, as well as the detection and assessment of threats, and the resulting and existing measures. Users are managed and authorised via a system which includes MFA (Multi-Factor Authentication) and periodic re-authentication for new, expired or changed resource accesses.
The concept of Zero Trust is mirrored by the architecture derived from it. The PEP (Policy Enforcement Point) forces all resources to be authenticated by a trusted source – the PDP (Policy Decision Point). Possible policies are:
- The roles and role groups assigned to a user.
- The status of an endpoint: This includes a malware scanner (current and active), the current OS, installed software, supported authentication mechanisms, the location of the endpoint, etc.
- Behavioural patterns like the times a user logs in. For example, the different geo-locations of logins must be plausible in terms of the local time and typical user habits.
- The method of authentication depends on the risk assessment and the sensitivity of the resource that is being accessed.
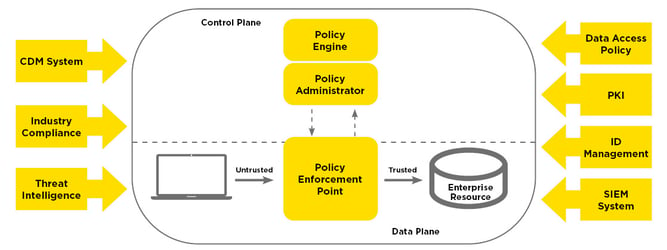 Figure: Elements of a Zero Trust system. In this illustration, the policy decision is divided into the policy engine and the policy administrator. (Source: Draft NIST Special Publication 800-207 “Zero Trust architecture”).
Figure: Elements of a Zero Trust system. In this illustration, the policy decision is divided into the policy engine and the policy administrator. (Source: Draft NIST Special Publication 800-207 “Zero Trust architecture”).
Various tools are available to implement these Zero Trust principles in IT systems:
- Security tools: for example anti malware, to detect malware and prevent undesirable access.
- NAC (Endpoint Protection and Network Access Control): First step is to identify an endpoint's status. The endpoint is only granted access to the network if the status – based on a comparison of the current vs. the desired status – delivers a sufficient score. The device must also be authenticated in compliance with the guidelines.
- Firewalls: they must also be able to handle dynamic resources such as containers.
- Log collectors and SIEM tools: Direct monitoring or connection to a SOC (Security Operation Center).
- IAM (Identity and Access Management) tools: user management, provisioning and auditing.
- Encryption between endpoints (end-to-end encryption), platforms for secure data exchange, secure e-mail solutions, etc.
- Key Management and secure storage of keys in HSM (Hardware Security Modules).
- Security Awareness training: creating employee awareness, for instance, about the dangers found in home networks.
- Document classification and data protection based on it (rights management).
The tried and trusted moat – is this the IT security model of the past?
The image of the castle with the moat and the drawbridge, the inner and outer fortifications and then the tower, has become ingrained in the security industry, and it implies that building the highest possible protective walls is the best means of protection.
The Zero Trust model challenges this concept because resources are no longer just located within the castle. Maybe the more accurate model is the image of an agile, armoured vehicle. It could be inside the castle, but it doesn't have to be.
However, anyone who thinks that the analogy of a moat and walls as security “defense in depth” is obsolete, as this could be interpreted to some extent, is mistaken. Defence in depth is a useful, important add-on in achieving maximum security when used together with Zero Trust.
Zero Trust – not a model for beginners
Zero Trust is not rocket science, but it is complex enough for people to be easily overwhelmed. Still, sooner or later you will not be able to avoid implementing this model. But how?
Our cyber security experts have the knowledge and experience you need to advise you on all aspects of Zero Trust architecture – from strategy to implementation, including the right products. We look forward to hearing from you!
Blog

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first

VM-basierte Evasion: So erkennen Sie Angriffe trotz XDR Blind Spots


