InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Why your suppliers can pose a threat to you and why supplier risk management is so important

What do many of the hacks and data thefts in recent times have in common? The point of entry, which was successfully exploited by the attackers, was not the companies that were directly affected. In many cases, the security vulnerabilities emanated from suppliers, partners or other external service providers. Events such as these are not isolated cases; they are a common scenario when investigating successful attacks. Using illustrative examples, we will show you why supplier risk management must include IT security, an absolutely essential factor in the modern, effective management of cyber security risks, as well as which solutions can help you.
Several surveys (see e.g. Risk Management Monitor and Infosec Institute) conclude that at least 60% of recent IT security incidents were due to suppliers, partners or former employees. This figure demonstrates how important it is for you as a company to also be taking into account the IT security risks of your suppliers and service providers.
4 typical challenges of Supplier (Security) Risk Management
There are many challenges involved in evaluating suppliers, yet they present important reasons for dealing with supplier (security) risk management today:
- The first challenge is selecting potential suppliers. It is almost impossible to get all of the (theoretically) required information concerning their IT and internal processes. As well as this, very few companies - mainly due to efficiency and cost-related reasons - can get a detailed picture of the IT security of a potential supplier up front.
- An assessment of this kind can still be managed with just a limited number of suppliers with a realistic amount of effort, and their security requirements and processes are usually less complex than with bigger companies. However, the time needed for supplier risk management increases drastically as the number of service providers increases. This is quite normal in our highly globalized world - or maybe you can still count your suppliers on two hands. All the same, due to its complexity and cost pressures, many companies continue to ignore their supplier risk management.
- Companies still underestimate general cyber security risks. The dangers that are threatening you are also pervasive among your partners and service providers. This means that when you select partners, it is important not just to carry out a one-off risk assessment. A regular review also needs to take place afterwards and a risk strategy has to be defined (reduce, accept, outsource) in order to really do justice to a "leading practice approach" when assessing your suppliers.
- The fourth point is that not only IT security managers are involved in the issue. Interfaces for the subjects of data protection, legal & compliance, risk management, the purchasing department and the audit department of the company as well as other stakeholders are typical configurations in the environment of a supplier ecosystem. This networking is an added complication to the already complex task for companies.
As these four examples demonstrate, there are now many challenges facing companies. However, this subject's importance is a central issue, based on the experience gained and developments (increasing networking and dependency as well as the increasing maturity of attackers). Supplier risk management should not only include familiar aspects such as the reliability of deliveries, economic assessments, etc.; it should also cover IT security risks. If a hack or data theft is successful, this becomes the responsibility of your company - regardless of whether the attackers were able to access the systems and data directly via your IT or if it was via your supplier's data. This can result in high recovery costs, regulatory penalties and damage to your reputation that cannot be ignored.
Supplier Risk Management –
Why make it so complicated when it can be done easily?
Fortunately, today there are efficient tools that make this complex (but important) task of supplier risk management considerably easier for you. One of the leaders in this field is SecurityScorecard. The SecurityScorecard solution allows you to transparently and clearly understand the security risks of (potential) partners or service providers and then take the measures required. You can continuously monitor changes in your suppliers' scoring and manage the resulting risks. How does this work? SecurityScorecard scans externally available IPs and searches for additional information available online, such as attempted attacks or compromised company e-mail addresses, and clearly summarizes this information.
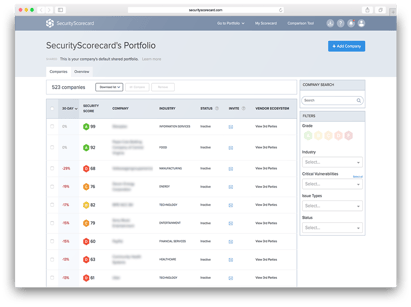 Having said that, SecurityScorecard does not only offer advantages in terms of pure supplier risk management. It also simplifies interface issues such as data protection and legal & compliance requirements. By the way - are the alarm bells still ringing when you hear the word "General Data Protection Regulation"? SecurityScorecard also provides you with helpful information on this subject by comparing the vulnerabilities that have been detected with the technical requirements (e.g. Privacy by Design, Privacy by Default) of the regulation. It is also possible to measure the deficiencies detected against international standards such as ISO 27001/2, NIST CSF or PCI DSS. Of course, you can also put your own company to the test by having it audited by SecurityScorecard. In turn, this can provide you with pointers for improving your own cyber security and your scoring with third parties.
Having said that, SecurityScorecard does not only offer advantages in terms of pure supplier risk management. It also simplifies interface issues such as data protection and legal & compliance requirements. By the way - are the alarm bells still ringing when you hear the word "General Data Protection Regulation"? SecurityScorecard also provides you with helpful information on this subject by comparing the vulnerabilities that have been detected with the technical requirements (e.g. Privacy by Design, Privacy by Default) of the regulation. It is also possible to measure the deficiencies detected against international standards such as ISO 27001/2, NIST CSF or PCI DSS. Of course, you can also put your own company to the test by having it audited by SecurityScorecard. In turn, this can provide you with pointers for improving your own cyber security and your scoring with third parties.
Want to know more about SecurityScorecard? We will be happy to show you personally how you can use SecurityScorecard in your company - request a non-binding quote now!
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first


