Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
Why you should be treating your company data as if it were precious crown jewels

Company data must be backed up, because losing data can have a serious impact on your company and may even threaten its very existence. Data losses can occur for a variety of reasons. These may include hardware or systems failure, ransomware cyber-attacks, viruses or malware and may be caused by natural disasters, human error or malicious behaviour. Do you make sure that your critical company data is adequately backed up? In this blog post, we'll show you best practices for backup and recovery, and explain why you too should be dealing this issue as a matter of urgency.
Data encryption – in a ransomware attack, every minute counts
Imagine that your critical business data is suddenly being held hostage because hackers have encrypted your data, and now they are demanding a high ransom for decrypting it. How should you react? Is your data security guaranteed if you decide not to pay – or even if you do pay? While you are examining your options, your company remains paralysed, and with every minute that passes, there is more and more pressure to make a decision.
You wouldn't wish this scenario on even your worst enemy. Ransomware attacks lend a completely different meaning to back-up and recovery. Back-up and recovery is an essential part of every disaster recovery strategy, but is a major challenge in today's diversified and multi-layered IT environment, so having processes, technologies and procedures for making regular copies of data and applications to a separate, secondary device are just as important as recovering them in the event of data loss/damage, as are business processes.
How are you going about tackling this challenge? With the right ransomware strategy, you can minimise the risk of an attack while at the same time reducing the impact of successful attacks. To achieve this, you should do the following five things:
- Plan: As a basis, devise a plan that should include WHAT, WHEN (Recovery point objectives (RPO), recovery time objectives (RTO) and service level agreements (SLAs)) and WHO.
- Prevent an attack: Focus on awareness, carry out regular patch updates and maintenance. These include hardening (operating system, database, application and web server), authorisation management as IAM (standard users, service, privileged users), MFA, etc.
- Monitor the environment: Attacks should be detected as soon as possible to limit their impact.
- Restore: Rapidly recover systems and data.
- Test: Test the plan and make sure that it is constantly improved.
Back-up and recovery – best practice checklist
This means that it is crucial for every company to implement a back-up and recovery process. Your organisation should be implementing best practices for back-up and recovery to minimise business risk, ensure compliance and reduce costs. Failure to properly manage and secure critical company data can result in disruption to business, and to the loss or potential collapse of the company itself.
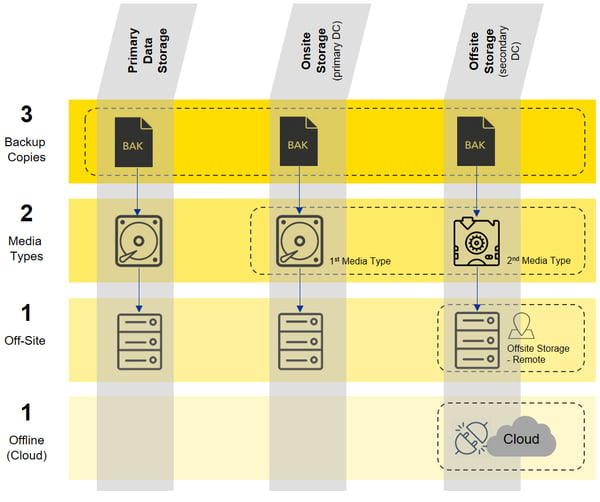
Figure: Data backup 3-2-1-1 backup rule
We have drawn up a best practice checklist for back-up and recovery for you. This guide is designed to help you review the broad outlines of your back-up and recovery plan and your back-up architecture, and to make any necessary modifications:
Information Lifecycle Management (ILM) as a part of the back-up process
Do not forget about Information Lifecycle Management (ILM). ILM is not a specific technology; it is a combination of processes and technologies that governs how data flows through an environment. This means that data can be managed from the moment it is created and stored for the first time, right up until it becomes obsolete and/or needs to be deleted. This also includes records management, because your data, i.e. «records»:
- must be retained based on their value to the organisation and not on its physical or logical characteristics.
- must have been created and maintained for a range of reasons, including to protect rights, meet compliance obligations, document business processes, provide customer service and minimise risk.
- must be managed on a media-neutral basis and stored in accordance with approved policies, procedures and schedules.
- must be stored for the same period of time, irrespective of the media on which specific recordings are stored.
As you can see, a sound data protection strategy is crucial, not just in the event of a ransomware attack and irrespective of the size of your company or the industry. With our whitepaper you can now get valuable tips and learn about proven best practice, because your data is far too precious for it not to be protected by the best practices for back-up and recovery.
Incident Response – because incidents can happen at any time
Despite all the precautions taken, it is still possible that your company may fall victim to a cyber-attack. That's why detection, analysis and response to cyber-attacks is so important – 24/7. Our CSIRT (Computer Security Incident Response Team) from our professional Cyber Defence Center (CDC) helps you to limit the length of time a security incident lasts and the damage it causes, and to dramatically reduce its impact on your business.
Image source: Data backup 3-2-1-1 backup rule from the whitepaper best practices for back-up and recovery
Blog

SWIFT CSCF v2025 Increases the Pressure: Only Cyberresilient is Compliant

Zero Trust Maturity Model 2.0: Security in a Dynamic Future



