Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
Ransomware – a Latent Threat [Part 2]

In the first part of this blog post, Stephan Berger, Senior Cyber Security Analyst at InfoGuard CSIRT, used two cases to show the continuing latent threat of ransomware. In the second part, you will read about four more exciting insights from his work, which he presented at the Swiss Cyber Storm.
As already explained in the last article, observations, experiences and learning from past incidents are enormously important in our InfoGuard Incident Response Team’s work. Takeaways from phishing and MalDocs attacks, vulnerability exploitation (ProxyLogon), attacks via exposed RDP ports and remote desktop solutions have already been analysed in detail. What happens once attackers have gained access to internal networks, and what can we learn from this?
3) Spying on the Network
After the initial compromising and the creation of backdoors, attackers usually start spying on the network. This locates open shares and other computers to which they can connect. Traditionally, network scanners are used for this task (Fig. 7).
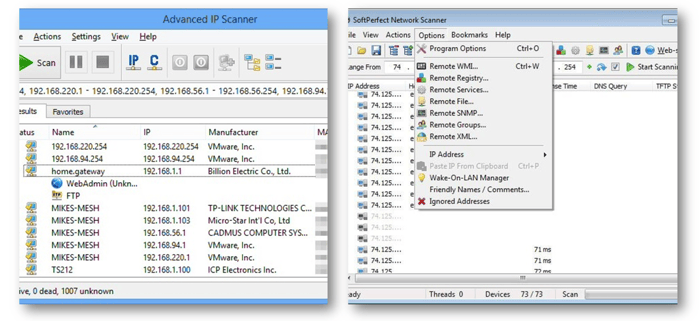
Fig. 7: Network scanner
Interestingly, our InfoGuard team has handled several cases where an observant system administrator has noticed that the CPU load for a critical server is higher than usual. Hence, when checking the running processes, the network scanner, which was started by attackers via a hacked account, stood out.
Key Points & Lessons Learned
- High CPU load: A high CPU load, especially at off-peak times or at weekends on critical servers, should be closely checked. Taking a deeper look into the running processes could potentially show a running network scanner.
- Licence File: The full version of the Softperfect Scanner is sometimes being used by attackers to unlock certain functions. A licence file is necessary for this full version, and may still be stored on the file system. On one hand, this file is interesting for investigation - especially by the police - as the purchase could provide information about who the perpetrator is. On the other hand, the file can be used for tracking attackers across different cases, as long as the same licence file is used in different companies.
- Advanced IP Scanner: An advanced IP scanner saves the last IP ranges scanned under a defined registry key (HKEY_CURRENT_USER\Software\Famatech\advanced_ip_scanner\State). Firstly, analysts can use this information to find out which user has been hacked by the attackers (by simply checking whether the key exists in the user hive or not). Secondly, by assessing the scanned IP ranges, it may be possible to identify which shares or computers the attackers were able to access.
4) Data Theft from the Network
Before the network is encrypted, it is not uncommon for attackers to steal data in order to doubly blackmail the company. To begin with, the network is encrypted and the attackers are the only ones with the key to decrypt it. Then, the attackers are in possession of the company's potentially sensitive data, and often threaten to publish it on the internet.
 Fig. 8: Two well-known upload platforms (MEGA & Yandex)
Fig. 8: Two well-known upload platforms (MEGA & Yandex)
We have seen data exfiltration to one of the two platforms MEGA and YANDEX in many of the cases we have investigated. To do this, the attackers made use of manufacturers' genuine software packages that enable data to be easily uploaded onto the corresponding platform. Of course, to upload, you need an account in the form of a username and password. In several cases, our incident response team was able to recover valid credentials from the system where data had been uploaded to platforms like these. As can be seen in Figure 9, we were able to log into the attackers' account and therefore understand in detail what data was stolen.
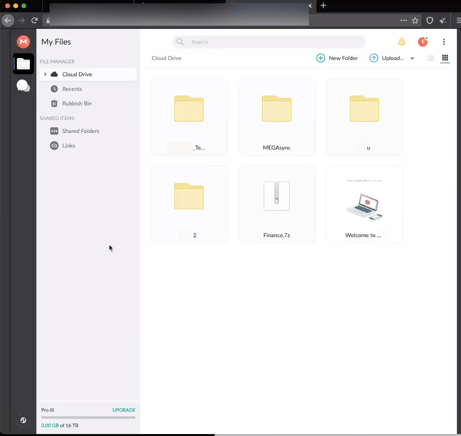 Fig. 9: Attacker Account with Stolen Data
Fig. 9: Attacker Account with Stolen Data
For one thing, this knowledge is very valuable in negotiations with the attackers. For example, the stolen data might not have been that sensitive, which means that publishing it would not be "extremely" critical for the company. On the other hand, working together with the police, this account can be blocked to take away the attackers' control over the data.
Key Points & Lessons Learned
- Blocking or Monitoring Connections to Known Cloud Providers: If (critical) servers connect to a known upload platform like MEGA or Yandex, this could be a sign of data leakage and needs further investigation.
- Access Data to Upload Providers: In the event of a ransomware incident, incident responders or forensic experts should always try to reconstruct the access data for the upload platform that was used or back it up on the file system.
5) Antivirus Logs
In the majority of our investigations, we found that the anti-virus agent deployed in the compromised network had detected and/or prevented one or more steps taken by the attackers. However, the anti-virus logs were either not analysed at all or it was done too late. Anti-virus solution findings can be used effectively as an early warning system and may be able to detect a compromise at an earlier stage.
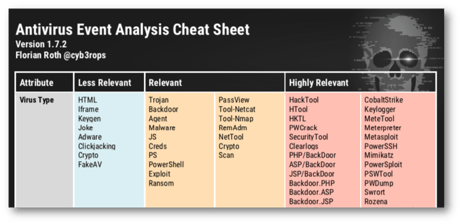 Fig. 10: Antivirus analysis Cheat Sheet (Source: Nextron Systems)
Fig. 10: Antivirus analysis Cheat Sheet (Source: Nextron Systems)
Key Points & Lessons Learned
- Lack of time: In countless conversations with affected companies, what emerges is that in general, system administrators simply do not have the time to check every anti-virus message. In this case, we recommend at least setting up alerts or keyword searches for the most critical detections as per the cheat sheet (Fig. 10), available for download here:
- Every minute counts: In the event of a critical detection based on the cheat sheet, a team of experts should be called in as quickly as possible to assess the alert, because time is a critical factor once the network has been successfully compromised.
6) Active Directory Hardening
During an incident - or preferably before - it is advisable to carry out an in-depth analysis of the Active Directory environment. For example, InfoGuard can provide an in-depth examination of environments like these. One freely available software for an analysis of the critical points is “Ping Castle”.
Saved passwords in group policies are one of the critical issues that our incident response team regularly comes across (Fig. 11).
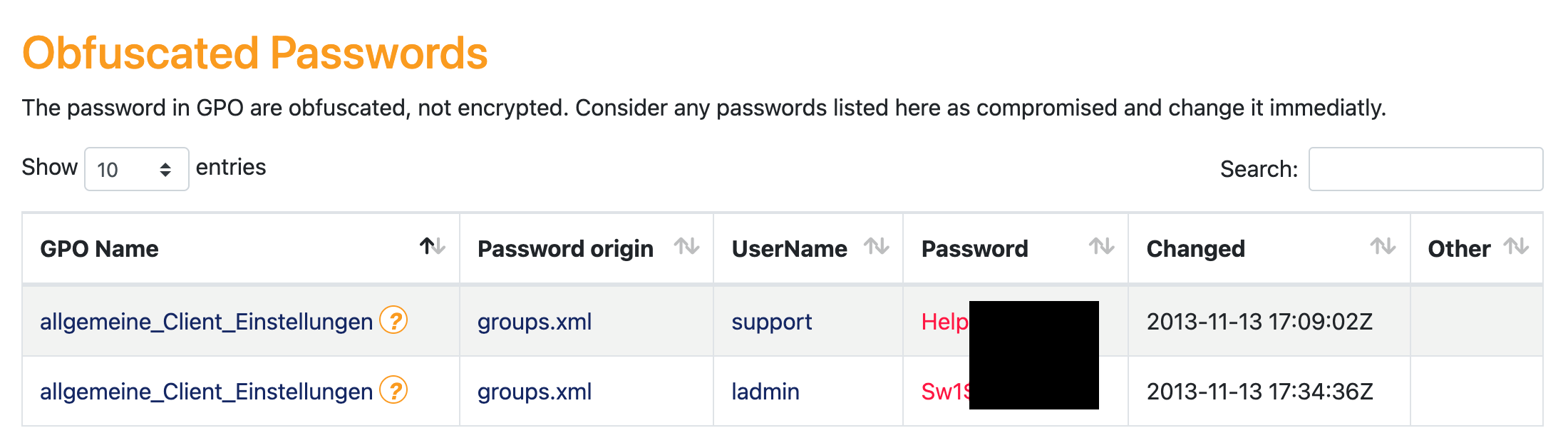
Fig. 11: Saved passwords in group policies
In this case, the user "support" pictured here was one of several administrators in the corresponding domain. In a short time, an attacker could gain the highest privileges in the network from an unprivileged user. Such simple "privilege escalations" must be avoided at all costs in order for the bar to be set as high as possible for an attacker.
Key Points & Lessons Learned
- Saved Passwords: If it is only possible to check a single point in the Active Directory, it is whether there are saved passwords in GPOs – a finding that we encounter surprisingly often during investigations.
- In-Depth Assessment: In addition, we recommend carrying out in-depth Active Directory analyses in order to identify and correct more complex incorrect configurations.
As you can see, the threat of ransomware is anything but a thing of the past. Attackers are organising themselves in a professional way and are constantly refining their attack techniques. It is a major challenge for companies to keep up with this dynamic, and these days it is almost impossible for them to manage it alone. That’s exactly why we developed our Incident Response (IR) Retainer.
You can count on the rapid expert support of our experienced CSIRT in the event of a security incident. This includes not only tracking down the attackers and isolating them as quickly as possible, but also analysing the damage from our Cyber Defence Center, helping to restore normal operations and taking care of the obligation to report a security incident under GDPR requirements.
Interested? All the information and the contact form can be found here:
Blog

15th InfoGuard Security Lounge: Cyber security and AI at the cutting edge

CISO/DPO Dual Role: Efficiency Booster or Conflict in Security & IMS?



