Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
Psychology – the underrated force in cyber security

Phishing is an issue that is a constant source of concern, and not just for companies. Do you remember one of our blog posts in which our penetration testers reported back on the 36C3 congress? One of the featured talks provided a lot of material for discussion among the specialists, which is why we would like to share this content with you. The fact that humans are still the most commonly exploited vulnerability, why psychology is not given enough weight in cyber security, and fascinating insights into the human factors in IT security are all presented here!
In the 36C3-talk “brain hacking”, the subject of security awareness and social engineering was examined from a different point of view. The speaker, Linus Neumann, complained about the lack of practical relevance in current IT security research. Often the topics are highly complex, ones like quantum cryptography, for example, and so what happens in companies daily is completely overlooked. In his opinion, to address the familiar issue of “people being the greatest security factor”, it is imperative to research psychological factors more thoroughly. In one of our previous articles; you can read how even the most sophisticated technical security measures are useless if the weakest link in the security chain has been forgotten about.
The head beats technology
According to Linus Neumann, the human element of IT security have not been researched very much – not enough, and he is absolutely right, but why are phishing attacks still so successful, even though employees are trained in them, and how do you manage to fix in people's minds the right reaction that is needed?
The possible answers are provided by organisational and behavioural psychology courtesy of Daniel Kahnemann, a leading American psychologist. In his view, human behaviour is controlled by two different systems:
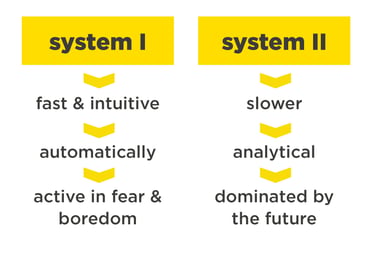 In his presentation, Linus Neumann referred to a statistic that states that up to 50 per cent of all simulated phishing campaigns are successful, but unfortunately, our experience gained from phishing audits shows that this figure tends to be somewhat higher. The success of the campaigns (and, conversely, cyber attacks) can be easily explained by the two systems: for example, as soon as the employee opens the link in the phishing e-mail – or the e-mail attachment - an unexpected event occurs – either the screen goes black or a warning message pops up. The person is alarmed, so “system I” is activated. Then what happens?
In his presentation, Linus Neumann referred to a statistic that states that up to 50 per cent of all simulated phishing campaigns are successful, but unfortunately, our experience gained from phishing audits shows that this figure tends to be somewhat higher. The success of the campaigns (and, conversely, cyber attacks) can be easily explained by the two systems: for example, as soon as the employee opens the link in the phishing e-mail – or the e-mail attachment - an unexpected event occurs – either the screen goes black or a warning message pops up. The person is alarmed, so “system I” is activated. Then what happens?
If it were just a phishing campaign, it would be no more than a scare. In most cases, the “victim” is then notified that it was only an internal security awareness campaign. Phew, once again you were in luck!
Could phishing be the most effective method against cyber attacks?
A simulated phishing attack of this kind consequently addresses system I – fast, intuitively, automatically and actively in case of fear and boredom. Interactivity maximises the learning impact in a significant and above all a long-lasting way. This is why simulated phishing attacks are a measure that we frequently use to check on our employees' security awareness. They experience and become aware in an (apparently) real scenario just how quickly a bad, ill-considered click can happen. Nonetheless, both we and Linus Neumann recommend that they undergo security awareness training beforehand. After all, you don't want to throw your employees in at the deep end, nor do you want to lay on training for those people who didn't fall for the attack. As the saying goes – little strokes fell big oaks!
System II – cyber security begins in the mind
What about “system II”? With suspicious e-mails, the aim is to make sure that system II predominates. By using the appropriate security awareness measures, employees can be given specific training so that instead of system I, system II is triggered as soon as a “tricky” situation arises. Examples of potential actions are explanatory videos, live hacking events or specific e-learning modules, but as is often true, a single one-off action is rarely enough, so it is important to have a variety of recurring (for example, annual) phishing campaigns. Nevertheless, it is also important to take technical measures that prevent employees from being put into situations like this in the first place. Good web, mail and firewall management are paramount here.
Our phishing poster provides first aid!
Apart from simulated phishing attacks, of course, there are other ways of raising employee awareness that should definitely be used at the same time. These include awareness communication in the form of posters, brochures, newsletters, etc. What would that look like? We can show you!
Download our free phishing poster now and receive concise practical tips from our cyber security experts on ways of detecting phishing emails – an immediate, effective way of raising awareness among your employees.
Security awareness with InfoGuard
So you see, cyber security is not just about the technical aspects. The human factor is at least as important, but it is still too often neglected. Therefore, you should rely on effective measures as part of a security awareness campaign! Find out more about the actions to be taken and how our cyber security experts can assist you here:
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant



