Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
(New) Volume Business: Fully Automated Scan and Reasonable Ransom Amount

Atlassian recently announced the discovery of a new vulnerability (CVE-2023-22518) in its Confluence Enterprise Server. This vulnerability allows attackers to reset Confluence and set up an administrator account. The issue affects on-premises installations of Confluence Data Center along with servers that are accessible via the Internet. Attackers have been now able to exploit this gap to carry out attacks or implant ransomware.
On 5 November, the InfoGuard CSIRT (Computer Security Incident Response Team) responded to several incidents involving the encryption of a Confluence server. This was an opportunistic attack that targeted the recently discovered CVE-2023-22518 vulnerability to install the Cerber ransomware on affected Confluence servers. The attacker used an IP address to gain administrator rights to the Confluence application, install a plugin (webshell) and ultimately activate the ransomware. The aim was to make a profit as quickly as possible through the exploitation of a vulnerability that can be automated.
From a hacker’s point of view, then, this represents a (new) volume business with a fully automated scan and a reasonable ransom of less than $2000 in cryptocurrency. The example illustrated below, taken from an investigated incident, shows how the vulnerability was exploited and the encryption completed within seconds.
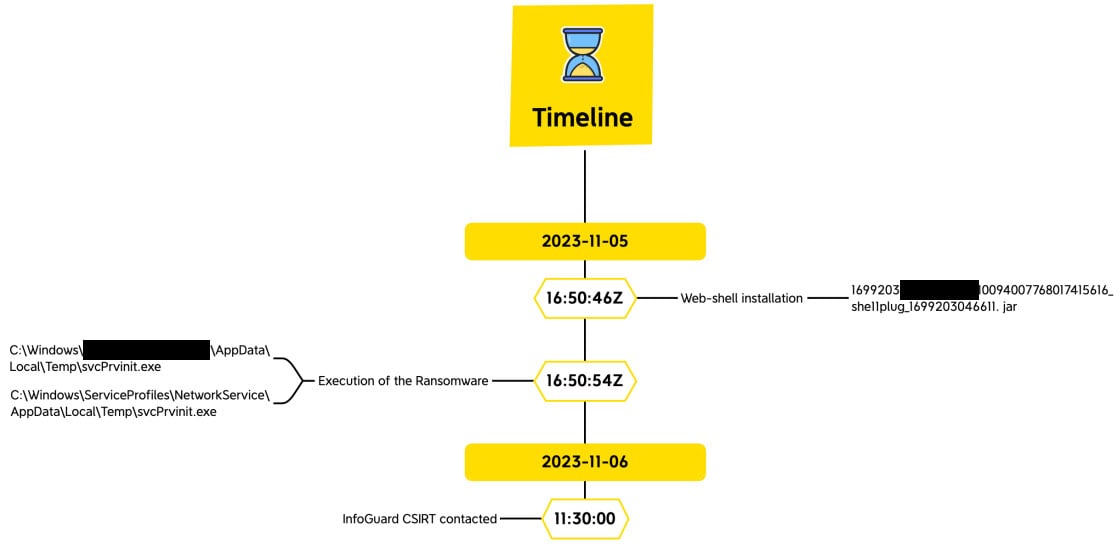
Source: InfoGuard
In many of the incidents we see, the webshells that were also used in this case are sold on the darknet, so it’s worth searching the darknet for compromised company assets.
Darknet scan by the InfoGuard Threat Intelligence Team
The latest analyses by our CSIRT are concerning – and should be a clear and present warning and urgent recommendation to companies. To ensure that your company is spared this fate, we recommend that you take advantage of our Darknet Scan to search for any stolen credentials being offered for sale on darknet marketplaces associated with stealers. Interested? You can find more information here:
Don’t give hackers a point of attack
The InfoGuard CSIRT has witnessed several security incidents in the last few days that can be traced back to the vulnerability in the Confluence Enterprise Server. Similar indicators of compromise (IOCs) and source IP addresses were found to have carried out all of these attacks.
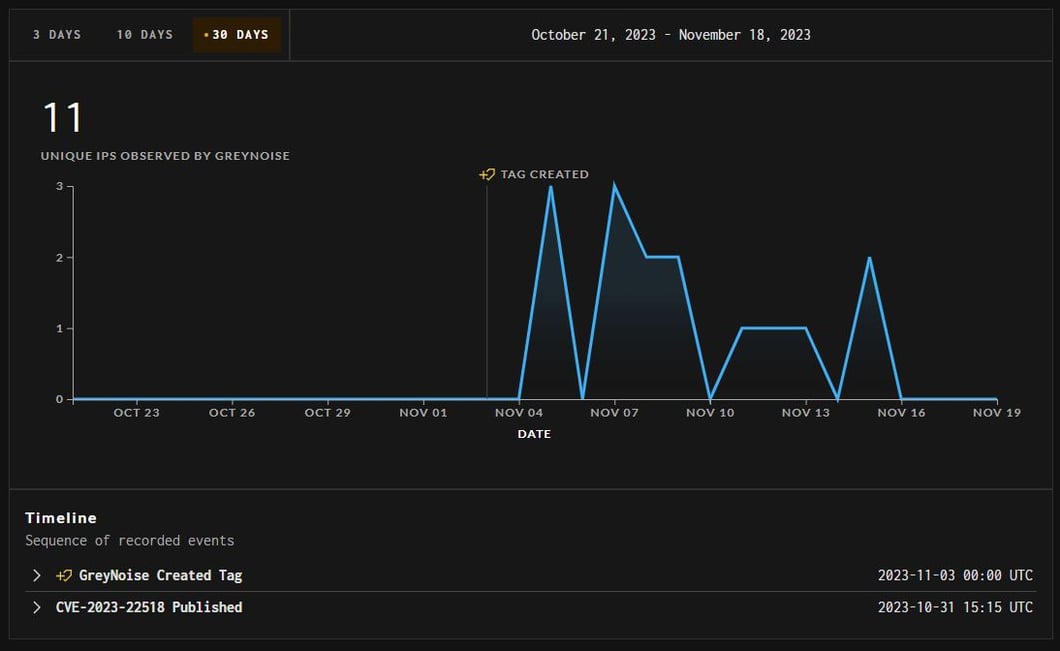
Source: greynoise
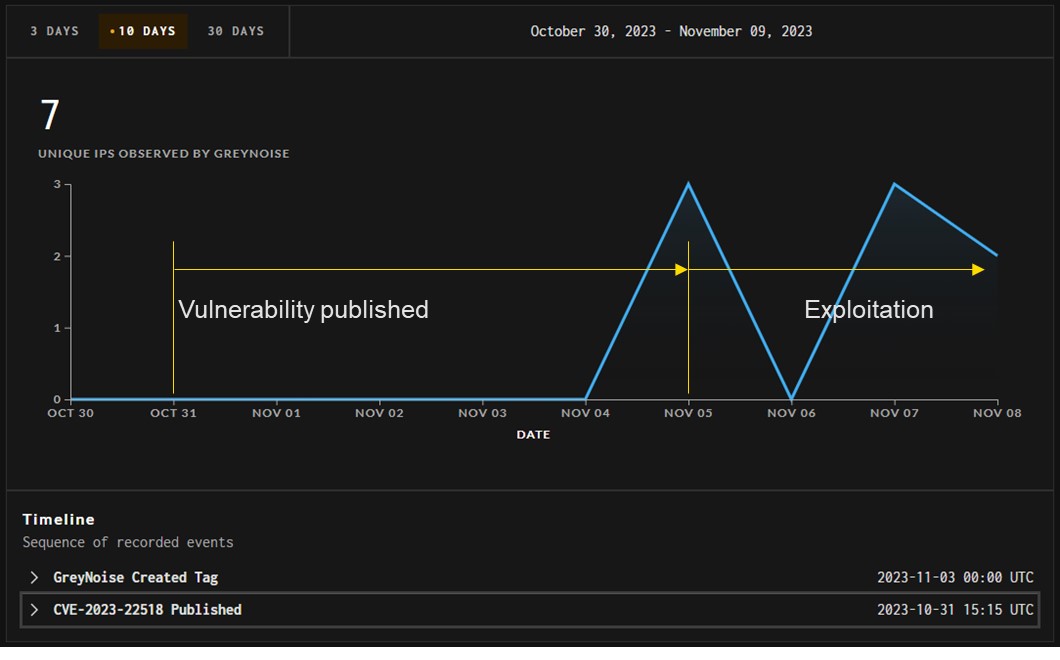
Source: greynoise
The figure shows how the attacker group underwent five days of preparation to exploit the vulnerability as a volume transaction and monetise it immediately.
Attackers are currently on the hunt for accessible systems that have not yet been patched and will attack them. Atlassian has issued warnings against these attacks and urges users to take the countermeasures recommended in the advisory memorandum – including installing the patches provided. If this is not possible, users should disconnect the affected system from the Internet, or at least block certain endpoints.
This once again emphasises the importance of external vulnerability management. New vulnerabilities are being discovered almost daily and cyber criminals are even having success in exploiting existing vulnerabilities. Every company’s core policies should include the ongoing review of vulnerabilities and the optimisation of its own infrastructure.
InfoGuard supports you around the clock
We offer you comprehensive support for vulnerability management, from the initial concept through to a standardised managed service from our certified Cyber Defence Center (CDC) in Baar.
External Vulnerability Management Service (eVUMA) – 24/7
Our 24/7 eVUMA enables you to see your company from the perspective of attackers. Our security experts scan your perimeter infrastructure on a daily basis and take charge of all steps of the vulnerability management process. This allows you to react quickly to threats without having to monitor your external infrastructure around the clock. Find out more about our (External) Vulnerability Management Service.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


