InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Innovations, trends and challenges in cyber security – that was the 11th InfoGuard Innovation Day

This year too, the InfoGuard Innovation Day, which took place on 25 January 2023 with over 700 participants from Switzerland, Germany and Austria, was a complete success. The virtual trade fair began with one of the two exciting keynote speakers. Dr Hannes P. Lubich gave an illuminating overview of the technological trends and new defence strategies coming by 2030. This was followed throughout the day by 24 presentations given by experts from InfoGuard and its 16 network and security partners. Philipp Rhomberg, the CDO of the Emil Frey Group, kept the participants gripped during the second keynote speech with a field report on the cyber-attack on Emil Frey. Overall, this year’s Innovation Day was a great educational event for all fans of cyber security. Did you miss out on the event? In this article you will find out about the most important insights and learnings from the keynote speeches and InfoGuard presentations.
The hacker attack on the Emil Frey Group – the most significant learnings
Cyber-attacks on Swiss companies are on the increase. Hackers are gaining undetected access to company networks, and with it an overview of the data they can encrypt. On D-day, this means the network is literally “paralysed” with nothing working at all. This is what happened at Emil Frey. Philipp Rhomberg, CDO of the Emil Frey Group and a board director, described in his gripping keynote speech how the hacker attack unfolded, and how the company handled this crisis with help from InfoGuard’s CSIRT. Rhomberg shared his most important learnings with the participants:
- Good preparation is absolutely indispensable: backups are essential, as is infrastructure testing, security awareness, the composition of the task force, etc.
- Structural and procedural organisation must be in place.
- The need for emergency communication cannot be overstated, and it demands careful preparation.
Dr. Hannes P. Lubich provides an overview on the trends, the changes to the threat landscape and the new defence dispositive in 2030
What will 2030 bring for the cyber world? In his keynote speech, Dr Hannes P. Lubich risked making a forecast. The renowned expert and InfoGuard board member is assuming that the economy will continue to be unstable, so corporate strategies should be ready for it. Climate change will also continue to be a major issue. Technology, which in future will become even more crucial for humanity than it has been up to now, will also undergo a dramatic evolution. Technology is increasingly exerting its power to shape our lifestyles, although this is not clearly recognisable, and it is taking (partial) control over our lives. One good example of this according to Lubich is kitchen appliances that can communicate over the net. Finally, Lubich gave the following tips: systems need to be tested where it’s hurting, not where it’s working. Also, there should always be a plan B in place that can be rolled out immediately.
InfoGuard Breach & Attack Simulation – the new service
EinIt’s no longer enough to do an annual vulnerability scan or a one-off attack simulation. In order to cope successfully with a constantly changing threat landscape, you have to be continually reviewing your security measures and optimising your infrastructure. This is what the recent discipline of ”Breach & Attack Simulation“ (BAS for short) offers – and it’s so much more than just automated pen-testing. In his presentation, Martin Dudle, Head of Security Detection Solutions, explained BAS’ added value, for instance, a significant improvement of the IT risk management process.
Does this sound interesting? You can find more information about the Breach & Attack Simulation Service and the non-binding contact form here.
User Enumeration – Tell me what you use, and our Red Team will tell you, who you are!
Mario Bischof, the Senior Penetration Tester at InfoGuard, explained exactly what user enumeration is and what can be done to counter it. In a nutshell, user enumeration is nothing more or less than data theft using registration forms. On a lot of public websites such as streaming platforms like Netflix, for example, critical information is given if the user access data is entered wrongly or if the user is asked to enter a new password, for example, if the email address already exists. This could be exploited for an attack by cyber criminals.
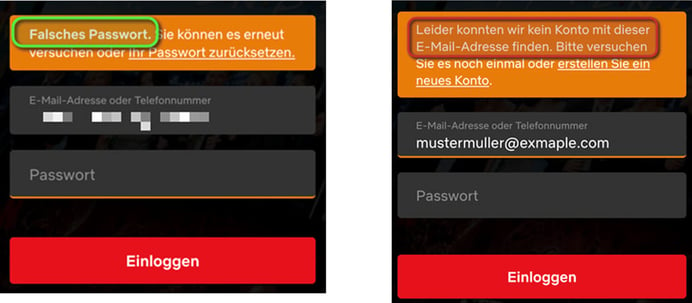
Image source: Mario Bischof
In his presentation, Bischof showed the many ways in which user enumeration can be achieved, the extent to which artificial intelligence can help an attacker circumvent security measures such as CAPTCHAS, and how data acquisition and machine learning could be used to create a targeted profiling of the people behind the email addresses.
ISO 27001:2022 – what has changed and what to look out for when implementing it
The ISO 27001:2013 standard was replaced in October 2022 by ISO 27001:2022. This standard contains specifications for information security management systems (ISMS) and at the same time sets out the requirements for implementing and maintaining the ISMS. This is key to protecting the most important assets.
The changes between the old and the new standard are minor. 14 areas from the 2013 version have been incorporated into four new control types. The controls have been reduced from 114 to 93. There are also new controls that deal with topics such as cloud security or threat intelligence. For more information on ISO 27001:2022, read this blog article.

Cyber Defence – why it is so important to rapidly analyse malware
When an incident occurs, time is of the essence. In her presentation, Ramona Betschart, a Cyber Security Analyst at InfoGuard, showed how quickly she and her team are analysing malware every day, and why this is so important. This is because as soon as it is clear through which IPs and domains the malware has entered the system, it can be immediately blocked to halt any further damage.
Successful defence against cyber-attacks begins by proactively eliminating known vulnerabilities in the infrastructure and continuously recording and analysing log information from all the system components. That’s why the InfoGuard Cyber Defence Centre offers what are called basic detection services. Whenever traditional security systems reach their limits, additional advanced detection services are recommended.
Cyber Threat Intelligence Annual Review – Trends, attack patterns and impacts
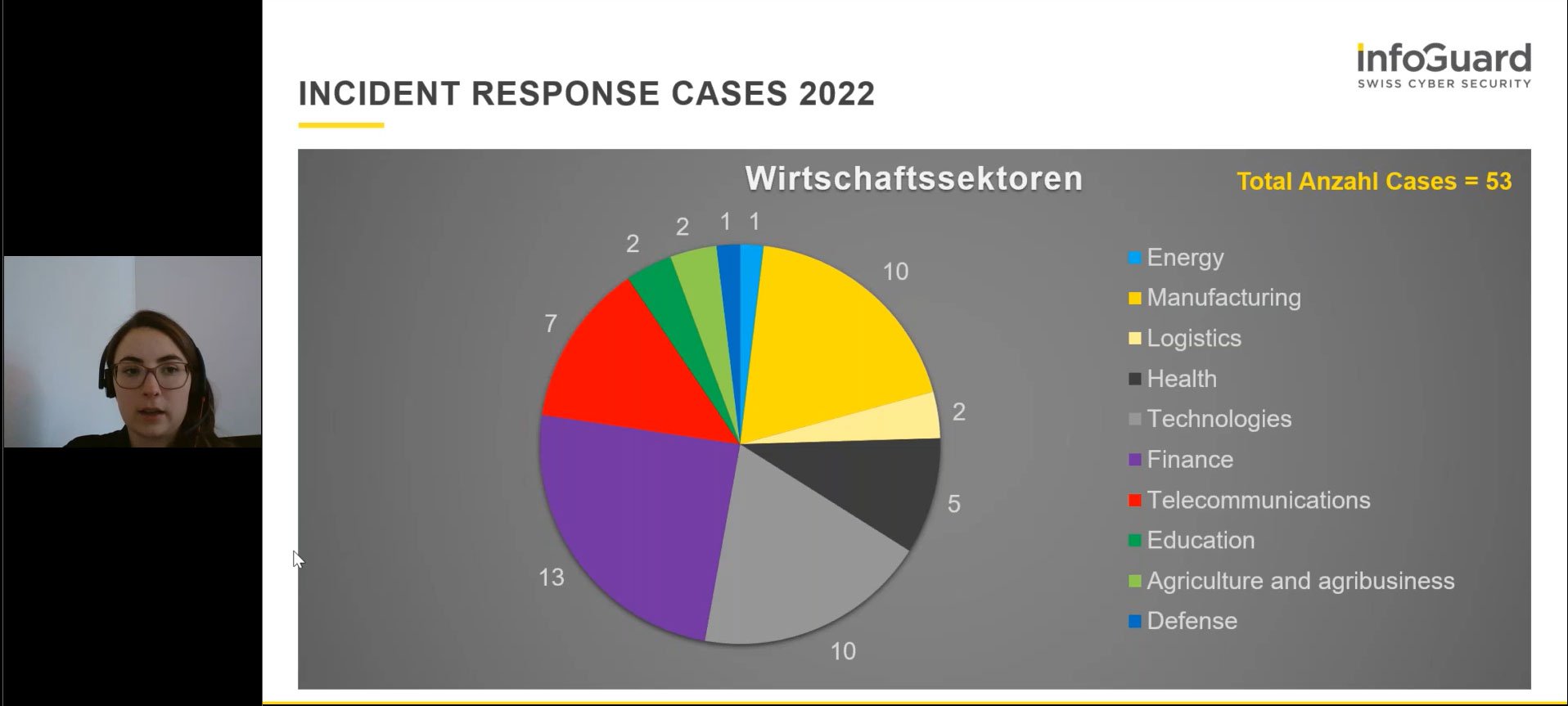
All in all, 2022 was another turbulent year – in particular for our InfoGuard Computer Security Incident Response Team (CSIRT). Jorina Baron, Threat Intelligence Analyst in the CSIRT, gave participants a glimpse into the past year. In total, CSIRT worked on 53 major incident response cases. The sectors most frequently affected were telecoms, technology and manufacturing. In 15 of the 53 cases, the initial attack was via VPN. In 11 of the cases, the attackers exploited vulnerabilities. Jorina Baron recommended using multi-factor authentication to proactively protect systems. Similarly, services should not be exposed and vulnerabilities should always be patched straight away.
By the way, we are already planning a separate blog post by our CSIRT with their insights. To avoid missing out on this, you should also sign up to receive our blog updates!
Incident-Response-Plan – how to prepare proactively for a security incident
It’s well known that preparation is everything. The extent of the damage caused by a successful cyber-attack also crucially hinges on how well prepared the company is to deal with a crisis of this kind. Our Principal Cyber Security Consultant Michael Güttinger has put together the greatest challenges he regularly encounters with clients when dealing with cyber-attacks.
- There has been no preparation for emergency operation.
- IT and senior management are inadequately prepared for a cyber-attack.
- The available plans have not been successfully tested.
- IT has no proxy and is unable to completely concentrate on dealing with a cyber-attack.
Güttinger repeatedly emphasised the importance of solid preparation. In so-called incident response plan workshops, he and his colleagues from Consulting regularly support clients in developing the necessary process steps for emergency operations, crisis management, IT management and recovery, and the continuous improvement process. Interested? You can find more information here.
SCiON-Internet – secure and flexible as a Managed Security Service
Stefan Pfiffner, Head of Security Prevention Solutions at InfoGuard, also opened with the question: Why do we need a new Internet at all? His answer – the internet was never fundamentally designed to be a secure network. That’s why it is vulnerable to “BGP hijacking” or “BGP leaking”. The Secure Swiss Finance Network (SSFN) is the new strategic communication network for the Swiss Finance Centre, replacing the well-known Finance IPNet. SSFN is based on the Next-Generation SCiON architecture developed by ETH and marketed by the Swiss company Anapaya. SCiON combines the security and reliability of private networks with the flexibility of the internet. In order to make access by the financial institution to the SSFN as simple and secure as possible, we developed the InfoGuard Managed Service Single Edge and Redundant Edge 100 Mbps. A full managed service is also available with end to end service, hardware, Anapaya VM and software, configuration and monitoring of SCiON Edge.
Spotlight on data protection – the new data protection law and its impact
From September 2023, the new Swiss Data Protection Law will come into force. Senior Cyber Security Consultant Daniel Däppen explained the changes the law will effectively bring:
- The rights of affected parties will be strengthened. It is important for companies to prepare for this. Däppen recommends that they define processes for the right to information, access rights, deletion, etc.
- If a data protection incident occurs, it is important to report it to the FDPIC as soon as possible. The minimum information you have to provide is: the contact details of the company’s contact person, the type of breach, the number of data subjects involved, the consequences and risks for the data subjects and the measures that have already been taken.
- In order to transition to the new data protection law, it is advisable to define responsibilities and processes within the company well in advance. Current plans have not been sufficiently tested.
InfoGuard Innovation Day – A well-established platform that will stay that way in the future
The 11th InfoGuard Innovation Day was a resounding success. Both we and the participants have learned lots of new stuff, got some informative tips and got to know about upcoming innovations in the future. This was also reflected in the huge amount of positive feedback from the participants.
Blog

Cyber Security vor neuen Risikolagen: Der 14. InfoGuard Innovation Day ordnet ein
Zero Trust ab 2026: 3 Praxisansätze für Cyberabwehr zwischen KI und Compliance



