InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
[InfoGuard CSIRT Warning] Currently Ransomware Attacks are underway with the Parcel Trick

Right now, InfoGuard CSIRT is investigating multiple ransomware attacks on Swiss companies. In many cases we found the same initial source of infection – a phishing e-mail with the well-known parcel trick. That’s why our CSIRT is informing you about our latest discoveries in this blog post
InfoGuard CSIRT has been investigating several cases of fraud in recent weeks. These are all based on an initial phishing e-mail notifying the delivery of a parcel or letter with a telephone call – below is an image of a real phishing e-mail:
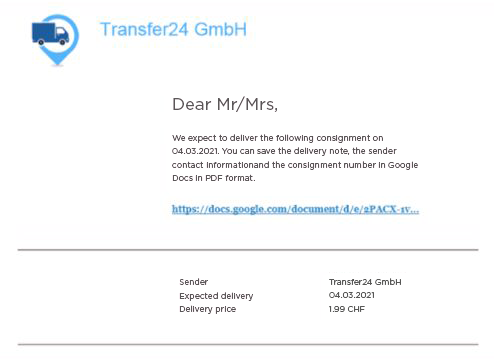
As early as December 2020, the Zurich Cantonal Police informed cybercrimepolice.ch about an e-banking Trojan, which is notified beforehand by telephone. A computer voice with an Eastern European accent calls and usually asks the caller to open an e-mail and install software. Then a button has to be pressed to ensure that the parcel or letter is delivered. However, an e-banking Trojan is downloaded in the background, and it can be used to spy on the company's financial transactions:
What we’ve learned from the current spate of Ransomware attacks
One thing that we are noticing more and more in attacks on companies is that the attackers also speak perfect German. As well as that, they no longer just install the Trojan, they also steal data on a massive scale, then encrypt the targeted company's data and systems and demand a ransom (ransomware).
In the cases investigated by our CSIRT, the time lag between the initial e-mail and the final data encryption was 2-3 weeks.
What our CSIRT recommends
Consequently, we strongly recommend that you urgently warn your employees about phishing e-mails like these. You are also welcome to use our free phishing poster with the most important features and tips for recognising attempts like these to scam you!
Specifically, ask your employees if the screenshot looks familiar to them or if they have received strange phone calls about parcel deliveries.
We also recommend that you examine your systems based on the following indicators:
- Has a local user been created (in the form of c:\Users\Xrq….)?
- Has software been installed (JDK, Ngrok, RDPWrapper)?
- Does the initial dropper frequently appear in the form c:\Users\<username>\Downloads\sendung_Nxxxxx_ddmmyyyy.com (see the screenshot above)
- Check your firewall for proxy logs to the following accesses:
- bin.equinox.io (Download ngrok)
- Accesses to websites in the following format: <domain>.com/.<word>/api.php
- Potential access to docs.google.com (may generate a lot of false positives)
If you detect one or more indicators, we recommend that you:
- Isolate the affected systems and disconnect them from the internet (if possible, disconnect the entire company from the network).
- Call in a forensic specialist with the expertise to investigate the situation on your premises.
InfoGuard is here to help you – 24/7
InfoGuard CSIRT will assist you by searching within your infrastructure for traces of a cyber attack. Our Compromise Assessment uncovers breaches in your whole environment, not just those related to the ransomware attacks described above.
In the event of this kind of cyber attack, it is crucial to act quickly and professionally. Our Incident Response Retainer is the best and most effective solution. In an onboarding workshop together with you, we will prepare you for an emergency situation. If one occurs, we can react correctly and collaborate with you – quickly, competently and with a lot of experience behind us – 24/7. Learn more about our Incident Response Retainer here:
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first

