InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Deutschland GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Identities are central to digitalisation and security

Digital transformation is the phrase on everyone's lips. It helps companies improve customer experience, simplify business start-ups and prepare for future challenges and business needs. However, this modernisation also presents new challenges in terms of cyber security and data protection. This is because the use of local and multi-cloud/remote environments enables users to access data from anywhere. This in turn means that identity governance is shifting, with the use of identity federation and personal devices (BYOD). At the same time, the number of data access points, roles and user accounts - including privileged accounts - is increasing. In such a complex IT ecosystem, it is hard to effectively manage and regulate identities and the access to them. In a multi-part blog series, we would like to show you how you can overcome these challenges with an identity-centred approach to security.
Attacks on identities are a reality
As we all know, top management is directly responsible for corporate risks and, consequently, for managing them. This also includes risks related to Identity Governance & Administration (IGA), as they have both a strong operational and financial impact. Identifying and managing identity-related risk is fundamental, because the consequences of an identity-related security breach range from damage to your reputation to financial losses in the form of fines or ransomware payments. The figures in the following stats speak for themselves:
Swiss statistics:
An average of 83 digital offences a day (2021).
Most commonly, goods that had already been paid for on classified ad platforms were not delivered (6,884 offences); The second most common way to commit fraud was to use online payment systems or another person's identity or all personal identification data. (6,670 offences).
Source: BFS Police crime statistics (PKS)> 1 million victims of identity theft in the first half of 2021. This represents an increase of 56% over the same period last year.
Source: Swiss Public Auditor CRIF Cyber Observatory
International statistics:
81% of hacking-related breaches use weak, stolen or otherwise compromised credentials.
Source: Verizon Data Breach Investigation Report, 30.03.202290 % of cyber attacks on cloud environments involve compromised privileged access information
Source: Centrify, 30.03.2022
To create effective risk-based access and identity management programmes, there is a need to focus on the risks associated with each identity:
-
Who can access important company applications (legacy and cloud)?
-
What risk does this access represent for the company?
-
Why does access exist and is it appropriate?
-
Is there a testing plan for the application and review process?
-
From a business risk standpoint, how is access used?
These risks have been made even worse by the global Covid-19 pandemic, but access data theft is also rising. On one hand, we recommend concentrating on distributed, remote workplaces and staff. On the other hand, we also recommend that there be efficient monitoring of digital threats as well as compliance with and assessment of legal and industry-specific requirements for data protection and security. It is also advisable to check access to sensitive customer and financial data, along with transactional processes.
Identities are the focus
Current requirements are forcing companies to put identity and its context centre stage. For example, an identity can be both an employee and a customer, a doctor can be a patient, or a member of staff can also be a citizen. In combination with agile business models such as job-sharing and job-rotation etc. access management has developed from a traditional perimeter-based approach to becoming identity-centred.
What we repeatedly find is that companies have difficulties in the following four specific areas:
-
Cloud integration with non-standard, centralised Identity & Access Management (IAM) solutions;
-
Integration of IAM into the DevSecOps processes;
-
Integration of SCADA / OT (Operational Technology) and Internet of Things (IoT) into Identity Governance & Administration (IGA);
-
Fulfilment of audit security and compliance requirements
This can be remedied by comprehensive Identity Governance & Administration (IGA), which targets cloud, hybrid and/or on-premises security, as well as the expectations of users and companies in terms of data protection, data security and cyber security.
IGA solves open points of the IAM
IGA is an important part of managing and controlling identities and related access authorisation. At the same time, IGA helps solve IAM challenges such as improper and/or outdated access to corporate resources, remote workers, time-consuming provisioning processes, poor Bring Your Own Device (BYOD) policies and strict compliance requirements. All these issues increase security risks and undermine companies' compliance posture.
With IGA, companies are able to extensively automate their access management workflows - even beyond their own boundaries - and in doing so, reduce risk. IAM policies can also be defined and implemented. Last but not least, it enables companies to actively monitor user access processes for compliance reporting and to proactively implement automated measures. For this reason, more and more companies are modernising IGA in order to continue to sustainably meet the growing compliance requirements of eHealth, SOX, ISO/IEC 27701, PCI DSS, etc., but compliance is not the only area that benefits from IGA.
IGA improves visibility over what users can and cannot access. This enables IT administrators to optimise identity management and access control, and effectively reduce risk and protect business-critical systems and data. The right IGA tools can help businesses protect themselves in today's complex IT and cyber security landscape, improve their resilience and deliver scalable growth.
Business-to-Identity as a key element
IGA is the secret kingpin of governance, risk and compliance. Identity Governance & Administration (IGA) with all its disciplines such as Privileged Access Management (PAM), Customer Identity & Access Management (CIAM) etc. are key functions for strategic security objectives such as (this is not an exhaustive list):
-
Zero Trust Completeness
-
Need-to-Know
-
(Data Protection &) Security by Design
-
(Data Protection &) Security by Default
A key element in identity-centred management is to make identity central to security strategies, based on a business-to-identity framework with IGA. A framework like this includes best practices for effectively managing the identity threat landscape, overcoming barriers to automation and ensuring security-by-design in the central governance of identities.
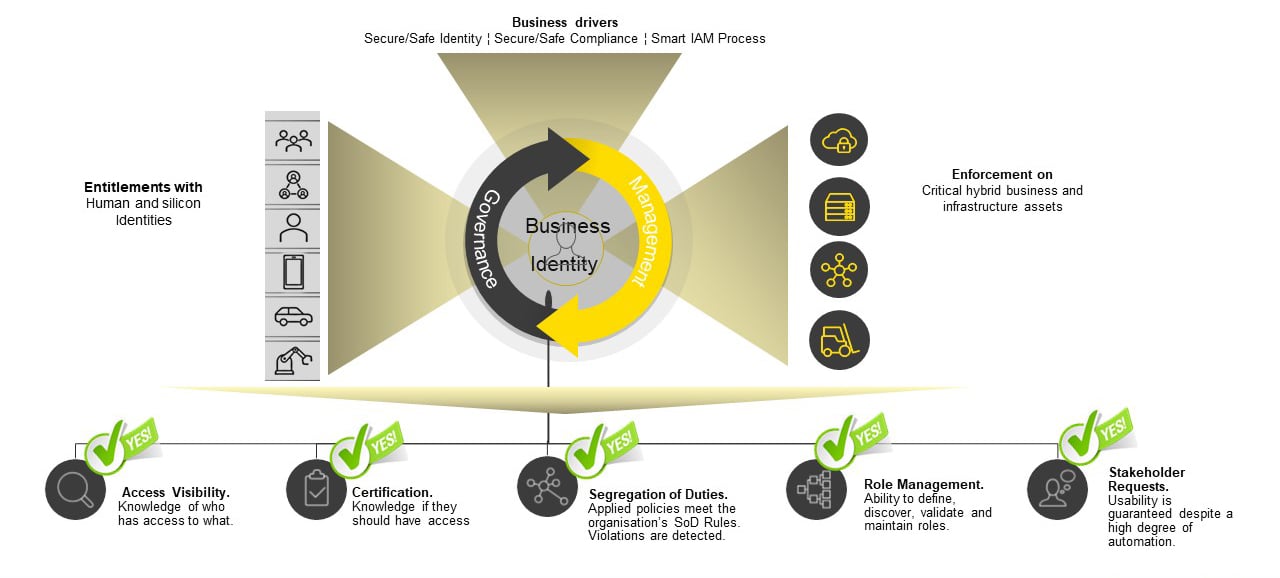 Fig. 1: Business-to-Identity Framework
Fig. 1: Business-to-Identity Framework
IGA tools also help track and control user access, for both on-premises and cloud-based systems. This enables you to ensure that the right users have the right access to the right systems throughout the lifecycle, as well as being able to detect and stop unauthorised access. By implementing the right controls with IGA, organisations can minimise risk and ensure regulatory compliance. Read an upcoming blog article to learn how to make the paradigm shift to identity-centred security using the Business-to-Identity Framework and IGA.
You don't want to miss out on what comes next? Then you should subscribe to our blog updates! You don’t want to (or can‘t) wait? It doesn’t matter. Of course, our experts will be happy to answer your questions at any time. Contact us!
You don’t want to (or can‘t) wait? It doesn’t matter. Of course, our experts will be happy to answer your questions at any time. Contact us!
Blog

Cyber Security vor neuen Risikolagen: Der 14. InfoGuard Innovation Day ordnet ein
Zero Trust ab 2026: 3 Praxisansätze für Cyberabwehr zwischen KI und Compliance

