InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
How to build Cyber Supply Chain Risk Management

In a previous article, we showed why many companies underestimate cyber supply chain risk management (C-SCRM), even though the impact on their own business can be huge. This is not due to a lack of interest ‒ quite the opposite! As is so often the case, it is caused by a lack of internal resources. In this article, we show you how to efficiently set up a C-SCRM and in doing so gain important insights into your risk landscape.
Companies' value chains have never been more vulnerable than they are today. This is due to influences such as changed production methods, globalisation, increasing technology / digitisation, economic and political influences etc. To be able to assess the risk potential, it is important to know the process chains, their dependencies and consequences in the event of disruptions (availability, financial consequences, reputation, compliance with SLAs, etc.). These form the basis for determining loss reduction measures as part of risk management.
Swiss companies are increasingly focusing on Cyber Supply Chain Risk Management (C-SCRM). It is important to be aligned with existing standards and best practices. For example, ISO/IEC 27036:2013 is part of the ISO/IEC 27001 series, and describes information security for supplier relationships. Additionally, in its update of the NIST Cyber Security Framework last year, NIST added the category "Supply Chain Risk Management", underlining the importance of SCRM in terms of corporate security.
NIST CSF explicitly addresses Supply Chain Risk Management
Version 1.1 of the NIST Cyber Security Framework (in Switzerland, this framework forms the basis for the minimum ICT standard) is specifically designed to take account of new technological developments and also covers areas such as supply chain and IoT. Another focus is on identifying risks in the entire supply chain. NIST has introduced a separate category (ID.SC) to implement processes to identify, assess and manage risks in the supply chain.
This process involves not only the company itself but also a wide range of actors such as manufacturers of devices, network and cloud providers, other service providers and consumers. Communication and auditing of cyber security requirements between stakeholders is one aspect of C-SCRM. NIST defines the main objective as follows:
"Identify, assess, and minimise products and services that may contain potentially harmful features, are counterfeit, or are vulnerable due to poor manufacturing and development practices within the cyber supply chain."
In terms of cyber security, this means, among other things:
- Definition of cyber security requirements and measures for suppliers, service providers and information technologies
- Enforcement of the requirements via formal agreements (e.g. contracts)
- Verification and validation of communication and access from and to suppliers and partners
- Checking whether the cyber security requirements have been effectively implemented
- Managing and supervising the above activities
In concrete terms, this means that you must ensure that all your business partners enter into a binding commitment to protect digital intellectual property and data in exactly the same way as is stipulated in your cyber security requirements. In addition, all parties must be aware that you also reserve the right to review this.
Supplier Lifecycle Management in relation to C-SCRM
The aim of a supplier lifecycle process is to optimally integrate and manage third-party providers in your company into your processes and to automate the monitoring and management of providers as far as possible, thereby reducing the workload. This also applies to the area of C-SCRM, which is part of Supplier Lifecycle Management and requires specific knowledge and experience in the cyber security field. The entire supplier lifecycle can be described as follows:
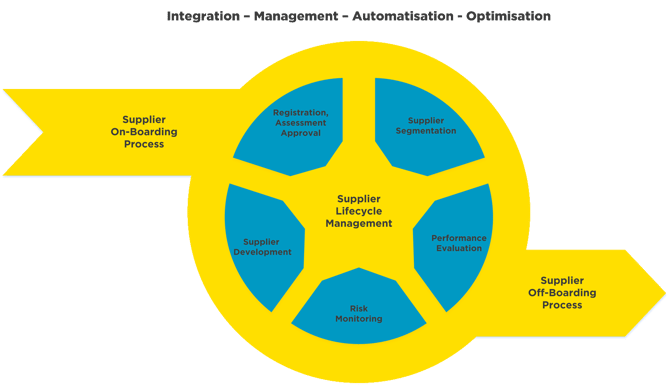
The challenges of C-SCRM that your company needs to focus on can be broken down into the following areas:
- Assessment & suppliers on-boarding process
a) Assessment and planning of security, compliance and data protection
b) Assessment of potential suppliers
c) Gathering of information on second and third stage suppliers
d) Peer comparison with suppliers, review of results and a report with recommendation
e) Documenting the decision and the on-boarding process - Preparation & procurement process
a) Definition of security targets
b) Assistance with the procurement process involving all parties, including cyber risks
c) Definition of the identification and evaluation of cyber risks
d) Definition and documenting of supplier requirements - Registration, audit, authorisation & segmentation process
a) Supplier rating (based on tier, service, etc.) based on questionnaires, interviews and other assessment tools, taking into account cyber risks.
b) Auditing and evaluation of suppliers
c) review of results and a report with recommendations - Security performance & risk monitoring
a) Regular cyber risk assessment of existing suppliers
b) Monitoring of cyber risks and determining the measures to be taken
c) Defining the measures for the minimisation of risks
d) Monitoring of the C-SCRM - Supplier development & reporting
a) Review of the Cyber Supply Chain Risk Managements (C-SCRM)
b) Review of safety requirements for suppliers, e.g. due to changing criticality
c) Internal reporting of SLAs and cyber security metrics
d) Reporting on Cyber Supply Chain Risk Managements (C-SCRM) - Supplier removal / off-boarding process
a) Disabling of logical system and physical accesses
b) Removal of system components that are no longer required
c) Ensuring the destruction of data after termination of cooperation
d) Monitoring and checking implementation
So as you see, Cyber Supply Chain Risk Management is not really a new discipline, but rather an extension of your own risk management and your cyber security in terms of the suppliers. The advantages are obvious: you get the transparency about cyber risks and the maturity of cyber security within your supply chain that you need. This enables you to meet the various compliance requirements, and at the same time view your critical assets in relation to your suppliers. By using an appropriate tool such as "SecurityScorecard", this can also be done with relatively little effort.
Do you know the security risks in your supply chain that are affecting your business?
Cyber Supply Chain Risk Management by InfoGuard
Our many years of experience in cyber security have given us the expertise you need to help you define and build your Cyber Supply chain Risk Management. We help you to understand your current risk landscape and measure your risks, define your supply chain risk management strategy and implement the measures required. Find out more about this on our web page.
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first


