Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
How an enterprise IT security architecture makes digitisation easier

Are you familiar with these issues: difficulties in meeting customer needs in time, a lack of innovative force, late project completion, inadequate functionality of applications, high operating costs – and last but not least, gut decisions due to insufficient information...?
… If this sparks memories for you, you should definitely keep reading.
The high complexity of the IT systems in the company is often (partly) responsible for the factors mentioned above. This is because the system tends to grow almost unnoticed from year to year. At some point, it reaches the threshold where the overall picture is lost and is virtually impossible to control. The creep in system complexity often goes unnoticed. The causes for this are:
- Bought-in applications with their own architecture. These are often not harmonised with the company architecture.
- Applications that are not fully integrated into the existing environment or continue to exist as "islands", with only a minimal set of interfaces to the existing environment.
- Legacy systems, which are have not been replaced or have only been partially replaced.
- Existing components that are not expanded into services, but "copied" into new applications.
- Missing or incomplete documentation, or documentation that has not been updated, not to mention the innumerable security gaps...
(IT) architecture - having or not having a plan
This is a crucial issue. Many companies lack IT security architecture, or at least it can no longer withstand the demands of digitisation. But why is company-wide IT security architecture necessary at all?
- Let me ask you four (not entirely serious) questions about this. (The answers are available at the end of this blog post.)
- Why are properties entered in a land register?
a. Because otherwise, no one can mow the lawn.
b. Because it's proof that you own the property.
c. Because otherwise, you won't be able to find the property. - Why is a structural building plan drawn up?
a. Because otherwise, architects wouldn't have a job.
b. Because the plans look great.
c. Because you can quickly get an image of the building project and implement it correctly. - Why are house bricks rectangular and a standard size?
a. Because it means a house can be built in a standardised, problem-free way.
b. Because rectangular bricks are nicer.
c. Because round bricks are more expensive. - Why are there different areas for use within the home?
a. Because it makes the house look nicer.
b. Because they satisfy different needs.
c. Because that's the only way to justify the blueprint.
These questions address the need for a planned or structured approach. Just imagine what cities and places would look like are like if everyone was allowed to build indiscriminately? It would inevitably lead to conflict and mayhem in construction. The way in which land is developed and used is regulated through development schemes. These then form the basis for the architects, who develop the corresponding building project and finally execute it with a variety of companies.
4 advantages of IT security architecture
Applied to IT security architecture, the questions above become the following:
- Certain artifacts serve as proof, e.g. when a company wishes to obtain (safety) certification. This makes it easier to prove during initial or re-certification that the processes are actually “lived”.
- A construction plan allows the components to be organised and provides the basis for informing internal and external departments of the current situation in a prompt manner. This enables projects to be rolled out more quickly and new employees to be trained more easily.
- Standardised components make it possible to develop modular IT, on-site or in the cloud. This ensures that IT is used in a consistent manner, promotes clear responsibilities and reduces costs because fewer components need to be maintained and they are used simultaneously by numerous applications (economies of scale).
- Defined areas of use and services make it easier to reuse and change functions and to protect them in suitably designed security zones. Reuse reduces the time and effort required for testing and facilitates the use of existing interfaces. At the same time, responsibilities can be clearly defined.
These are great advantages - wouldn't you agree? But experience shows us that what is taken for granted in house building is not true in the IT world. In many companies, IT is growing and changing faster than the regulatory authorities can keep up with them. The consequences are these:
- System failures or disruptions (crashes, incorrect data, malfunctions)
- Costly adaptations
- “Unexpected” problems
- The loss of the ability to actively design and change IT systems ("bug wave"), and
- Rising costs and frustrated staff.
In our opinion, it doesn't have to be this way!
IT security architecture creates order
Fortunately, alongside the divisive forces, there are also the ordering forces that form the basis of an appropriate IT security architecture. To put it bluntly, we believe that IT security architecture should also mean "creating order".
Within enterprise architecture, there are different sub-areas. Below you will find an overview of the most well-known representatives. These partial architectures affect the enterprise IT security architecture and vice versa.
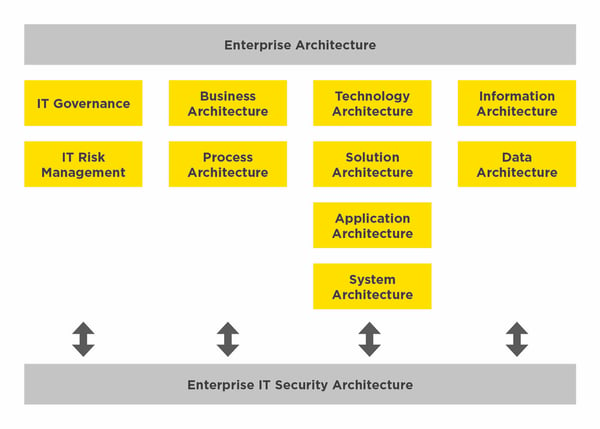
We will be happy to show you in detail in another blog post how you can find an appropriate IT security architecture. What I mean is: in a house construction project, at the start the final water or electricity connections are not set in stone, and in just the same way, it is also indispensable to plan the IT security architecture from the rough draft to the detailed version. In our experience, this is the only way to get such a project "off the ground".
If you want to find out more about IT security architecture, don't miss out on our other blog articles! Soon we will have an whitepaper on IT security architecture ready for you. What are you waiting for? Subscribe to our blog updates and stay up-to-date.
Enterprise IT Security Architecture by InfoGuard
Don't be afraid. We won't let you down. We already assist numerous companies and organisations in the planning and implementation of structured, coordinated activities to ensure cyber security in the enterprise architecture.
Put your trust in our architects. We will help you to build a needs-based enterprise IT security architecture that offers you an optimal basis for all your digitisation projects.
And before I forget: The correct answers are 1b, 2c, 3a, and 4b. Of course, these apply both to house construction and to your IT security architecture.
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant


