InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Crypto agility puts IT Architecture in the Spotlight

The hedgehogs of Leaf Mound plc have enjoyed many years of success, mainly thanks to the consistent implementation of their “buy before make” strategy. This is also due to the responsible approach of the IT architecture team, which always endeavours to ensure that the IT environment remains stable and the systems function smoothly.
Ms. Spiny (CEO) has recently been reading exciting articles from the world of IT security over the Easter holidays. While she was enjoying the right ear of her third chocolate Easter bunny, a piece about “crypto agility” that discussed the upcoming “Q-Day” really stood out to her. You can either read the whole article or a summary of what she read:
Crypto agility definition
Crypto agility describes the ability to react quickly and flexibly to changing cryptographic requirements. It focuses on the visibility and processes relating to an organisation’s crypto assets.
Crypto agility requires transparency about the use of cryptography in an organisation (e.g. protocols, libraries, cryptographic algorithms and certificates, etc.) and the ability to identify and resolve problems swiftly. An organisation that has implemented crypto agility can replace obsolete crypto assets without significantly affecting the existing system infrastructure. We’ve already reported on this in more detail in a separate blog article.
Q-Day
“Q-Day” is the day on which a powerful quantum computer will be able to crack conventional cryptographic algorithms.
By this point at the latest, the vulnerable cryptographic algorithms must be replaced by algorithms that are resistant to quantum cryptography, because otherwise the bad guys will “exploit” the computing power of quantum computers to their own ends. The article didn’t say when the Q-Day would be. However, the topic has spurred the CEO into action...
Leaf Mound plc gets moving
You guessed it: at the next IT stand-up meeting of the manager-hedgehogs, Ms. Spiny (CEO) wanted to know how Leaf Mound plc is positioned in terms of crypto agility – in other words, how the crypto assets at Leaf Mound plc. could be substituted.
Mr. Mealworm (CISO of Leaf Mound plc) pricked up his ears. With a shudder, he recalled unscheduled weekend operations needed to quickly patch an actively exploited vulnerability and keep Leaf Mound plc’s customers abreast of the progress of the patching work. That was very unpleasant every time.
He proceeded as follows:
| Challenge | Solved by |
| Identifying affected components |
|
| Finding owners of the components | Inquiring (and ascertaining) |
| Fix the vulnerability |
Depending on the situation:
|
| Testing and deploying |
Manual testing of all systems and deployment of patches or configuration modifications. |
| Preparing customer communication |
Finding the affected customers by surveying all contacts across all departments. |
Table 1 “Vulnerability patching” procedure
Every CISO knows these challenges. Lists are drawn up that serve as the basis for the next “hot mission”. Because the information is not updated, it quickly loses its relevance and usefulness. And the ad-hoc exercises start all over again with the next vulnerability...
Key management processes
The CISO also feels the squeeze in another area: key management. The standard processes for key management include generating, saving, renewing and cancelling keys. These processes aren’t only critical for safety reasons: if they’re not executed correctly, inappropriate keys prevent the operation of applications and lead to data loss in the worst case.
Based on the NIST key management document, Mr Mealworm created a drawing for Leaf Mound plc’s internal key management policy:
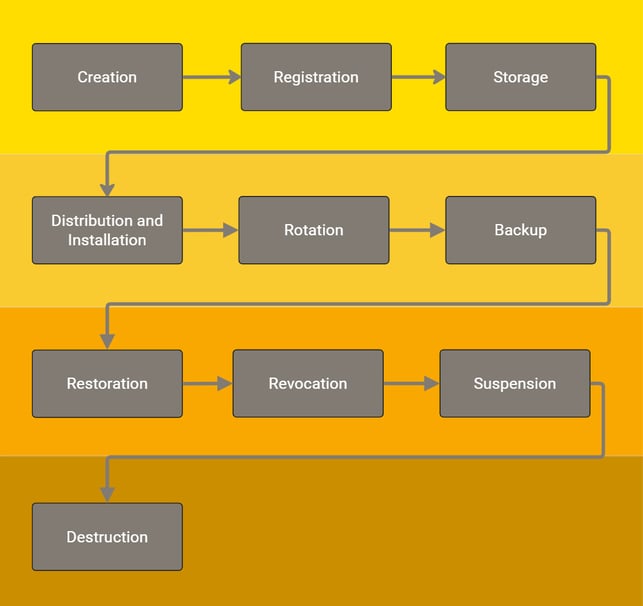 Figure 1: Internal key management of Leaf Mound plc
Figure 1: Internal key management of Leaf Mound plc
The manual processes cost the CISO and IT team a lot of time – quite apart from the fact that there’s no reliable information about the keys, cryptographic algorithms and applications.
The architect enters the scene
Ms. Wagglenose, the IT architect at Leaf Mound plc, makes an appearance at the management meeting. She refers to the CISO’s experience and explains that updating lists is not enough. For a long-term solution, the procedure needs to be standardised and the field of cryptography analysed.
Ms. Wagglenose mentions the following points:
| Steps | Measures | Examples |
| Gain understanding |
Understand the requirements of business, compliance and IT. Develop requirements for the crypto assets. |
How must data with a specific protection requirement be encrypted? Keys must be rotated automatically. |
| Recognise contexts |
Develop an overview of the crypto assets in the company and their context. |
Applications store data in an encrypted fileshare or blob. |
| Group cryptographic use cases |
Identify the various uses of crypto assets. |
Obtain certificates via an internal or external PKI. |
| Define use cases |
The corresponding use cases are defined for the identified application purposes. |
USupport for key management processes, e.g. automatic generation of a certificate or keys. |
Table 2 Analsysis steps
The first step is therefore to gain knowledge of how Leaf Mound plc’s IT is set up with regard to crypto assets. The keywords are “detection” and “inventor”. Ms. Wagglenose has more to say about this than you might think....
Detection and inventory
The aim of detection is to find all crypto assets. The information is then updated in the crypto inventory. The crypto inventory can be based on a conventional inventory solution. Key here is that its data model is expandable.
The following crypto assets are of interest to Leaf Mound plc:
- Cryptographic secrets
- Devices with a cryptography function
- Storage location of secrets
- Implementation of cryptographic algorithms, cryptography libraries
- Protocols for cryptography
- Cryptographic algorithms used
The crypto assets mentioned are analysed in more detail below.
How easily detectable are cryptographic secrets
Cryptographic secrets are more than just keys, as the following list shows. Some secrets are “volatile” and therefore difficult or impossible to detect.
| Cryptographic secret |
Explanation |
Persistent storage and thus detectable |
| Certificate |
Authenticates the public key associated with a private key. |
Yes |
| Symmetrical key |
Encrypts and decrypts data with the same key, therefore “symmetrical”. |
Yes |
| Shared key |
Two parties share a key. |
Pre-Shared keys: Yes |
| Password |
A password is usually stored as a hash. |
Yes |
| Message authentication code MAC |
Ensures the authenticity of a message by means of an algorithm and a key. |
No |
| Random number generation |
Creation of unpredictable random numbers. |
No |
| One-time password |
Randomly created, single-use passwords. |
No |
| Biometrics |
Biometric characteristics of a person. |
Yes |
Table 3 Cryptographic secrets
When asked what information regarding the keys might be relevant, Ms. Wagglenose draws a list on the whiteboard in the meeting room:
- Cryptographic algorithm
- Length of keys
- Creation date
- Expiration date
- Version no. (e.g. for rotated keys)
- Key status (not active, active, suspended, compromised, expired)
Cryptographic devices
It helps to know what you’re looking for. There’s a whole range of cryptographic devices that are part of our crypto ecosystem:
| Device | Description | Purpose | Detection possible |
|
HSM
|
Hardware security module
|
|
Yes
|
|
Hardware encryption
|
Encryption of a connection.
|
Connects one or more endpoints via an encrypted connection.
|
Yes
|
|
Smart card dongle
|
|
Authentication, signing, transaction security.
|
Difficult as mobile device.
|
|
Trusted plattform module (TPM)
|
Keys and certificates are securely stored in the TPM, which are used to perform cryptographic functions.
TPMs are classified according to security levels in the FIPS standard.
Cheaper devices can emulate the functionality of the crypto chip in software.
|
Secure system startup. Capable of various cryptographic algorithms. |
Yes
|
|
Crypto chip
|
Specialised chips such as those frequently used in IoT devices.
|
Offloading of cryptography for performance reasons.
|
Only if the device is connected to the network and allows access to the configuration.
|
Table 4 Cryptographic devices
Storage location of secrets
The way in which secrets are stored has a significant influence on the security of the cryptography used, so storage location must also be recorded in the crypto inventory.
| Storage location | Explanation |
|
Hardware security module (HSM)
|
Keys are generated within the HSM and do not normally go beyond it.
|
|
In key stores
|
Key stores such as the Java Key Store are files in which secrets are stored. The Java Key Store can be protected with a password. Enhanced protection is possible by assigning file-system access rights.
|
|
Plugable devices
|
Secrets can also be stored in plug-in devices or smartcards. Secrets may be, for example, a certificate and the associated private key or biometrics.
|
|
In the head
|
The secret is often stored in a user’s head.
|
|
In the source code
|
This should not be the case, but it does happen. E.g. for establishing a connection to the database.
|
|
In password managers
|
Any number of secrets can be stored in password managers.
|
Table 5 Storage location of secrets
Implementation of cryptographic algorithms
Cryptographic algorithms can be implemented by developers in different ways.
| Implementation with | Explanation |
|
Library
|
A cryptographic library is used.
Representative of cryptographic libraries:
|
|
In the application code
|
Cryptographic functions can be implemented in the application code itself.
|
|
API
|
Local API calls to a library or remote calls to a cryptographic service.
|
Table 6 Implementation locations of cryptographic algorithms
Protocols for cryptography
There are cryptographic protocols for different needs. Protocols can be detected by analysing the network traffic, which itself provides a good overview of the protocols. Here are some representatives:
| Protocol |
Explanation |
|
Internet protocol security
IPSec / Internet key exchange (IKE) |
Allows a virtual private network (VPN) connection.
|
|
Kerberos
|
Protocol for authentication that is used in the Unix and Windows environment.
|
|
Point-to-point protocol (PPP)
|
Layer 2 Protocol for authentication and encryption.
|
|
Secure shell (SSH)
|
Remote Login and execution of commands on a remote host.
|
|
Transport layer security (TLS)
|
Secure communication via a network.
|
|
Key management interface protocol (KMIP)
|
A protocol for managing keys and performing cryptographic operations. KMIP will be discussed in more detail second blog.
|
Table 7 Protocols in the area of cryptography
Data collection
Ms. Spiny, the CEO, thinks that’s all well and good. However, she can’t imagine how this information could be obtained automatically at Leaf Mound plc.
The architect explains that there are two options for collecting information: scanning and agents. There are pros and cons to both, which she summarises here:
| Criterion |
Scanning |
Agent |
|
Easy to handle
|
Scanning only requires the scan server and an open network connection to the target.
|
Agents are installed on the target system.
|
|
Information obtained
|
Information can be obtained that is available via the network (with or without login).
|
The agent provides a deep insight into the target system.
|
|
Areas of application
|
|
In-depth analysis.
|
Table 8 Scanning vs. agents
Five reasons in favour of the crypto agility approach
It is now clearer that there is plenty of information about crypto assets. But the final question remains: what’s the point of all this?
Practical benefit 1: risk assessment
The information obtained can be used to determine risk, enabling new vulnerabilities to be prioritised for remediation based on the assigned vulnerability.
Ms. Wagglenose shows a (very) pragmatic formula for determining risk based on the information obtained. categorisation is based on a scale 1-4 for the values low, medium, high and very high.
| Influencing factor | Examples |
|
Protection requirements of an asset
|
Protection requirements of an asset:
|
|
Dependent systems
|
Connections to other assets (systems):
|
|
Severity of the vulnerability
|
CVE, information from relevant sources.
|
|
Exposure (vulnerability)
|
Accessibility of a system for an attacker.
|
Table 9 Influencing factors for risk assessment
Here are a few examples to illustrate this. The values were quantified according to the above scheme.
| Asset | Protection requirements of the asset | Dependent systems | Severity of the vulnerability | Exposure (vulnerability) | Points (vulnerability) |
| AD |
4 |
4 |
2 |
3 |
96 |
| Customer DB |
4 |
1 |
1 |
2 |
8 |
| JIRA |
2 |
3 |
4 |
1 |
24 |
| Open SSL Library |
4 |
4 |
4 |
4 |
256 |
Table 10 Examples risk assessment
Practical benefit 2: queries and compliance
Queries from the crypto inventory can provide information about:
- Outdated or weak cryptographic algorithms
- Obsolete libraries
- Rotation requirement for keys
- Storage locations of secrets
Practical benefit 3: key management
Information about cryptographic secrets makes key management easier by providing relevant information, e.g. about the keys used.
Practical benefit 4: patching
The information in the crypto inventory is a good basis for patching. The cryptographic attributes of the relevant components are stored in it. Queries such as “Show all systems on which MD5 is used as a hash algorithm” enable migration to a current algorithm.
Do you remember how Mr. Mealworm went through his list for the “hot mission”? He pondered that if Leaf Mound plc had a crypto inventory, the work steps would be as follows:
| Procedural step | With cryptographic inventory |
|
Identifying affected components.
|
Consult cryptographic inventory. |
|
Finding owners of the components.
|
Check the cryptographic inventory. |
|
Fix the vulnerability
|
Decentralised depending on vulnerability:
Centralised:
|
|
Testing and deploying
|
Manual testing and deployment of patches or configuration adjustments.
|
|
Preparing customer communication
|
Generate reports from the crypto agility solution.
|
Table 11 Procedural steps with crypto inventory
Practical benefit 5: crypto bill of material
As a manufacturer of mobile leaf mounds and hedgehog houses, Leaf Mound plc must comply with EU legislation for exports to the EU. The Leaf Mound products transmit telemetric data such as location, temperature and operating hours to Leaf Mound plc. Mr Mealworm quotes from the proposal for a regulation of the European Parliament and of the Council on cybersecurity requirements:
Article 2, Scope (1):
“This Regulation applies to products with digital elements whose intended or reasonably foreseeable use includes a direct or indirect logical or physical data connection to a device or network.”
He continues by saying that the crypto bill of material CBOM is an extension of the software bill of material (SBOM) concept. It maintains software BOMs, which are a formal record of the details and supply chain relationships of the components contained in the software elements of a product with digital elements.
Finally, Mr. Mealworm explains the reference to cyber security, which can be seen in the recitals of the regulation: “In order to facilitate vulnerability analysis, manufacturers should identify and document components contained in the products with digital elements, including by drawing up a software bill of materials. A software bill of materials can provide those who manufacture, purchase, and operate software with information that enhances their understanding of the supply chain, which has multiple benefits, most notably it helps manufacturers and users to track known newly emerged vulnerabilities and risks. It is of particular importance for manufacturers to ensure that their products do not contain vulnerable components developed by third parties.”
Crypto agility as an opportunity
The manager-hedgehogs believe that crypto agility is a sound approach. Mr. Mealworm (CISO) and Ms. Wagglenose don’t always see eye to eye, and the CISO considers this to be an opportunity to make his work easier in future and avoid stressful remediation measures. The only steps everyone would like to see simplified are those involving “fixing the vulnerability” and “testing and deploying”. They decide to keep an eye on measures in this regard as a pending issue. In addition, the key management process should be automated to a greater extent because the CISO team at Leaf Mound plc is still spending too much time replacing keys and certificates.
This is no cause for concern for the manager-hedgehogs: they already have a few ideas for optimisation on this topic. In a further step, the hedgehogs are tackling the topic of crypto-agility-“ready” architecture and automation.
Find out how the hedgehogs at Leaf Mound plc are tackling this challenge in the second part of this blog series.
Are you interested in making your IT infrastructure cryptographically agile and taking it to the next level of security? We’ll be happy to assist you in mastering the many challenges of crypto agility together.
Our approach includes a thorough analysis of your existing architecture, with a particular focus on crypto-agility-readiness. We work with you to develop a detailed profile of your strengths and weaknesses. Based on the cryptographic inventory, we identify development and optimisation opportunities so that you can complete the transition towards crypto agility step by step. Ultimately, our goal is to integrate your IT architecture into the cyber landscape in a secure and strengthened manner.
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first


