Career 15 Vacancies 250+ Employees
Career 15 Vacancies 250+ Employees
InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
CISOs in the eye of the storm due to a security incident

A cyber attack can affect any company. Just like with a storm, it is only possible to detect the precursors with the right tools (or infrastructure). We are not anticipating a decrease in the number of cyber threats – quite the opposite. The trend is for them to become increasingly acute and aggressive, and as a result, the duties of CISOs (Chief Information Security Officers) are becoming more and more and more challenging. But what do CISOs need to do in the event of a security incident? What challenges are they facing? And how do they hold their own in critical situations like this? In this article, we answer precisely these questions and shed light on what CISOs are required to do when the storm hits.
You think the comparison with the storm is a bit extreme? Well, a cyber attack can definitely be compared to being hit by a tornado. Before its full force hits you, often there is bright sunshine. Scenarios just like this play out in many companies that have (so far) failed to detect cyber attacks. The challenge of protecting intellectual property, company, customer and employee data from cyber attacks is becoming harder and harder. The damage to companies reputations and finances varies considerably depending on how quickly and efficiently the organisation can react. As the Chief Information Security Officer (CISO), you have a decisive role to play.
CISOs as key players in cyber security
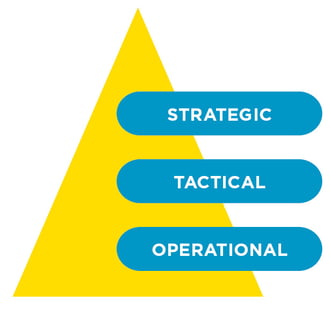 CISOs act primarily at the strategic level. On one hand, in the company, they take responsibility for the operation, strategic orientation and budget of the security measures. They also provide advice to management on security issues, current threats and issues related to meeting compliance requirements.
CISOs act primarily at the strategic level. On one hand, in the company, they take responsibility for the operation, strategic orientation and budget of the security measures. They also provide advice to management on security issues, current threats and issues related to meeting compliance requirements.
The Computer Security Incident Response Team (CSIRT) operates at the tactical level. The CSIRT is responsible for making preparations for incidents and – if necessary – for implementing a predefined incident response plan. CISOs work proactively with their team and focus on concrete prediction as well as preparation to defend against the attack.
This is one of the reasons why CISOs never stop learning. They need to be kept constantly informed about new threats and vulnerabilities, and define and implement measures that are appropriate to the risks they pose. This is a huge challenge, don't you think?
CISOs' strategic and tactical area of responsibility
CISOs have numerous tasks to deal with at a strategic and tactical level in the event of a potential incident. These tasks range from assisting the management and the board of directors, for example in defining and updating the cyber security policy. This also includes advice on all issues relating to cyber resilience and support in resolving conflicting aims, for instance cost efficiency vs. cyber security measures. CISOs have an active involvement in cyber risk management, creating guidelines for organisational cyber resilience and, of course, monitoring compliance. Ensuring cyber resilience is not a one-off event, so CISOs are also concerned with continuously improving the corresponding processes.
Do you actually know the state of your cyber resilience? You can get the answer with our free checklist. Download it now!
However, this is by no means the entire area of responsibility. CISOs are the lynchpin, acting as a central contact point for all questions relating to cyber resilience. Of course, they also provide support in drawing up and updating emergency plans in the event of a security incident. At the same time, they also deal with the current threat situation and regularly inform senior management about the status of cyber security. For example, this status report includes an assessment of the cyber security situation as compared to previous reports, information about cyber security projects, cyber incidents and the results of penetration tests and other audits. This also includes managing and coordinating measures to raise awareness of cyber security and awareness training (with the keyword security awareness). You can find out about all the other jobs that land on their desks in our comprehensive task list!
The role played by the board of directors and the senior management should not be forgotten either. After all, they have to ensure that a senior manager is responsible for defining and implementing the cyber security strategy at the corporate level. Here, the management needs to be independent, have the right balance of skills, knowledge and experience, as well as adequate resources and direct access to senior management and the board of directors.
The independence of CISOs – an important point
In terms of organisation and procedure, CISOs must be independent to avoid any potential conflict of interest. For this reason, we recommend that the following measures in particular be implemented:
- Organisational corporate set-up to ensure that CISOs can act independently of the IT/operations department and can report directly to senior management. Furthermore, care must be taken to ensure that they are not involved in internal auditing.
- Definition of the resources required.
- Setting a fixed budget for training the IT staff in cyber security and for raising the awareness of the rest of the staff (including the management) about security awareness.
- Obligation of all IT department staff and IT service providers to report all related incidents, as per the escalation procedure.
The role and duties of CISOs in a security incident
In principle, all security incidents must be reported to the CISO. A preliminary analysis of the incident is then conducted to establish whether it is warranted to activate the CSIRT. We illustrate one possible reaction process, using the example of an unintentional data outflow, below. This may include the following steps, depending on the company and its size:
- The first step is for the CISO to carry out a preliminary analysis of the facts, based on the notification from the user or the Help/Service Desk. This is then used to assess the situation to establish the nature and extent of the incident.
- In the second step, the CFO and DPO (Data Protection Officer) are informed of the potential breach of data protection, including all relevant information about the situation.
- Contact is then made with the user who reported the incident.
- The CISO now has to identify the systems and the type(s) of information affected. It is also necessary to establish whether the incident could be a (suspected) breach of personal data or critical assets. The type of breach involved is important, as not every breach demands the intervention of the entire CSIRT. For example, an investigation of the physical data outflow in paper form or via theft does not warrant the involvement of system and firewall administrators or other technical staff.
- As a next step, the CISO needs to discuss the preliminary details with the DPO(s). The following issues are central to this process:
- If there is an infringement of data protection, which includes personal data, then activation of the CSIRT is necessary.
- It is the job of the CISO is to inform the PR department about the details of the breach and the current status of information. The PR department must always be kept updated about the key events of the investigation.
- The CSIRT is also responsible for ensuring that all of the details of an incident are documented to assist their communication to senior management and other parties when required.
- The CISO or CSIRT leadership is responsible for coordinating all CSIRT activities. This specifically includes involving the appropriate members of the CSIRT and the first level escalation team.
- The CISO also has responsibility for identifying and contacting the data owners who are affected by the breach. The CISO, DPO and the data owners must define additional reporting obligations (e.g. human resources, external parties) in coordination with the CFO and the management.
- If the breach occurred on a third party's site, it has to be checked whether there is a legally valid contract. Collaborating with the parties who are responsible for the contract, the CISO, the DPO and the data owners will review the terms of the contract and decide how to proceed. This usually involves the following steps:
- Identify the likely extent of the potential harm. This includes all the stored and compromised data as well as the number of affected persons.
- Identify what kinds of personal data are at risk - including but not limited to: name, address, pension / social security number, bank account number, cardholder, card holder's address, medical and health-related information, etc.
- Where personal data is involved, the data owners are to identify who may be affected. The next steps, including the following, will be taken jointly with the CSIRT in consultation with the CISO or CISO, the CSIRT, CFO, administration and the PR department:
- Identifying where and how the breach occurred
- Identify the source and time frame of exposure
- Check the infrastructure for vulnerable or affected systems
- Check the system logs and audit logs
- Check directory and file permissions
- Document the Internet Protocol (IP) addresses, operating systems, domain names, system names, and other relevant system information
- In coordination with the CSIRT leader, it is also the CISO's responsibility to take measures to contain and control the incident. The following options are possible:
- Shutting down certain applications or connections to third party providers
- Re-configuring firewalls
- Changing computer access codes
- Changing physical access controls
- Changing all passwords, including system processes and privileged users (repeatedly if necessary)
- Isolating those systems affected without switching them off, disconnecting from the network (e.g. network cable), changing the Service Set Identifier (SSID) at the access point (AP)
- Also, in coordination with the CSIRT leadership, the CISO is responsible for monitoring the systems and network for signs of an ongoing attack
- Evidence must be preserved, where appropriate, to ensure that prosecution can proceed.
- The CSIRT must also prepare a synthesis of the results and the measures taken.
- In the case of credit cardholder data, the requirements of the PCI DSS standard must be respected.
- Where an internal user is responsible for the breach, disciplinary action may need to be coordinated with human resources.
- Where an external user was responsible for the breach, the service contract needs to be reviewed.
CISO-as-a-Service is a worthwhile option for every company
As you can see, CISOs are rarely bored. That's why gartner's market research experts recommend that companies employing 150 or more staff should assign an internal or external resource to the CISO or CSO position.
Does your company lack the internal resources to fill the CISO position with an expert? We can undertake these duties within the framework of a mandate (CISO-as-a-Service). This way you can benefit from our experts' experience and comprehensive knowledge in the fields of technology, organisation, compliance and audits. Together with you, we will define the specific area of responsibility and provide you with the right specialists. Sounds interesting? Then we look forward to your inquiry!
Blog

Zero Trust Maturity Model 2.0: Reifegradmodell auf 5 strategischen Säulen

SWIFT CSCF v2025 erhöht den Druck: Nur cyberresilient ist compliant




