InfoGuard AG (Headquarter)
Lindenstrasse 10
6340 Baar
Switzerland
InfoGuard AG
Stauffacherstrasse 141
3014 Bern
Switzerland
InfoGuard Com-Sys GmbH
Frankfurter Straße 233
63263 Neu-Isenburg
Germany
InfoGuard Deutschland GmbH
Landsberger Straße 302
80687 Munich
Germany
InfoGuard Com-Sys GmbH
Am Gierath 20A
40885 Ratingen
Germany
InfoGuard GmbH
Kohlmarkt 8-10
1010 Vienna
Austria
Are you ready for the new FINMA circular 2023/1 “Operational risks and resilience – Banks”?

The completely revised FINMA Circular 2023/1 on management of operational risks and ensuring resilience in banks and the reworked FINMA Circular 2013/3 on auditing come into effect as of 1 January 2024. The new FINMA Circular 2023/1 replaces the previous edition, 2002/21 “Operational risk – Banks”. This article provides the most important information about the new features and the expectations for financial institutions (banks, investment firms, finance groups and conglomerates).
FINMA Circular 2013/1 “Operational risks and resilience – Banks”
In March 2021, the Basel Committee on Banking Supervision (BCBS) published the new Principles for Operational Resilience (POR) and the revised Principles for the Sound Management of Operational Risk (PSMOR). These principles should give financial institutions the ability to bettercope with operational threats. The publication of the above principles triggered a complete overhaul of the FINMA Circular which comes into effect as at 1 January 2024.
FINMA Circular 2013/3 “Auditing”
Based on the changes in FINMA Circular 2023/1, the FINMA Circular 2013/3 “Auditing” was also amended as follows:
New- Internal organisation and internal control system: Gradual coverage of topics over six years with an auditing depth at the discretion of the auditing company.
- Management of information and communication technology risks (ICT risks): Gradual coverage of topics over four years with an auditing depth at the discretion of the auditing company.
- Applications to FINMA for a reduce audit interval in accordance with RZ 150 from the last circular.
Next, we can gain an overview of the total of eight principles of the new circular. In general, the principles apply to all addressees of the circular. However, in individual cases these depend on the size, complexity, structure and risk profile of the bank. The principle of proportionality applies. The eight major principles are summarised as follows:
1. Comprehensive management of operational risks (Rz 22-46)
- Specification of the responsibilities of the board of directors and the executive managers with respect to the management and monitoring of operational risks (ICT risks, cyber risks, risks relating to critical data, BCM risks), the approval of risk tolerances (annual) and the strategies, governance and reinforcement of awareness on the handling of operational risks
- Regular implementation of audit and mitigation measures, including by independent auditors
- Separation of roles, expertise and responsibilities to ensure independence and prevent conflicts of interests
- Reporting on risk controls at least once a year to the board of directors and every six months to the management
2. Comprehensive management of ICT risks (Rz 47-60)
Guaranteeing suitable processes, procedures, responsibilities and resources:
- for implementation of the ICT strategy and governance
- for change management
- for ICT operation, including keeping an inventory of ICT assets (hardware, software, location of critical data)
- for incident management
3. Management of cyber risks (Rz 61-70)
Guaranteeing suitable processes, procedures, responsibilities and resources:
- to identify institution-specific potential threats, to protect the inventoried ICT assets, to detect and record cyber attacks and to react and ensure prompt restoration after a cyber attack.
- to carry out regular vulnerability analyses, penetration tests and cyber exercise (e.g. table top exercise, red teaming exercises, etc.)
- Ensuring compliance with FINMAG reporting obligations: The initial assessment and the pre-orientation must be submitted to the relevant office at FINMA within 24 hours. There is a time window of 72 hours for the subsequent notification in accordance for the requirement catalogue in the EHP investigation platform (mandatory fields).
4. Management of critical data risks (Rz 71-82)
- Guaranteeing suitable processes, procedures, responsibilities and resources for the handling and protection of critical data1
- Commissioning a unit to ensure the confidentiality, availability and integrity of critical data
- Carrying out due diligence in the selection of service-providers processing critical data
5. Business Continuity Management (BCM) (Rz 83 – 96)
- Identification of critical business processes in line with Business Impact Analyses (BIA), definition of Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) and production of at least one Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP)
- BIA and BCP amended at least every year and in the event of major changes
- Putting together a crisis team for crisis management and definition of a communication strategy
- Regular checking of BCPs and DRPs and reporting to the board of directors and the management about activities carried out and results.
- Regular training of the employees and members of the crisis team with respect to their roles, expertise and responsibilities (RER).
6. Management of risks from international service business (Rz 97-100)
- Analysis of the legal framework conditions and the resulting risks for the international service business
- Definition and implementation of strategic and organisational risk mitigation measures
7. Guaranteeing operational resilience (Rz 101-111)
- Identification of critical functions and their tolerance to interruption and definition and implementation of measures to guarantee operational resilience
- Reporting on operational resilience to the board of directors and the management at least once a year
- Inventorying critical company functions with regular (at least once a year) checking and updating
- Regular testing of critical functions within their interruption tolerances based on scenarios
8. Transition periods
- Before entry into force: Fulfilment of the equity capital requirements for operational risks in accordance with the revised ERV (Revision pack “Basel III final”) and the related FINMA Regulation (in accordance with Rz 2 - 116 of the FINMA Circular 2008/21 “Operational risks – Banks”)
- After entry into force: Identification of critical functions, definition of interruption tolerances and initial permissions (Rz 101 and 103) plus an initial report (Rz 105)
- Within 1 year after entry into force: Fulfilment of the requirements (Rz 106 - 109) and first tests of operational resilience (Rz 110)
- Within 2 years after entry into force: Guaranteeing operational resilience (Rz 102) and fulfilment of requirements in accordance with Rz 104 and 111
Conclusions on the new FINMA Circular 2023/1 “Operational risks and resilience – Banks”
The new FINMA Circular 2023/1 defines important requirements for financial institutions, some of which are new. The new requirements focus in particular on the management of risks relating to critical data (not only customer data), the management of ICT risks, the establishment of an appropriate Business Continuity Management system and guaranteeing operational resilience.
FINMA Circular 2023/1 - the management of operational risks - also specifies the responsibilities of the board of directors and the management. In terms of the requirements, it should be noted that there are relaxations for banks and investment firms in supervisory category 4 and 5 and for banks classed as small banks and investment firms which do not hold accounts.
An important tool for efficient and effective management of (operational) risks involves dividing the roles, expertise and responsibilities (RER) into different lines of defence:
First line of defence
The first line of defence lies with the business and process officers. The operative management is responsible for the maintenance of effective internal controls and carrying out risk and check processes during everyday business. This includes identification and assessment of controls and reduction of risks. The business and process officers are also responsible for the development and implementation of internal guidelines and procedures. They make sure that the activities tally with the organisational objectives.
Second line of defence
The second line of defence supports the management in order to ensure that the risks and controls are being properly managed. The management sets up different risk management and compliance functions in order to support the structure and/or the monitoring of the controls in the first line of defence. The second line of defence fulfils an important purpose but cannot be completely independent because of its management function.
Third line of defence
The third line of defence gives the management and the board of directors the peace of mind that the efforts of the first two lines comply with the business objectives. The main difference between the third line of defence and the first two is the high degree of organisational independence and objectivity. Internal auditing cannot arrange or implement processes, but it can give advice and recommendations on processes. Internal auditing can also support the company’s risk management system, but it can only implement or execute risk management within its own function. Internal auditing achieves its objectives by means of a systematic approach to evaluating and improving the effectiveness of the risk management, control and governance processes.
External auditors
External auditors are responsible for submitting an assessment on the orderliness (correctness within a specific degree of significance) of the annual reports in compliance with specific accounting standards. External auditors can also provide guarantees on compliance with institutional regulations to the regulatory body.
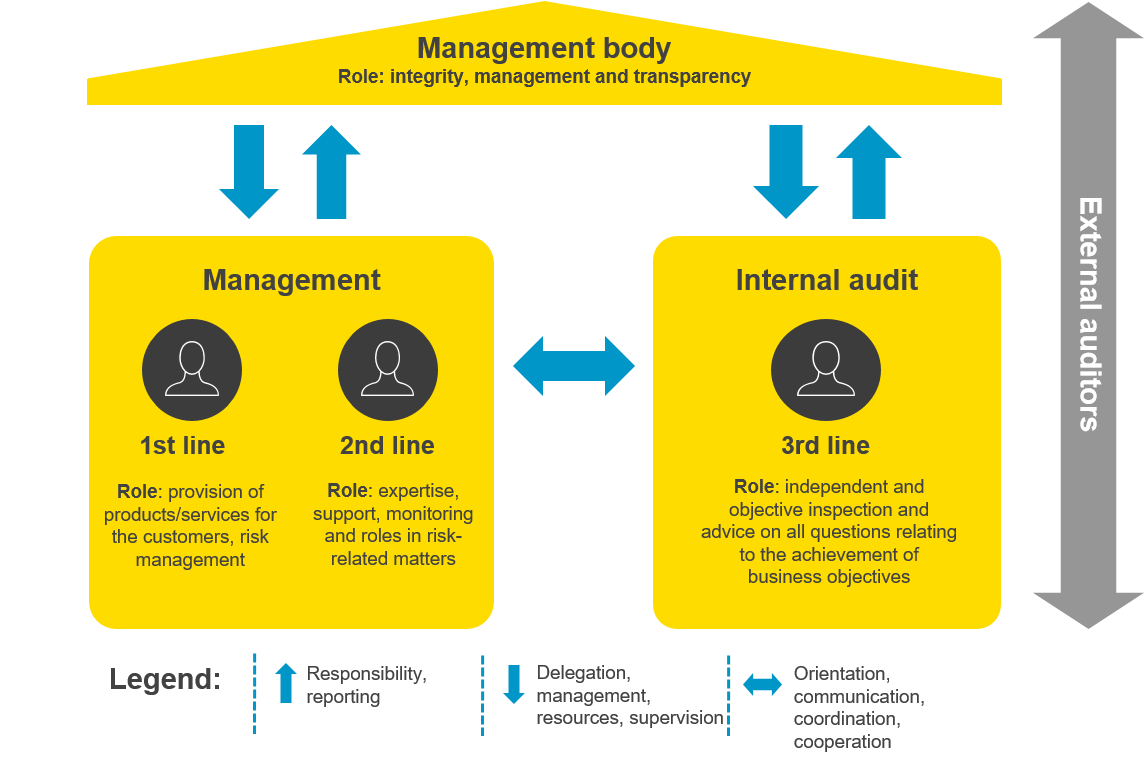
The IIA Three Line Model (Source: The Institute of Internal Auditors)
For some financial institutions, there is a lot of catching-up to do in order to meet the transition periods. While the entry into force as at 1 January 2024 incorporates transition periods of up to two years, financial institutions are well advised to get to grips with the new requirements as soon as possible in order to guarantee appropriate compliance within the deadlines.
Financial institutions which have already implemented best practice standards in risk and business continuity management should be looking at a more manageable outlay. FINMA Circular 2023/1 specifies the responsibilities of the board of directors and the management and requires coordination and communication.
How are things looking for you?
-
In your company, are the responsibilities with respect to the handling of operational risks adequately clear and defined?
-
Have the threat scenarios for your company been identified and formulated?
-
Do you carry out regular analyses of operational risks?
-
Have you defined and implemented processes for change management, ICT operational management, incident management, etc.?
-
Do you carry out regular vulnerability analyses, penetration tests and cyber practices (e.g. table top exercise, red teaming exercises, etc.)?
-
Is there a BCM strategy identifying critical business processes in your company in line with Business Impact
-
Analyses (BIA), have you defined Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) and drawn up Business Continuity Plans (BCP) and Disaster Recovery Plans (DRP)?
-
Do you test the critical functions regularly in line with their interruption tolerances?
-
Do you provide your employees with regular training on their responsibilities in handling cyber risks?
-
etc.
Thanks to our many years of proven experience in security consultancy, we are happy to support you on ensuring compliance with the new FINMA Circular 2023/1.
1 Critical data is data which is of such significance given the size, complexity, structure, risk profile and business model of the institution that it requires increased security. This is data that is critical to the successful, lasting provision of the services by the institute or for regulatory purposes. Confidentiality, integrity and availability must all be considered when assessing and determining the criticality of data. Each of these three aspects can be key in determining whether data is classified as critical (Source: FINMA Circular 2023/1).
Blog

Agentische KI im Angriff: Wie Human-AI-Teaming die Cyberabwehr neu ausrichtet

Zero Trust 2026: Diese 4 Schritte funktionieren in IT, OT & Cloud-first


